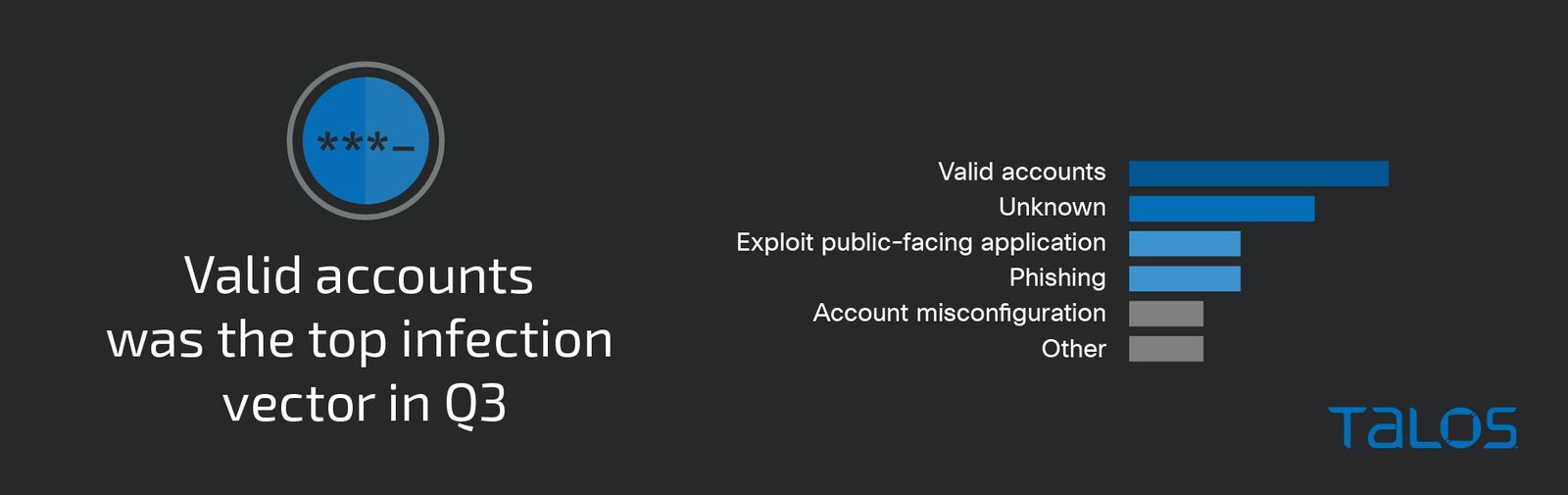
Notable Trends
Security vendor Talos recently released their Q3 Incident Response trend report. It identifies the use of “valid accounts to gain initial access, especially in cases where accounts were misconfigured, not disabled properly, or had weak passwords” as the most common initial infection vector.
The report also points out that “a lack of MFA remains one of the biggest impediments to enterprise security. Nearly 18 percent of engagements either had no MFA or only had it enabled on a handful of accounts and critical services.”
Both of these factors are controllable, meaning those incidents were preventable. Click the image to see the whole report.
1. Beware of Malicious Installers
Microsoft’s Security Threat Intelligence team has been tracking a threat actor that uses emails and other methods “to distribute malicious installers for legitimate applications, including TeamViewer, Microsoft Teams, Adobe Flash Player, Zoom, and AnyDesk.”
The attacks began as links in malicious ads, fake forum pages, blog comments, or through scam emails. They have evolved into using website contact forms, legitimate software depositories, and Google Ads to distribute their links.
Microsoft describes these attacks as showing “a pattern of continuous innovation, with regular incorporation of new discovery techniques, defense evasion, and various post-compromise payloads, alongside increasing ransomware facilitation.”
What can you do to avoid these scams?
Downloading programs and software updates is a regular part of our lives now. But it should still be done with extreme caution.
- Never download something you did not independently navigate to unless you know, trust, and confirmed with that sender that it is valid. For example, you know and trust your Support team. And it wouldn’t be crazy for them to tell you you need a new version of Zoom or Teamviewer, right? But ask yourself if we would send you a link to download or if we would just install it for you. And keep in mind that any sender can be spoofed, including us. So always verify in some way before downloading.
- Microsoft recommends implementing mail flow rules and safe links security tools to help prevent these campaigns from reaching you in the first place. They also encourage limiting local admin privileges. But the most effective prevention they recommend is what you’re doing right now: gaining awareness of the threats and learning how to handle them.
2. Unusual Login Scam
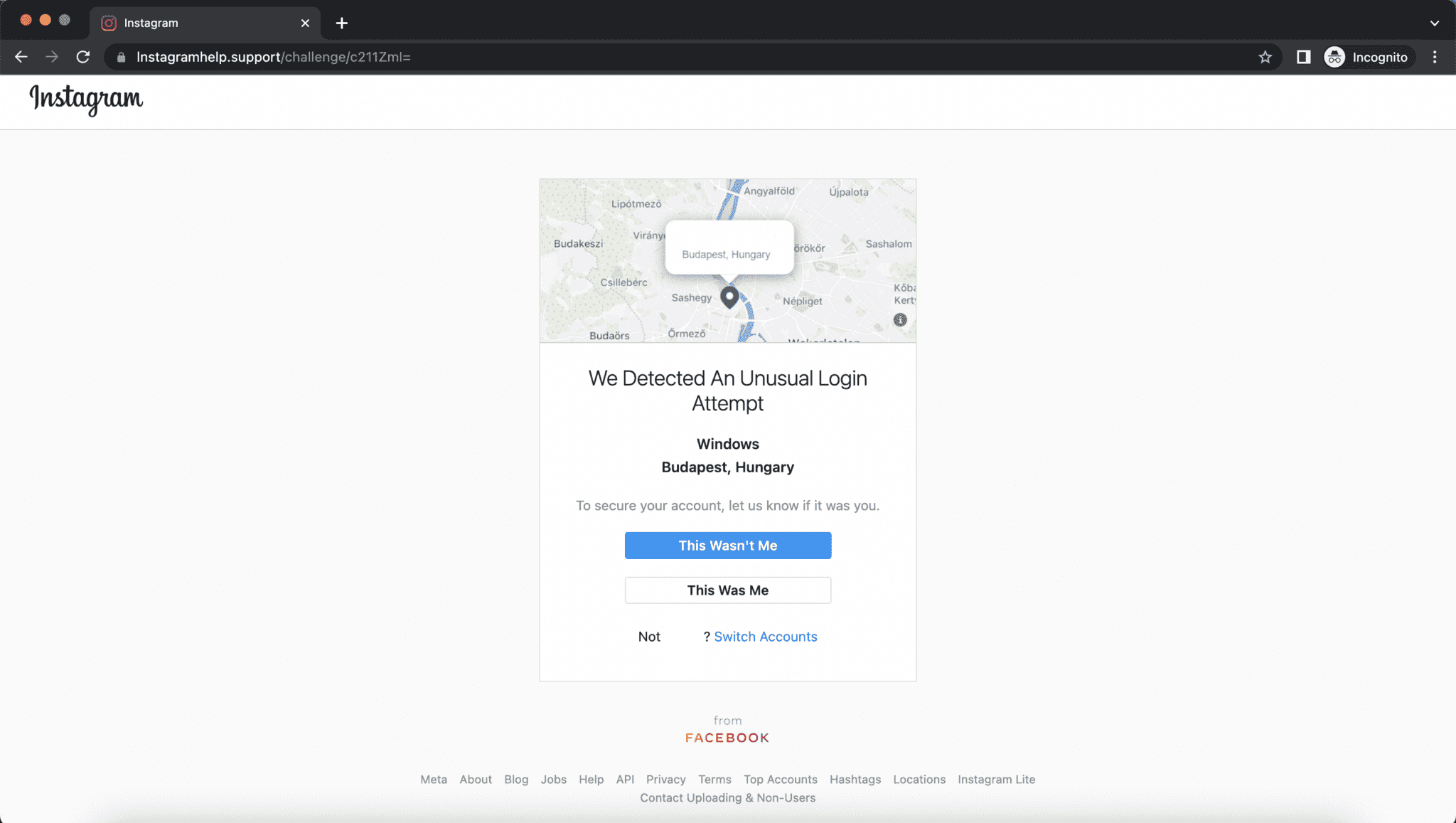
More than 22,000 mailboxes were targeted in this recent Instagram impersonation scam. And it’s a good one to learn from even if you don’t have Instagram because it will most likely be replicated and used for other platforms.
Security researchers at Armorblox describe how this scam starts as an email with the subject line ‘We Noticed An Unusual Login, [user handle]’.
“The email looks like a notification from Instagram, notifying recipients about unusual login activity on his or her account. The body of the email coincides with the spoofed email subject and sender, with details around a login from an unrecognized device. This targeted email attack was socially engineered, containing information specific to the recipient – like his or her Instagram user handle – in order to instill a level of trust that this email was a legitimate email communication from Instagram. The victim is prompted to review the details provided and secure his or her account if the login attempt was not legitimate.”
Clicking on the link in the email takes you to a well-made but fake landing page. It shows the fake login location with buttons below for you to click ‘This wasn’t me’ or ‘This was me.’
It’s the kind of notification we are all used to seeing now, often when we travel. The kicker is that if you click on ‘This wasn’t me,’ the next page is where they harvest your credentials. Instead of a reset password link or fields for a new password and confirmation, they want your old password, too.
How can you protect yourself?
- Always stop yourself before entering credentials on a page you did not independently navigate to. Always.
- Try to pay attention to emails like this that are designed to make you feel fear and react without thinking. None of us wants to deal with a hacked account. But that’s why it’s even more important now to slow down when we get messages like this. Carefully check the spelling of sender names, emails, and URLs. And open a new tab or window to check your account rather than clicking the link. Especially when it leads to a page asking for both old and new passwords.
3. Clone Phishing
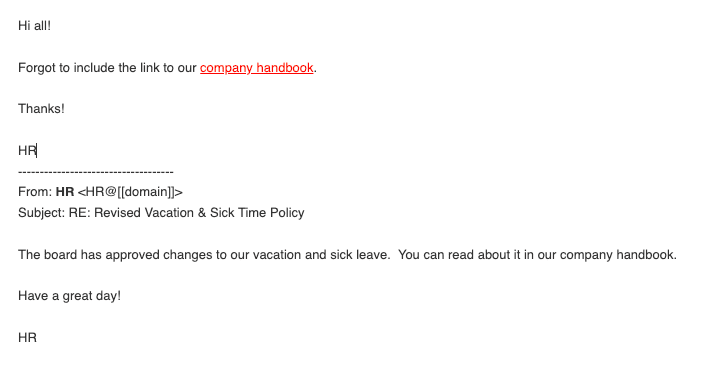
“Imagine receiving a legitimate email from a brand you know and trust. Later you receive the same email again, only this time the sender explains they forgot to include additional recipients or information.
Without knowing the obvious signs of clone phishing, you trust the email as authentic and accept the sender’s reasoning without a second guess. After all, the email’s content and context give you no reason for suspicion. It turns out, however, that this second email isn’t legitimate, but a clone of the original message, intended to deceive you into clicking a malicious link or downloading a harmful attachment.”
This is how researchers at Vade Secure describe the new scam tactic of cloning emails. And it doesn’t end there. These cloned messages are often sent out to numerous recipients. Whenever someone falls for it, they access that individual’s contacts and forward them the cloned email, spreading the reach of the initial attack. And once they have penetrated a company’s network, they can use additional campaigns to target other employees, customers, or partners.
“Highly deceptive and devastating, especially to organizations like SMBs,” they call it.
So how can you stay safe from this?
- To start with, the usual rules apply. Carefully check the sender name and email for any misspellings or red flags. Then check the message itself. If anything at all about the language or tone seems ‘off’ to you, trust that instinct.
- Verify with the original sender before clicking any links or opening any attachments. Pick up the phone or send a quick chat. If you are the sender, email services like Outlook give you the option of Recalling and Resending a message so you can simply replace the original email rather than forwarding or replying and looking like this clone tactic. And you can usually communicate company-wide with Teams or another chat tool to say whether or not it is legitimate.
- Don’t be afraid to report messages to us to check for you. Tools like PhishMe make it as simple as a click right in Outlook to let us know you think a message is suspicious. We can test it in a secure environment and let you know if it was real or if you just saved the whole company from an attack.