You know that nagging feeling in the back of your mind? The one that surfaces when an employee leaves and you can’t quite remember which laptop they had. Or when you approve an invoice for software licenses, wondering if you’re paying for seats that no one is even using anymore.
It’s the quiet hum of operational chaos. And for small and midsize businesses, that low-grade anxiety is more than just a feeling—it’s a massive, hidden expense.
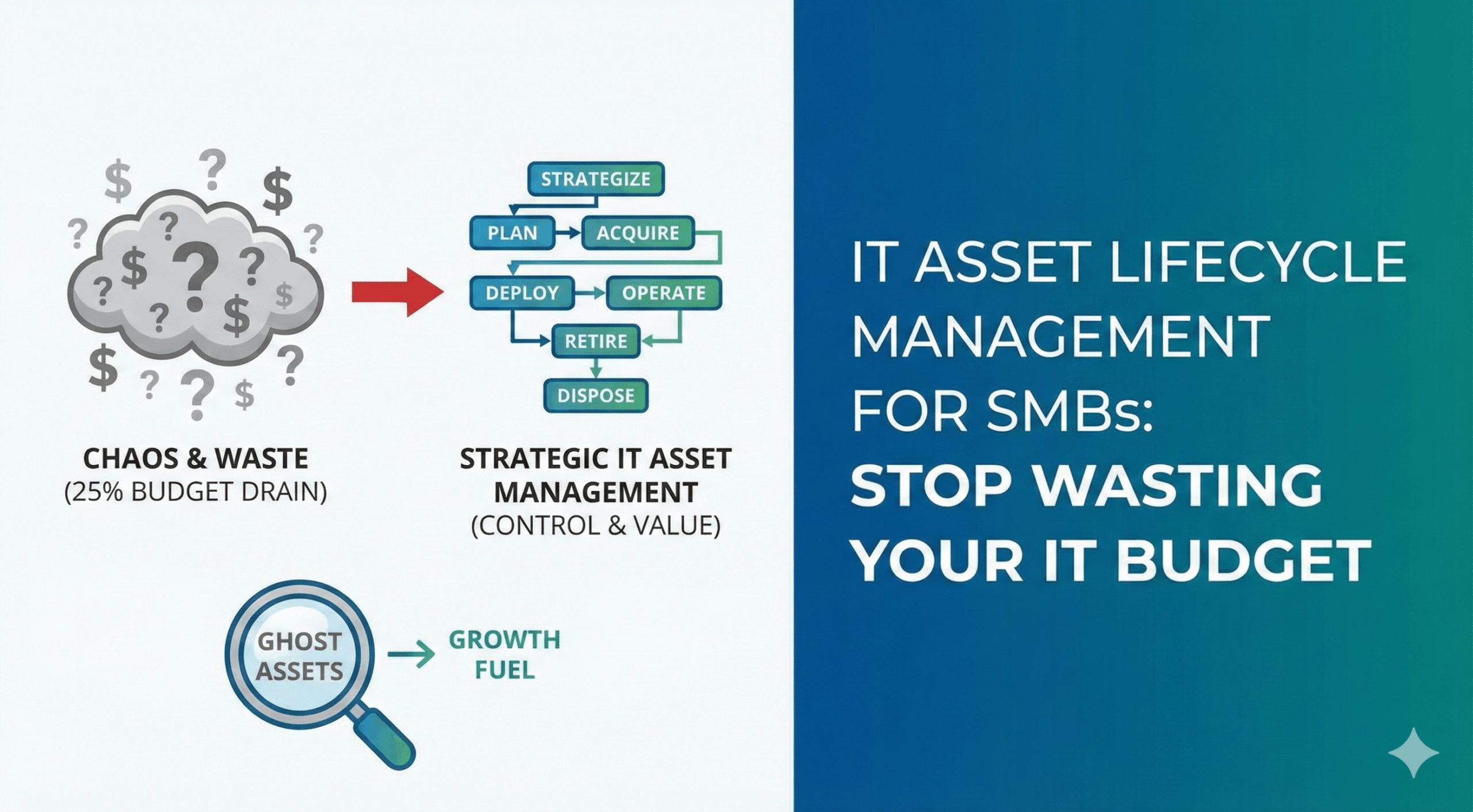
Here’s the hard truth: Up to 25% of IT budgets are wasted on “ghost assets.” That’s hardware and software that is on your books, in your billing, but is physically missing, broken, or simply sitting unused in a closet. A quarter of your technology investment, potentially vanishing into thin air.
This isn’t about sloppy bookkeeping. It’s about the lack of a system. A predictable, repeatable process for managing your technology from the day you consider buying it to the day you securely dispose of it. This process is called IT Asset Lifecycle Management (ITAM), and it’s not just for massive corporations with sprawling server farms.
For an SMB, a smart ITAM strategy is the single most effective way to turn your technology from a reactive, unpredictable cost center into a strategic asset that fuels growth. This guide will give you the financial and operational framework to do exactly that.
Table of Contents
- The High Cost of Chaos: Solving the Ghost Asset Problem
- The Critical Financial Crossroads: To Buy or To Lease?
- The Modern ITAM Lifecycle: 6 Stages for Today’s Distributed Workforce
- Stage 1: Strategic Planning & Forecasting
- Stage 2: Smart Procurement & Acquisition
- Stage 3: Secure Deployment & Tracking
- Stage 4: Ongoing Operation & Maintenance
- Stage 5: Retirement & Data Security
- Stage 6: Responsible Disposal & ESG
- The Future of Asset Management: Zero-Trust Security for a Remote World
- Key Takeaways: Your ITAM Action Plan
- Frequently Asked Questions (FAQ)
- From Chaos to Control: Build Your IT Asset Plan with Infinity
The High Cost of Chaos: Solving the Ghost Asset Problem
Before we get into the “how,” let’s be crystal clear on the “why.” What exactly is a ghost asset, and why is it costing you so much?
A ghost asset is any piece of IT equipment—a laptop, server, monitor, or even a software license—that your company is paying for but can’t account for. It might have been lost, stolen, broken beyond repair, or simply replaced and forgotten in a storage room. But it’s still on your books, and in many cases, you’re still paying for its associated costs, like software subscriptions or support contracts.
This is the 25% drain. It’s not one big leak; it’s a thousand tiny drips. It’s the subscription for the employee who left six months ago. The warranty renewal for a server that was decommissioned last year. The spare laptops that walked out the door and were never tracked.
This financial waste is just the beginning. The hidden costs are even more damaging:
- Security Risks: An untracked laptop is a data breach waiting to happen. If you don’t know where a device is, you can’t ensure it’s patched, protected, or wiped of sensitive company data.
- Lost Productivity: When an employee’s machine fails, how long does it take to get them a replacement? Without a clear inventory and a plan, it’s a frantic scramble. That downtime is a direct hit to your bottom line.
- Poor Decision-Making: You can’t budget accurately if you don’t know what you have. You end up buying new equipment you don’t need or getting caught off guard by sudden, massive replacement costs.
IT Asset Management is the cure for this chaos. It’s a simple framework for tracking every piece of technology you own, understanding its total cost, and making smart, data-driven decisions about its future.
The Critical Financial Crossroads: To Buy or To Lease?
One of the first—and most important—decisions in your asset lifecycle is how you acquire your technology. For most SMBs, this comes down to a simple question: should we buy our equipment outright or lease it?
There’s no single right answer, but making the wrong choice for your cash flow and business model can have long-term consequences. Think of it like deciding between buying a car and leasing one. Both get you on the road, but the financial implications are completely different.
Here’s how to frame the decision:
Buying IT Assets (CapEx – Capital Expenditure)
- The Upside: You own it. It’s your asset, and you can benefit from tax deductions like Section 179, which allows you to deduct the full purchase price in the current tax year. You have total control over the equipment without contractual restrictions.
- The Downside: The upfront cash outlay can be significant, tying up capital that could be used for growth. You also bear the full risk of obsolescence—when that new laptop is outdated in three years, it’s your problem to replace and dispose of it.
Leasing IT Assets (OpEx – Operating Expenditure)
- The Upside: Much lower upfront cost. You get the latest technology for a predictable, manageable monthly payment, which is great for cash flow. Tech refreshes are built into the cycle; at the end of the lease term (typically 3 years), you simply send the old gear back and get new equipment.
- The Downside: Over the full term, leasing is almost always more expensive than buying. You don’t build any equity, and you’re bound by the terms of the lease, which can include penalties for damage or early termination.
How to Decide? Calculate the Total Cost of Ownership (TCO).
The only way to make an informed decision is to look beyond the sticker price. TCO includes the initial purchase price plus all the direct and indirect costs over the asset’s useful life: support, maintenance, software licensing, and eventual disposal costs.
Comparing the 3-year TCO of a purchased laptop against the total cost of a 36-month lease gives you a true, apples-to-apples financial picture. This is where strategic IT consulting becomes invaluable, helping you build a financial model that aligns with your business goals, not just your immediate IT needs.
The Modern ITAM Lifecycle: 6 Stages for Today’s Distributed Workforce
The old model of ITAM was built for a world where every computer was in one office. That world is gone. Today’s lifecycle needs to account for remote employees, cloud services, and heightened security threats.
Here are the six essential stages of a modern ITAM program, tailored for the realities of an SMB.
Stage 1: Strategic Planning & Forecasting
This is where you stop buying technology reactively and start planning proactively. Instead of waiting for a laptop to die, you build a predictable refresh cycle (e.g., all employee laptops are replaced every three to four years).
Good planning involves:
- Defining Standards: Decide on a few standard models for laptops and desktops. This simplifies purchasing, support, and deployment.
- Calculating TCO: Before you buy anything, estimate its TCO. This prevents you from choosing a cheap device that ends up costing you more in repairs and downtime.
- Budgeting for the Future: A clear refresh policy means you can forecast your IT spending accurately for the next several years. No more surprise capital requests.
Businesses that get this right see incredible results. Rigorous TCO tracking alone can lead to a 15% annual reduction in asset-related costs.
Stage 2: Smart Procurement & Acquisition
Once you have a plan, you can purchase with confidence. But for a distributed team, getting that equipment into the hands of your employees is a major logistical challenge.
Modern procurement isn’t just about finding the best price. It’s about:
- Centralized Purchasing: Avoid letting employees buy their own gear. Centralize all purchases to maintain standards and control.
- Pre-Configuration & Shipping: The device should arrive at the employee’s home ready to go. This means it’s pre-configured with all necessary software, security agents, and management tools before it’s shipped.
- Vendor Management: Build relationships with a few trusted vendors who understand your standards and can handle the logistics of direct-to-employee shipping.
This stage is a core function of proactive managed IT services. A good partner handles the entire procurement and pre-configuration process, ensuring a secure and seamless experience for your team.
Stage 3: Secure Deployment & Tracking
The moment a new asset is deployed, it needs to be tracked. This is the heart of ITAM. A spreadsheet might work when you have five employees, but it breaks down quickly. It can’t tell you if a device is online, if its security software is up to date, or where it’s physically located.
This is where asset tagging comes in.
- Barcodes/QR Codes: The simplest and most cost-effective method. A unique label is placed on each device and scanned into your inventory system. It’s a manual process, but it’s a massive leap forward from a spreadsheet.
- RFID (Radio-Frequency Identification): These tags can be read from a distance without a direct line of sight. Great for quickly auditing a room full of equipment, but the cost is higher.
- BLE (Bluetooth Low Energy): These tags actively broadcast their location, allowing for real-time tracking of high-value assets. This is typically overkill for most SMBs but can be useful in specific industries like construction or manufacturing.
For most SMBs, a simple barcode system combined with a software agent on each device provides the perfect balance of cost and control.
Stage 4: Ongoing Operation & Maintenance
An asset’s life isn’t just about its beginning and end. The long middle period—its operational life—is where it delivers value. The goal here is to maximize that value by minimizing downtime.
This means tracking key metrics like:
- Support Tickets: Is one model of laptop generating far more help desk tickets than another? That’s a sign of a poor-quality device that’s costing you in lost productivity.
- Downtime: How long does it take to resolve issues? Tracking this helps you identify bottlenecks in your support process.
- Patch Status: Your inventory system should confirm that every device is up-to-date with the latest security patches. An unpatched machine is an open door for attackers.
This isn’t about implementing a complex, enterprise-grade system. It’s about using your ITAM data to make smarter support decisions.
Stage 5: Retirement & Data Security
When a device reaches the end of its life, you can’t just toss it in a closet. This is one of the most critical stages for security. That old laptop contains years of sensitive company data, client information, and financial records.
Proper retirement involves:
- Retrieving the Asset: Have a clear, documented process for recovering equipment from departing employees.
- Secure Data Wiping: Deleting files isn’t enough. The hard drive must be forensically wiped using certified software to ensure the data is completely unrecoverable.
- Updating Records: Once the device is wiped, your asset inventory must be updated immediately to reflect its retirement. This stops the “ghost asset” problem at its source.
This final step is a non-negotiable component of your overall cybersecurity and network security posture. A single improperly retired laptop can negate thousands of dollars spent on firewalls and antivirus software.
Stage 6: Responsible Disposal & ESG
After a device has been securely wiped, it must be disposed of. In the past, this meant a trip to the local dump. Today, there’s a growing focus on responsible, environmentally friendly disposal.
This is part of a larger trend known as ESG (Environmental, Social, and Governance). For SMBs, this means:
- Using Certified E-Waste Recyclers: Partner with a company that is certified to dispose of electronic waste in an environmentally sound way. They will provide a certificate of destruction, which serves as proof of your due diligence.
- Exploring Donation/Resale: If a device is still functional but past its useful life for your company, consider donating it to a local charity or using a certified reseller.
A responsible disposal policy isn’t just good for the planet; it’s good for your brand. It shows your customers and community that you’re a responsible corporate citizen.
The Future of Asset Management: Zero-Trust Security for a Remote World
So, why does all this tracking and planning matter more than ever? Because it’s the foundation for modern cybersecurity.
You may have heard the term “Zero-Trust.” It’s a security model built on a simple philosophy: “Never trust, always verify.” It assumes that threats can come from anywhere—inside or outside your network. In a Zero-Trust world, every device, user, and application must be verified before it’s granted access to resources.
And here’s the key: You cannot secure what you do not know you have.
A comprehensive IT asset inventory is the absolute first step in building a Zero-Trust framework. You need a real-time, authoritative list of every single device that needs to access your company’s data. Without it, Zero-Trust is just a buzzword.
Your ITAM program provides the ground truth that your security tools need to make smart decisions. It answers the critical questions: Is this a company-owned device? Is it fully patched? Is the user authorized?
In a world of remote work and ever-increasing cyber threats, ITAM is no longer just an accounting exercise. It is a fundamental pillar of your security strategy.
Key Takeaways: Your ITAM Action Plan
Feeling overwhelmed? Don’t be. Getting started with IT Asset Management is about taking small, deliberate steps. Here’s your action plan:
- Acknowledge the 25% Problem: Recognize that “ghost assets” are likely draining your budget right now. The first step is admitting you have a problem that needs to be solved.
- Start with an Inventory: You can’t manage what you don’t measure. Your first project is to create a baseline inventory of all your hardware and software.
- Analyze Buy vs. Lease: For your next major tech purchase, run a TCO analysis. Don’t just look at the purchase price; model the full cost over three years to see whether buying or leasing makes more financial sense.
- Define a Refresh Policy: Decide on a standard lifecycle for your key assets (e.g., 4 years for laptops, 5 years for servers). This creates predictability and makes budgeting easier.
- Create Offboarding Procedures: Immediately implement a formal checklist for when an employee leaves. This must include recovering all company assets and securely wiping devices.
Frequently Asked Questions (FAQ)
What’s the very first step to starting an ITAM program?
The first, most crucial step is conducting a physical inventory. Go office by office, and have remote employees self-certify, to create a baseline list of every piece of hardware you own. Compare this list to your purchase records. The discrepancies you find will be the “ghosts” you need to address.
Is ITAM software expensive for a small business?
It doesn’t have to be. Many modern IT management platforms include robust asset management features at a price point that is very accessible for SMBs. More importantly, the cost of not having an ITAM system—the 25% waste from ghost assets, the security risks, the lost productivity—is almost always higher than the cost of the software.
How often should we refresh our computers?
There’s no magic number, but a 3-5 year cycle is a common best practice. A 3-year cycle, often aligned with leasing, keeps your team on newer, faster hardware and minimizes repair issues. A 4 or 5-year cycle, more common with purchased assets, maximizes the value of the initial investment but can lead to higher support costs near the end of the lifecycle.
Can’t I just use a spreadsheet to track my assets?
You can start with a spreadsheet, and it’s certainly better than nothing. However, a spreadsheet is a static, manual document. It can’t tell you if a device is online, if its antivirus is updated, or what software is installed. It’s a temporary starting point, not a long-term solution.
From Chaos to Control: Build Your IT Asset Plan with Infinity
An effective IT Asset Lifecycle Management program does more than save you money. It brings order to chaos. It gives you control over your technology, predictability in your budget, and a stronger security posture.
It transforms IT from a source of frustration into a reliable engine for your business. And a well-managed asset lifecycle is the first line of defense in any robust disaster recovery and business continuity plan. When you know exactly what you have and where it is, recovery becomes exponentially faster and more effective.
For over two decades, we at Infinity, Inc. have been helping businesses across Savannah and the Low Country do just that. We’re not just an IT provider; we’re a strategic partner. We believe in building genuine relationships and providing the human-centered guidance you need to make technology your greatest asset.
Ready to turn that 25% waste into a strategic advantage? Let’s have a conversation about building an IT asset plan that works for you.