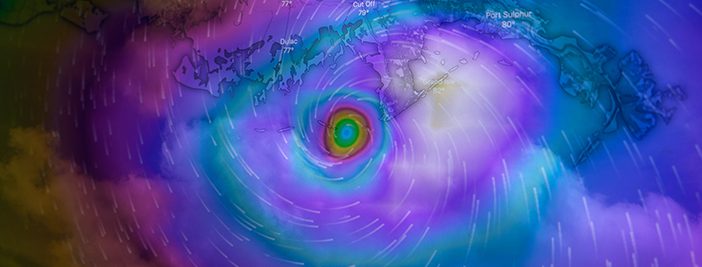
The National Oceanic and Atmospheric Administration (NOAA) is predicting a ‘near-normal’ hurricane season for 2023. That means there could be 5-9 hurricanes and 1-4 major hurricanes through November 30th. They are 70% confident in these predictions and are implementing a series of upgrades and improvements as they expand their operational supercomputing system by 20%.
The increase in computing capability means they can roll out the Hurricane Analysis and Forecast System (HAFS), which shows a 10-15% improvement in track forecasts over existing models. It also means the Probabilistic Storm Surge model gets an upgrade that allows it to run 2 storms simultaneously, and the Weather Prediction Center is extending the Excessive Rainfall Outlook by 2 days, which means it can provide forecasts up to 5 days in advance and warn areas prone to flash flooding.
With these advancements and others still to come, NOAA aims to provide communities with the earliest and most accurate forecasts for planning and safety. What business owners need to do then is be prepared to act. Here are 5 things you can do today:
- Visit CEMA’s website at chathamemergency.org to sign up for alerts and take advantage of the free Ready Business toolkits and resources they offer.
- Review your insurance coverage. Make sure you are covered for everything you think you are, and consider business interruption insurance and cybersecurity insurance as well if you do not already have it. Hurricanes are only one kind of disaster.
- Check on your backups. Talk to your IT services provider to make sure your data is being backed up as frequently as you need it, that it’s being stored in multiple, unconnected sites, and that it’s being tested. You don’t want to assume this and find out after you’ve lost everything that it wasn’t the case.
- Update your communication plan. This can be as simple as checking the employee names and numbers you have to make sure they’re current or as complicated as laying out the official company channels and SOPs for staying in touch during an evacuation.
- Schedule a drill. You don’t have to hold a disaster drill today, but you should get your leadership team together and put one on the calendar. Plans always look good on paper, but disasters rarely go according to plan. Running through a drill can show any weak spots and make your entire team more comfortable with what to do in an emergency.
There is plenty of more detailed, thorough disaster planning that can benefit your business, but these 5 steps will put you further ahead than most, just as the NOAA’s supercomputing increase aims to do.
Contact Infinity with your business disaster planning questions and get free resources, including disaster recovery plan examples, here on our website. You can also visit ready.gov, sba.gov, and chathamemergency.org for more.
Below, find a sample A.I. generated disaster recovery plan outline that you can take and use in your business. It was generated by ChatGPT, and you can ask us for the prompt if you’d like to run your own variations.
[av_icon_box icon=’ue278′ font=’new-icons-upload’ title=’Sample Disaster Recovery Plan Outline from A.I.’ position=’left’ icon_style=” boxed=” font_color=’#de533e’ custom_title=” custom_content=” color=’custom’ custom_bg=” custom_font=’#de533e’ custom_border=’#de533e’ custom_title_size=” av-desktop-font-size-title=” av-medium-font-size-title=” av-small-font-size-title=” av-mini-font-size-title=” custom_content_size=” av-desktop-font-size=” av-medium-font-size=” av-small-font-size=” av-mini-font-size=” heading_tag=” heading_class=” link=” linktarget=” linkelement=” id=” custom_class=” template_class=” av_uid=’av-2vs95p’ sc_version=’1.0′ admin_preview_bg=”]
Here is an expanded outline of the comprehensive disaster recovery plan:
I. Introduction to the Disaster Recovery Plan
A. Purpose and Scope
– Clearly define the purpose of the plan, such as ensuring the continuity of business operations and protecting sensitive data.
– Specify the scope of the plan, including the office’s physical location, network infrastructure, and employees.
B. Objectives
– Outline the main objectives, such as minimizing downtime, safeguarding data integrity, and maintaining client trust.
C. Responsibilities and Roles
– Assign specific roles and responsibilities to key individuals involved in disaster recovery efforts, including the incident response team, IT staff, management, and employees.
II. Risk Assessment
A. Identification of Potential Disasters
1. Cybersecurity Threats
– Identify common cybersecurity risks, such as phishing attacks, malware infections, data breaches, and ransomware.
2. Hurricanes
– Assess the specific risks associated with hurricanes in Savannah, Georgia, such as high winds, storm surge, and potential flooding.
III. Cybersecurity Threats
A. Prevention Measures
1. Employee Training and Awareness
– Implement regular cybersecurity awareness programs to educate employees about common threats, social engineering tactics, and best practices.
2. Secure Network Infrastructure
– Establish robust network security measures, including firewalls, intrusion prevention systems, and virtual private networks (VPNs).
3. Strong Password Policies
– Enforce password complexity requirements, regular password changes, and the use of multifactor authentication (MFA) where applicable.
4. Regular Software Updates and Patches
– Implement a comprehensive patch management process to ensure all software and systems are up to date with the latest security patches.
5. Firewalls and Antivirus Protection
– Deploy and maintain firewall systems to monitor and filter incoming and outgoing network traffic.
– Install and update antivirus software on all devices to detect and mitigate malware threats.
6. Data Encryption
– Encrypt sensitive data both at rest and in transit using industry-standard encryption algorithms and protocols.
B. Detection and Incident Response
1. Intrusion Detection Systems
– Implement intrusion detection systems (IDS) and intrusion prevention systems (IPS) to monitor network activity and detect potential security breaches.
2. Security Incident and Event Management (SIEM)
– Utilize a SIEM solution to centralize log collection, analysis, and alerting for early detection of security incidents.
3. Incident Response Team
– Establish an incident response team consisting of trained individuals responsible for promptly responding to and mitigating security incidents.
C. Data Backup and Recovery
1. Regular Data Backups
– Conduct regular backups of critical data and ensure the backup frequency aligns with the organization’s recovery point objectives (RPO).
2. Offsite Data Storage
– Store backup data in a secure offsite location to protect against physical damage or loss.
3. Testing Data Restoration Procedures
– Regularly test the restoration process for backups to ensure the integrity and availability of data during recovery.
4. Documented Recovery Processes
– Develop documented recovery procedures that outline step-by-step instructions for restoring systems and data in the event of a cybersecurity incident.
IV. Hurricane Preparedness
A. Emergency Communication Plan
1. Communication Channels
– Establish multiple communication channels, such as email, phone, and instant messaging, to ensure effective communication during emergencies.
2. Contact Information
– Maintain an up-to-date contact list of employees, emergency services, key vendors, and clients to facilitate quick and efficient communication.
B. Evacuation Plan
1. Assembly Points
– Identify primary and secondary assembly points for employees to gather during an evacuation.
2. Transportation Arrangements
– Make arrangements for employee transportation, if necessary, to ensure their safe evacuation from the office.
C. Protection of Physical Assets
1. Securing the Office
– Implement physical security measures, such as reinforced windows and doors, to protect the office space from hurricane-related damage.
2. Safeguarding Equipment and Documents
– Develop procedures to secure and protect office equipment, important documents, and client files from potential water damage or destruction.
D. Data Protection
1. Data Backup and Offsite Storage
– Ensure regular backups of critical data and store them in an offsite location, preferably outside the hurricane risk zone.
2. Protecting Physical Storage Media
– Safeguard physical storage media, such as hard drives or tapes, in waterproof and secure containers to prevent damage.
E. Business Continuity
1. Remote Work Capabilities
– Establish remote work policies and provide employees with necessary tools and resources to continue working during the recovery phase.
2. Alternate Workspace Arrangements
– Identify alternate workspace options, such as coworking spaces or other branch offices, to ensure business operations can continue in case of office unavailability.
3. Access to Critical Systems and Applications
– Plan for remote access to critical systems and applications needed for essential business operations during the recovery phase.
V. Testing and Maintenance
A. Regular Plan Testing
– Conduct periodic tests and drills to validate the effectiveness of the disaster recovery plan and identify areas for improvement.
B. Updates and Revisions
– Regularly review and update the plan to incorporate new technologies, address emerging threats, and reflect any organizational changes.
C. Training and Awareness Programs
– Provide ongoing training and awareness programs to keep employees informed about changes to the plan and enhance their disaster recovery skills.
VI. Plan Activation and Incident Response
A. Activation Procedures
– Clearly define the criteria for activating the disaster recovery plan, such as specific events or conditions that trigger its implementation.
B. Incident Response Team Roles and Responsibilities
– Specify the roles and responsibilities of the incident response team members during a cybersecurity incident or hurricane-related emergency.
C. Communication and Reporting
– Establish communication protocols and reporting channels for notifying key stakeholders, including employees, clients, and regulatory authorities, about incidents and recovery progress.
D. Recovery Procedures
– Provide detailed step-by-step instructions for recovering systems, data, and operations in a coordinated and timely manner.
E. Post-Incident Evaluation
– Conduct a post-incident evaluation to assess the effectiveness of the disaster recovery efforts, identify areas for improvement, and incorporate lessons learned into future planning.
VII. Documentation and Distribution
A. Documented Plan
– Prepare a comprehensive document containing the disaster recovery plan, including all relevant procedures, contact information, and recovery strategies.
B. Accessible and Distributed Copies
– Ensure that copies of the disaster recovery plan are readily accessible to authorized individuals, both in physical and electronic formats, and distribute them to relevant stakeholders.
VIII. Appendix
A. Contact Information
– Maintain an up-to-date appendix with contact details for emergency services, employees, vendors, insurance providers, and other critical stakeholders.
B. Network Diagrams
– Include network diagrams and system configurations to aid in the recovery and restoration of network infrastructure.
C. Recovery Resources and Vendors
– List external resources, such as disaster recovery service providers or specialized vendors, who can assist with recovery efforts if needed.
D. Relevant Legal and Regulatory Requirements
– Document any legal or regulatory requirements that must be considered during the disaster recovery process, such as data privacy laws or industry-specific regulations.
Note: This expanded outline provies a more detailed structure for a comprehensive disaster recovery plan, covering cybersecurity threats and hurricanes. It should be customized and tailored to meet the specific needs and circumstances of your business.
[/av_icon_box]