
Latest Microsoft Updates: November 2025
If you’re an SMB leader or IT decision-maker, staying ahead of Microsoft 365 changes isn’t optional—it’s mission-critical. Every update can impact productivity, security, and even
Free technology insights, tips, and news

If you’re an SMB leader or IT decision-maker, staying ahead of Microsoft 365 changes isn’t optional—it’s mission-critical. Every update can impact productivity, security, and even

Let’s be honest. There’s a reason we choose to live and work here in the Low Country. It’s the smell of the salt marsh at

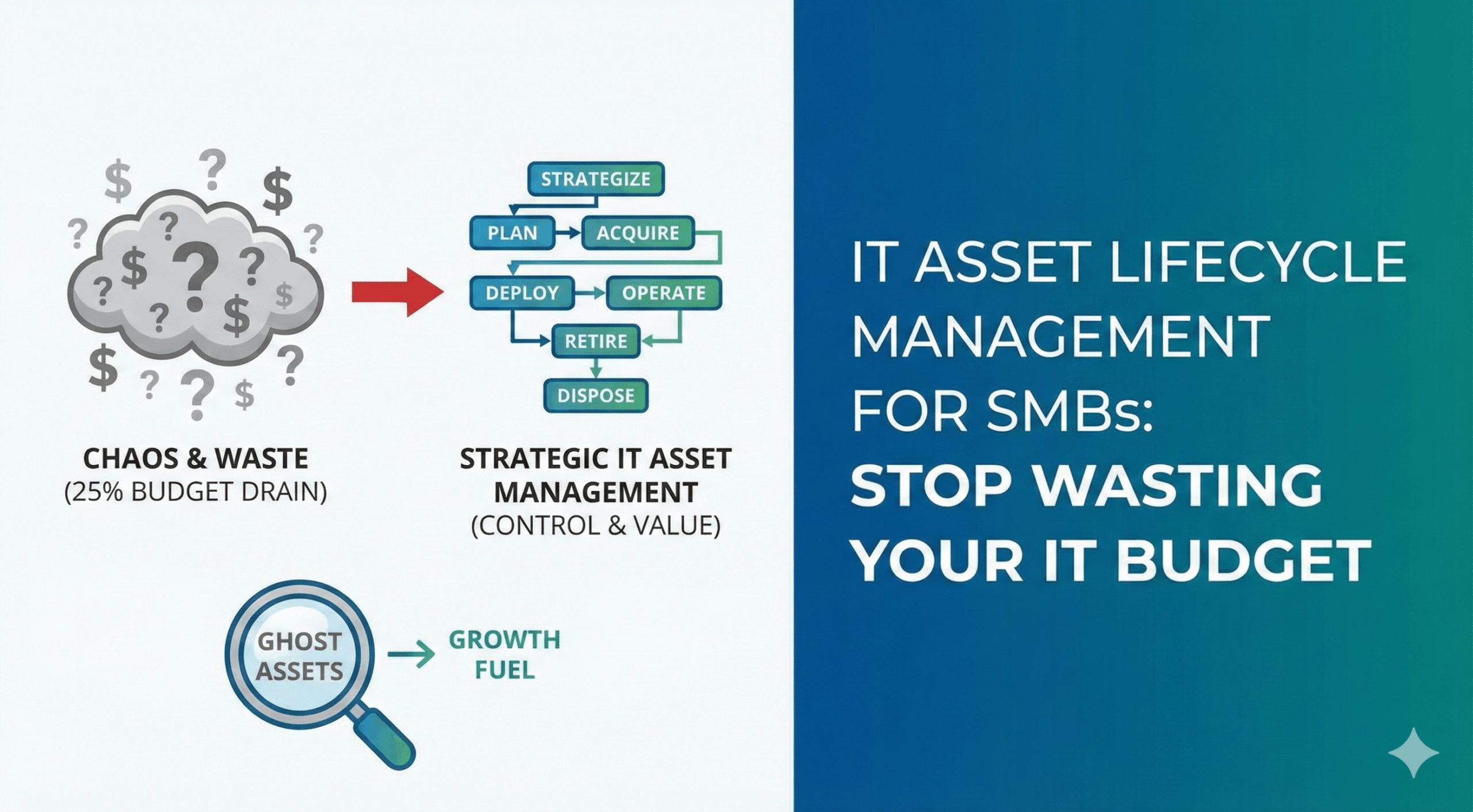







If you’re an SMB leader or IT decision-maker, staying ahead of Microsoft 365 changes isn’t optional—it’s mission-critical. Every update can impact productivity, security, and even

Let’s be honest. There’s a reason we choose to live and work here in the Low Country. It’s the smell of the salt marsh at

Your Infinity team is proud to announce we’ve won a fourth consecutive Best of Georgia Computer & I.T. Firm award!

You know that nagging feeling in the back of your mind? The one that surfaces when an employee leaves and you can’t quite remember which laptop they had.

It doesn’t take a major equipment failure to bring work to a halt on a construction site. One expired license for project management software, a wireless dead zone, or a missed field management system update can delay inspections, hold up change orders, or prevent crews from accessing critical project files.

All it takes is one missed software patch, network bottleneck, or expired credential for a mission-critical machine to go silent and freeze production. Assess your risk today.

When client outcomes depend on flawless timing and absolute accuracy, it only takes one lost file, outage, or technology hiccup to throw your legal services firm into chaos.

As summer winds down, Microsoft continues to roll out updates that help businesses stay productive, secure, and connected. Get the August 2025 updates here.

Nothing drains the profits (and the reputation) of a financial services firm faster than uncontrolled IT costs and sloppy tech management. The stakes are sky-high as every dollar wasted, and every vulnerability left unaddressed, impacts your bottom line and client confidence. Between relentless cyber threats, mounting regulatory pressure, and the crippling impacts of a data breach, there’s no room for complacency if you want to stay competitive and relevant.

Because construction is so sensitive to variables like economic growth and interest-rate changes, swings in the broader economy mean immediate consequences for construction budgets, pipelines, and profitability. Get cost controls here.
Whether you know exactly what you need or you would like our help in figuring it out, fill out the form.
We promise to get back to you promptly.
Clients, please use our Support form to submit tickets.