1. Hijacked Google Ads
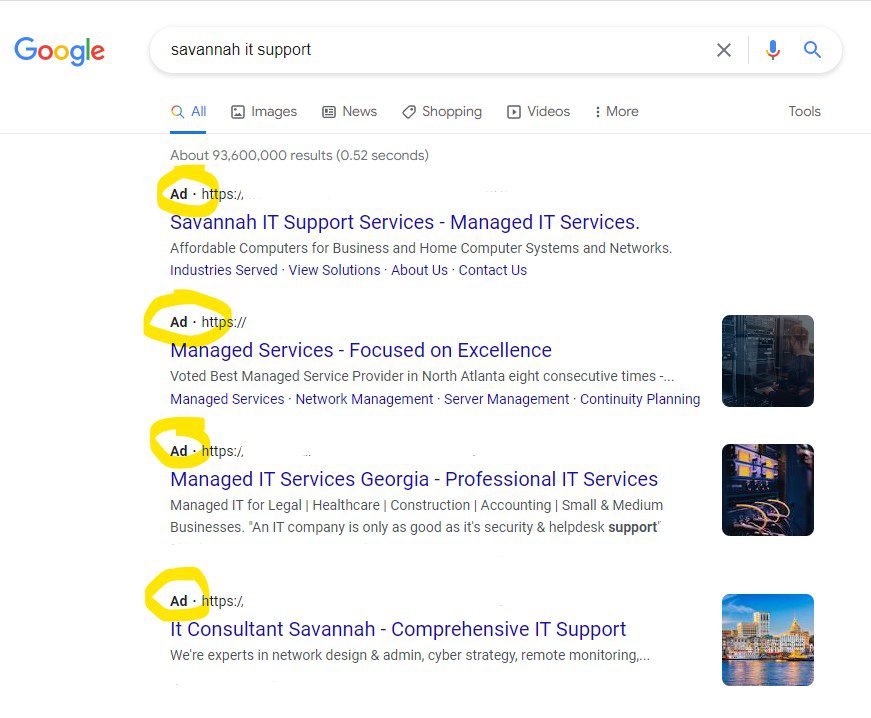
If you typically click on the first link that comes up in your search results, you may want to reconsider.
Researchers at Malwarebytes, a software company that aims to protect network endpoints, warn about a recent trend that has gone mainstream. Criminals posting malicious ad links is not new. But effectively targeting major brand names in this way is.
They describe it like this:
“The threat actors are abusing Google’s ad network by purchasing ad space for popular keywords and their associated typos. A common human behavior is to open up a browser and do a quick search to get to the website you want without entering its full URL. Typically a user will (blindly) click on the first link returned (whether it is an ad or an organic search result).
Let’s say you want to load YouTube and type ‘youtube’ instead of entering the full address ‘youtube.com’ in the browser’s address bar. The first result that appears shows ‘www.youtube.com’ so you are likely to trust it and click on it.”
The first link, however, may be an ad–a link someone paid to show up first.
If you click on the malicious ad in this scam, you will be redirected to a page that makes you think your computer has been infected. If you click on any of the prompts for help there, or call the ‘support’ phone numbers, you are contacting the criminals.
So what can you do to avoid this?
This is a tricky scam. It works on 2 very common human behaviors – 1. searching for a website rather than typing the URL directly into the address bar and 2. clicking on the top link in the search results.
- Bypass this threat by typing the website you want directly into the address bar or by bookmarking the site and navigating to it using your bookmarks.
- If you aren’t sure what the address is, go ahead and search, but be careful to look for the bold “AD” in front of any search results. Businesses pay to show up there, but criminals do, too. And they are cloaking and redirecting their links to appear as the website you want. Scroll down to links that do not have Ad in front of them.
- If you click an ad link and suddenly see warnings on your computer screen that you have been compromised or that there is a security alert, do not click anything. If it’s your work computer, call your IT team. If it’s your personal device, disconnect your Internet and restart. Remember that companies like Microsoft and Google are not going to call you, so if you suddenly receive any phone calls offering ‘tech support,’ they are also a scam.
2. Beware of Unknown USBs
Penetration testing teams – the people you hire to check your security systems for weaknesses – have used USB drives as a vulnerability tool for years.
As KnowB4 computer security consultant Roger Grimes says, “My favorite trick, when I was a full-time penetration tester, was to label the dropped USB keys with the company’s name and include a malicious file labeled “Pending layoffs”. Employees could not wait to plug those in and open the file.”
Now, you may be aware enough to be suspicious of a random USB drive or key lying in your work parking lot or in the lobby. But what if it came to you in the mail as part of a Microsoft or other software company package?
That’s the new scam researchers are warning about.
Examples include free software downloads and ‘updated’ devices that users should install because of security compromises. They arrive in fully branded packaging that may be real and repurposed or just very successfully copied.
No matter what the premise is though, installing the USB will install whatever malicious code or scam the criminals put on it.
How can you protect yourself?
- Never plug in a USB to your computer that you aren’t 100% sure is safe. It doesn’t matter if you picked it up off the ground, received it in the mail, or were handed it at a trade show. Unless you know exactly who the USB came from and what is on it, do not expose yourself and your company to the risk.
- Give any unknown USBs to your IT team to check for you. It’s absolutely possible that a colleague left their USB on the conference table. But ask them or get the USB checked. Do not plug it in thinking you’ll take a quick look and find out who it belongs to.
- Keep in mind that criminal tactics will continue to evolve. The USB lying in the parking lot may be obvious, but the one sent in the mail that looks like it’s really from Microsoft is not. These attacks do happen, and we need to stay alert for them.
3. Giveaway Scams

A recent scam circulating through WhatsApp motivated Heineken to issue a formal statement. They were not, in fact, giving away 5,000 coolers of free beer in honor of Father’s Day.
But how many people do you think saw the fake competition, versus how many saw the official statement? According to onlinethreats.com, the scam spread “like wildfire.”
And before you dismiss this as irrelevant because you don’t even use WhatsApp (neither do I), consider how many online competitions you have entered or seen. The Savannah Morning News website frequently promotes giveaways, for example. They are an effective tool for businesses to get new leads and build engagement. And they can be inexpensively distributed to large quantities of people via email, text, and social media.
All a criminal has to do is set up a webpage or form for capturing the data they want.
So how can you tell which giveaways are legit?
- Read the fine print. I know, I know. None of us wants to do this. But inside the terms and conditions, or even within a social media contest post, legitimate businesses typically spell out how and when you may be contacted, as well as by which social handle or email address. If this kind of information is missing, you’re probably looking at a scam.
- Stop if you see the contest asking for any banking or financial information. As the FTC explains in this article, real contests and giveaways do not require you to pay.
- Use caution if you feel any kind of urgency or pressure to enter. Official contests often, if not always, have a deadline for entering, but scams will be pushier. They’ll make it seem like you have to ‘enter now’ due to limited quantities or an expiring time so you rush.
- Take a moment to check the sponsoring company’s official website to see if the giveaway is mentioned. Alternatively, search for the company name and ‘giveaway’ or some related term to see if results come back warning you of a scam.
- As always, stop and think before clicking on any unsolicited links you get via email, text, or served to you online.
