Infographic: Q1 2022 Report
KnowBe4’s latest quarterly report on the top-clicked scam email subjects is here. They analyze the top categories, general subjects (in both the United States and globally), and ‘in the wild’ attacks.
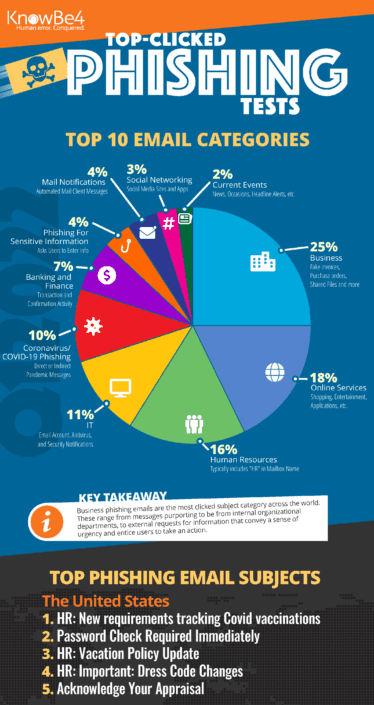
Takeaways include:
- Business scam emails remain the highest-clicked category around the world. This category contains typical communication that employees might receive. The subjects of these emails include fake invoices, purchase orders, requests for information, shared files, and more.
- Holiday-themed emails were the most tempting for employees to click on. HR-related messages such as a change in the schedule for the holidays likely piqued interest from employees to see if they would receive an extra day off or shortened work schedule due to the holidays.
- IT and online service notifications that could potentially affect users’ daily work…are effective because they cause a person to react before thinking logically about the legitimacy of the email.
1. Phony Bank Fraud
The criminals keep evolving. As we get used to apps and accounts alerting us to unusual activity, scammers try to take advantage. The FBI recently put out a Public Service Announcement warning about texts claiming bank fraud alerts that are fake.
This is how it works:
You receive a text, seemingly from your bank, alerting you that someone has attempted to initiate a money transfer on your account. It will look official, include an amount of the supposed instant payment, and ask you to respond Yes or No if it was you.
If you respond to the text, you get a call from that financial institution’s spoofed number.
The caller claims to be a representative of your bank’s fraud department. To trick you into believing they are legitimate, they may provide personal information such as your old addresses for you to confirm. Then they walk you through the steps necessary to ‘reverse’ the transaction mentioned in the initial text.
But instead of reversing anything, you’ve just sent money to the criminal’s account.
The FBI recommends the following precautions:
- Be wary of unsolicited requests to verify account information. If a call or text is received regarding possible fraud or unauthorized transfers, do not respond directly.
- If this happens to you, contact the institution’s fraud department through verified contact information on official websites or documentation, not through those provided in texts or emails.
- Enable Multi Factor Authentication (MFA) for all financial accounts, and do not provide MFA codes or passwords to anyone over the phone.
- Understand financial institutions will not ask customers to transfer funds between accounts in order to help prevent fraud.
- Be skeptical of callers that provide personally identifiable information, such as social security numbers and past addresses, as proof of their legitimacy. The proliferation of large-scale data breaches over the last decade has supplied criminals with enormous amounts of personal data, which may be used repeatedly in a variety of scams and frauds.
2. Prompt Bombing or ‘Being Annoying’ as a Social Engineering Tactic
As Multi Factor Authentication (MFA) increases in use as one of the most effective ways to help people secure their accounts, criminals are trying to find ways around it. Ars Technica, a website for technologists, reports on MFA prompt bombing as a tactic that essentially tries to annoy you into allowing access.
Methods include:
- Sending a bunch of MFA requests (texts or app notifications) and hoping the target finally accepts one to make the noise stop.
- Sending one or two prompts per day. This method often attracts less attention, but “there is still a good chance the target will accept the MFA request.”
- Calling the target, pretending to be part of the company, and telling the target they need to send an MFA request as part of a company process.
An actual member of the criminal hacking group Lapsus$ that has used this tactic gives an example of why it works for them, “No limit is placed on the amount of calls that can be made. Call the employee 100 times at 1 am while he is trying to sleep, and he will more than likely accept it. Once the employee accepts the initial call, you can access the MFA enrollment portal and enroll another device.”
How can you protect yourself?
- First, keep in mind that having any form of MFA in place is always more secure than not having it.
- If you ever get an MFA prompt that was not a result of you trying to log in yourself, call your IT team. Do not accept or allow the prompt, and change your password if you are able.
- Be cautious of unsolicited phone calls that ask you for access. If the caller tells you it’s part of the company process, tell them you need to confirm it. Then independently contact someone you know and trust at your company. Any legitimate professional will appreciate your caution.
- Remember to practice vigilance with your phone texts and notifications just as you do with your emails. For every security measure companies put in place, there will be criminals trying to undermine or smash through it.
3. Charity Scams
Experts warned us, and now we have multiple examples of scammers impersonating various charities and fundraising efforts for the people of Ukraine.
As I’ve mentioned before, most recently in March, global issues and events will always attract criminals because it turns the whole world into their potential targets.
These latest examples include:
- Texts that appear to be from legitimate charity Mercury One. Some of the texts even copy actual texts from the charity. But the links do not go to the Mercury One website. They go to spoofed sites that want your personal information and/or payments.
- Emails seeming to be from the legitimate United Help Ukraine charity that link to a convincingly spoofed site. As Bitdefender researchers describe, “The threat actors behind this campaign go way past any previous nickel-and-dime antics, impersonating the United Help Ukraine organization. Criminals are using IP addresses in the US to deliver this scam across Europe and North America. The DONATE NOW button sends recipients to a cloned version of the official United Help Ukraine Website. The fake website offers users a single donation method, and it closely resembles the official Donate page of the non-profit charitable organization.”
- A series of “help Ukraine” donation posts on webpages, in forums, and sent via email that are really a scam enticing users to send donations to counterfeit addresses. Bleeping Computer describes “attackers using a variety of means—from emails that appear to originate from npr.org or the United Nations Office for the Coordination of Humanitarian (OCHA) domains, to posting forum posts claiming to be behind the “Help Ukraine” movement.”
These tactics are disgusting, but you need to know they’re out there so you can avoid them.
So how can you stay safe from this?
- Always be suspicious of unsolicited texts or emails asking for money. Especially the heart-string-pulling emotional pleas that seem so desperate for help NOW and ‘aren’t even really asking for that much.’ If it’s not a charity you have previously donated to and signed up to be contacted by, then do not click any links. You can look them up independently and donate through legitimate channels.
- Pay particular attention when an email or text elicits an emotional reaction, and make yourself stop and think. Scammers jump into action whenever there is a crisis so they can exploit people’s generosity by clouding their judgment.
- Train yourself to carefully check the sender and link details on any unsolicited messages. Look for misspellings and numbers used in place of letters to appear to be legitimate URLs. And trust your gut if you feel like something is ‘off.’ Sometimes a logo has the wrong colors or is an outdated version. Sometimes the tone of the message is strange. Your brain can notice little things like this before you consciously recognize what felt wrong.