Summer Stats
Now that we’re halfway through the year, many reports are being released with full 2021 data. I’m including some quick statistics for you here to stay alert on scams already covered in the past.
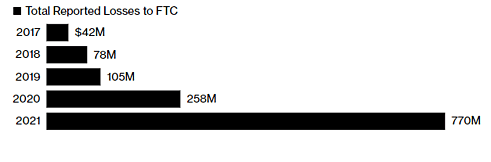
- Fraud losses on social media last year were 18 times higher than in 2017.
More than 95,000 people in the US reported fraud initiated on social-media platforms in 2021, with losses totaling about 770 million, according to the Federal Trade Commission. In 2017 that number was 42M. See chart above.
Scams tied to romance were the second-most profitable on social media, after investment fraud, the agency’s data show. And it’s important to remember this can happen to anyone.
“The younger crowd likes to think they are more tech savvy, but there are a huge amount of the younger crowd being victimized,” said Kathy Waters, founder of Advocating Against Romance Scammers. “All of them say, ‘I never thought it could happen to me.’”
- According to TrueCaller’s 2022 report, a staggering 39.5 billion USD was lost to phone scams in America over the past 12 months.
1 in 3 Americans (33%) report having ever fallen victim to phone scams, with 20% more than once.
Scam texts have more than doubled over the previous 3 years with males over 65 years old being the biggest targets.
The scams communicated over text vary ranging from consumer issues like changing cable TV providers, to cyber security issues, to data breach notifications.
- Researchers at Abnormal Security report vendor impersonation overtaking CEO fraud as a tactic.
“In January 2022, the number of attacks impersonating third parties surpassed those impersonating internal employees for the first time,” the researchers write. “This trend has continued each month since, with third-party impersonations making up 52% of all BEC attacks in May 2022.”
Abnormal Security notes that this tactic allows threat actors to target organizations of all sizes.
“We’ve seen this shift to what we’ve termed financial supply chain compromise for a number of reasons,” the researchers write. “Most notably is that the approach gives threat actors a plethora of additional trusted identities to exploit. Even the smallest businesses likely work with at least one vendor, and larger companies have supplier numbers in the hundreds or thousands. And while the average employee has some level of familiarity with the company’s executive team, they may not have that same awareness of the organization’s entire vendor ecosystem—particularly in larger enterprises. Further, the vendor-customer dynamic has an intrinsic financial aspect to it, which means emails requesting payments or referencing bank account changes are less likely to raise red flags. All of these factors combine to make a perfect environment for exploiting end user trust.”
1. Hiring Scams
In today’s climate of employee shortages and competitive recruiting, it’s more important than ever to make sure the person you’re hiring is truly that person. HR personnel and all hiring managers should be especially alert for these 2 scam tactics.
1. The FBI warns of an increase in “the use of deepfakes and stolen [identities] to apply for a variety of remote work and work-at-home positions. Deepfakes include a video, an image, or recording convincingly altered and manipulated to misrepresent someone as doing or saying something that was not actually done or said.”
These reports are primarily for IT jobs, but you can expect them to spread if scammers find them to be effective. And the goal of the imposters, according to Gizmodo, could be a “desire to steal sensitive information as well as a bent to cash a fraudulent paycheck.”
2. Contrast Security reports attackers using job-listing and networking sites such as LinkedIn to identify potential targets. Then they hide malware in documents claiming to be resumés and CVs.
Experts at KnowB4 explain, “As part of their job, HR employees frequently interact with people outside of the organization and are more likely to open external files.”
So what can you do to avoid this?
To address the deepfake issue, the FBI recommends paying close attention to the actions and lip movements in a video to see if they line up with the audio. Things like coughs and sneezes that do not show in the video can be a strong indication that you’re seeing a deepfake.
In addition, you can use the tips below from an MIT Media Lab research project that was designed to help people identify manipulated videos. These tips can also be used on the video and audio you see on social media to make sure you’re getting the true story.
- Pay attention to the face. High-end DeepFake manipulations are almost always facial transformations.
- Pay attention to the cheeks and forehead. Does the skin appear too smooth or too wrinkly? Is the agedness of the skin similar to the agedness of the hair and eyes? DeepFakes are often incongruent on some dimensions.
- Pay attention to the eyes and eyebrows. Do shadows appear in places that you would expect? DeepFakes often fail to fully represent the natural physics of a scene.
- Pay attention to the glasses. Is there any glare? Is there too much glare? Does the angle of the glare change when the person moves? Once again, DeepFakes often fail to fully represent the natural physics of lighting.
- Pay attention to the facial hair or lack thereof. Does this facial hair look real? DeepFakes might add or remove a mustache, sideburns, or beard. But, DeepFakes often fail to make facial hair transformations fully natural.
- Pay attention to facial moles. Does the mole look real?
- Pay attention to blinking. Does the person blink enough or too much?
- Pay attention to the size and color of the lips. Does the size and color match the rest of the person’s face?
Test your skills on the MIT project website, DetectFakes.
To address resumés and other attachments with malware hidden in them, continue or even increase your employee awareness training.
- Make sure your team uses caution when handling unsolicited messages. Be immediately suspicious of ZIP file attachments, and never click “Enable content” in a Microsoft document unless it is an expected file from someone you trust and have confirmed that they sent it.
- Take advantage of your IT partner and ask us to check attachments before opening them.
- When you set up phone interviews, let the call come through the office and be routed to you; do not give strangers your direct cell phone number.
Dmitri Alperovitch, chairman of the Silverado Policy Accelerator, warns of texts that contain implants that use the iMessage protocol to send spyware to your smartphone. He says nothing will show on your device when it happens, and he recommends getting in the habit of rebooting your cell phone every night because they can be brushed off fairly easily, at least sometimes.
“Oftentimes when they land on the device, while the device is running, they can collect information, they can communicate, they can activate the microphone, but once you reboot, the flag goes away, and unless you’re retargeted, you’ll be free of the malware.”
2. Monkeypox and Mail Order Brides
As we’ve seen again and again, globally trending news will likely become the topic of the next scam message in your inbox.
Researchers at Mimecast, an IT security company, report scam emails using Monkeypox to target businesses. The messages impersonate companies in an attempt to trick employees into visiting phony health safety sites that steal their information. The subject line tries to grab your attention as something official and important, and the message claims to be about Monkeypox safety awareness training that you need to complete.
Another scam seems to combine the headline news about Ukraine with the success of romance scams. Researchers at Bitdefender, a cybersecurity technology company, report, “in the past couple of weeks, spammers have been targeting internet users with a mixed bag of online dating opportunities such as mail order bride services and dating platforms where single western men can meet Ukrainian women.”
These ads and messages want you to click a link that will take you to their dating platform. That, of course, is not secure and asks for personal information such as your date of birth to set up an account. Once you do, you’re redirected to another platform where you can interact with these beautiful women. For a price. Emails, chat times, even unlocking photos has a cost. And guess who gets your financial information when you enter payment details.
How can you protect yourself?
- Start with the basics, checking your sender and subject line carefully. Researchers reported a spelling error in the Monkeypox subject lines they saw, which should set off a red flag. And when emails seem to come from within the company, make sure the name matches the email. Or that it is the exact right department email such as hr@ versus humanresources@.
- Pick up the phone and call or chat to confirm mandatory training at your company before clicking a link. Especially if that’s different from how you normally receive important information or training.
- Stop yourself any time you click a link and are asked to enter credentials. It is always safer to navigate independently to any login page.
- When it comes to online dating sites, stick to the ones you can verify are secure.
- Check the URL to make sure it is spelled correctly and not hosted in another country.
- Avoid clicking on an online ad altogether and navigate to the advertised site on your own.
- Always think twice (or three or more times) before entering any payment information online. There are many reputable websites, but there are far too many scams.
3. MGM Hotels Breach
This last one is different in that it is not about a specific scam but a general and very serious warning.
The VPNMentor security research team reports that a previous breach has now been released in full, for free, on Telegram, an app accessible to anyone.
The breach includes 142 million records of personally identifiable information (PII) of MGM Hotels customers prior to 2017. Different pieces of the breach had been exposed previously, and the data as a whole had been sold on the dark web, but now it is all public.
They estimate at least 30 million people had their data leaked with the following information:
- Full names;
- Postal addresses;
- Over 24 million unique email addresses;
- Over 30 million unique phone numbers;
- Dates of birth
KnowB4 explains why this is concerning:
“If you received a medical bill that had your birthdate, phone number, and name mentioned in it, you’d at very least give it a moment of your time to determine what the bill is, whether you owe it, etc. And you probably wouldn’t think that it was a scam, but – at worst – a mistake, right?
“This information could be used for [email, SMS, and voice] scams intent on using the compromised personal data to gain the trust of a potential victim in order to trick them into giving up banking and credit card details, credentials, and more.
“And given the actual breach occurred two years ago, people whose information is contained in the breached data aren’t expecting such attacks.”
So how can you stay safe from this?
- If you’ve never stayed at an MGM Hotel before 2017, you are not impacted by this particular breach. It’s just one of many, however. And it’s disturbing to wonder about the motivation behind releasing stolen records on public platforms like this. If you think you might be on this list, you should reach out to MGM.
- To best protect your online data, always use strong, unique passwords for every login. Your password won’t prevent that account’s network from being hacked, but it will protect all your other accounts from being accessed. Get tips and resources on good password hygiene here.
- Implement Multi Factor Authentication (MFA) on any accounts that allow it. That extra verification step takes just a few seconds but makes an exponential difference in your protection.
- Something else you can do, though it’s not preventative, is checking your email, phone number, and even your passwords on the haveibeenpwned site. Their search can tell you if your information has been included in a breach so you can address those accounts.
