New threats slide into your mailbox every day. So we’re sharing a monthly digest of the latest and greatest of those attacks and how you can avoid falling for them. This will typically be a ‘Top 3’ cybersecurity scams. Enter your email below to receive it on the first of every month.
As IT professionals, we hear some real horror stories. They keep us motivated to provide you with the best protection available. And we know that awareness is key. So as your partner, we want to help arm you against these threats.
For more ways to improve your cybersecurity intelligence, browse that category of our blog, and sign up to receive this convenient, monthly email.
Security Brief – January 1, 2024
The Current Climate
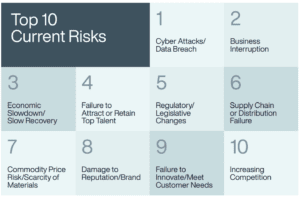
Top 10 Current Business Risks
According to Aon’s 2023 Global Risk Management Survey, cyber attacks remain the number 1 risk to businesses, both currently and for the future, as they were in the last survey (2021).
From the report:
“Cyber risk did not come into the top 10 until 2015, but it has since risen in importance and became the number one risk globally in 2021 and again in 2023.
Corporate digitization programs as well as increases in remote working and the widespread use of automation and service centers mean that cyber exposure is a critical aspect of overall organizational success. Mitigation actions and protocols can quickly become ineffective as soon as attackers shift their tactics. As Aon’s 2023 Cyber Resilience Report highlights, ransomware attacks were more than 1,010 percent higher in the third quarter of 2023 than they were in the first quarter of 2019, even though they declined in 2022. The overall rise in malicious activity is evident in regular news reports of breaches and exemplifies the need for continued vigilance and proactive protections.”
Click on the image above to read the key findings report with breakdowns by region and by the respondent’s role.
Ransomware Rising
The NCC Group’s Cyber Threat Intelligence Report recently came out with ransomware data through November 2023. It shows some alarming, though not surprising, statistics:
- The number of attacks from January through November of this year is approximately 85% greater than the same timeframe last year.
- The number of attacks in November alone is 67% more than November of last year.
As security researchers at KnowBe4 say, this “data signals that we may be in for a bumpy ride in 2024.”
Spam and Scam Calls Stats
Do you answer unknown calls on your cell phone? Or respond to unknown texts? No judgment whether you do or don’t, but this data may make you think twice.
TrueCaller, a global communications provider, recently released its first Monthly U.S. Spam and Scam Report. And it has some appalling numbers.
- Americans receive 2.1 Billion spam calls each month
- The average American individually gets 5.6 spam calls a month
- The average spam call is 3.36 minutes long
Their information ranks Georgia 6th and South Carolina 2nd in the Most Unwanted Calls on average per user per month. It’s not a top 10 we really want to be in.
The image below shows details for Georgia. You can click on it to see the other findings and look at other states’ stats.
So that’s where we are, our current climate.
That’s the reality we live and work in.
I don’t share this information to be full of doom and gloom. I share it like a warning sign on the road of a sharp curve ahead or a low gas indicator in your car. If you don’t slow down, you could take the curve too quickly and have an accident. If you don’t stop to get gas soon, you could run out and be stuck somewhere inconvenient or even dangerous.
The point is to be aware so you can prepare.
- Teach your team about the risks and how to properly handle them.
- Make sure you have multiple layers of protection built into your business.
- Don’t freak out, but don’t be complacent. Check on your cyber insurance coverage.
- Test your business continuity and incident response plans.
- If you have questions, ask them. Even when you don’t like the answers, it’s better to know so you can move forward.
News and Updates
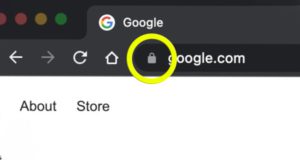
Chrome Padlock Icon Change
Have you looked at the address bar on a website in Chrome lately?
Google Chrome made a change recently, and it’s likely you never even noticed. It’s also okay if you didn’t. But here’s the explanation.
The padlock icon (left) has been changed to the tune icon (right) shown below.
![]()
They changed it because the padlock was misleading, or more accurately, misunderstood by most users.
The Chrome Security Team explains:
“Replacing the lock icon with a neutral indicator prevents the misunderstanding that the lock icon is associated with the trustworthiness of a page, and emphasizes that security should be the default state in Chrome. Our research has also shown that many users never understood that clicking the lock icon showed important information and controls. We think the new icon helps make permission controls and additional security information more accessible, while avoiding the misunderstandings that plague the lock icon.”
So now you know. And you can click on the tune icon, or the padlock still in use on other browsers, and access the security controls you never knew you always had access to.
Cyber Crime Marketplaces on the Open Web
This news is less positive but still important to know.
KnowBe4 breaks it down:
“According to cybersecurity vendor ZeroFox, cyber crime marketplaces are beginning to shift to the open web. One such marketplace is OLVX, available using a .cc top level domain. This marketplace sells services and products including:
- Ph|shing kits
- Remote desktop connections
- Cpanel credentials/access
- Webshells
- Spam sending platforms
- Stolen data
- Webmail access
By moving to the open web, it becomes easier to leverage traditional Internet services and platforms like Telegram, social media, SEO, etc. to act like any other legitimate business that seeks to advertise, outreach, and direct potential customers to their website.
This shift to the open web makes cyber crime tools much more accessible; something that organizations should be concerned about, as it means more players in the market, higher frequencies of attacks, better tools and techniques used over time, and – potentially – a higher likelihood of successful attack.”
Russian Hackers Indicted
But to end on a higher note, the Department of Justice put out a press release about this.
Two Russian Nationals Working with Russia’s Federal Security Service Charged with Global Computer Intrusion Campaign
“The indictment…alleges the conspiracy targeted current and former employees of the U.S. Intelligence Community, Department of Defense, Department of State, defense contractors, and Department of Energy facilities between at least October 2016 and October 2022. In addition, the indictment alleges the conspirators – known publicly by the name “Callisto Group” – targeted military and government officials, think tank researchers and staff, and journalists in the United Kingdom and elsewhere, and that information from certain of these targeted accounts was leaked to the press in Russia and the United Kingdom in advance of U.K. elections in 2019 [designed to influence that election].
As a common example, the conspirators used ‘spoofed’ email accounts designed to look like personal and work-related email accounts of the group’s targets. The conspirators allegedly also sent sophisticated looking emails that appeared to be from email providers suggesting users had violated terms of service. These messages were designed to trick victims into providing their email account credentials to false login prompts. Once the conspirators fraudulently obtained the victim’s credentials, they were able to use those credentials to access the victims’ email accounts at will.”
Read the full DOJ press release here.
Granted, this is an indictment, not a conviction. But you can see the methods used and learn from that. And this shows that the partnership among agencies can be effective in bringing down criminals. It can seem like they run unchecked with all the hacks and breaches we hear about, but just keep staying alert and reporting anything you’re not sure about. You’ll not only protect your own company better, you’ll help others down the road as well.
Security Brief – December 1, 2023
Holiday Season Safety (Video)
Amidst the holiday joy and end-of-year madness, remember to keep your business protected with a few key reminders. This 2-minute video is a special sneak preview for you with 4 simple, actionable tips.
FBI Public Service Announcement
Speaking of the holidays, the FBI has issued a PSA for buyers and sellers to be more alert with their online transactions.
There’s good reason for this. During the 2022 holiday shopping season, the FBI Internet Crime Complaint Center (IC3) received reports from almost 12,000 victims reporting non-payment/non-delivery scams, resulting in losses of over 73 Million.
Click here to read the PSA as a reminder for yourself, and don’t be shy about sharing it with your loved ones. Too often, embarrassment about admitting how we got tricked keeps us from saving others from the same horrible experience.
Ransomware-Aware
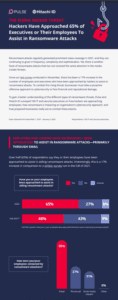
1 in 34
That’s how many organizations worldwide experience an attempted ransomware attack now.
North American companies sit at 1 in 69, but that’s still a 25% increase over last year. And industry can bump you up – Healthcare, Education, and Finance are 1 in 25, 27, and 29, respectively.
This data is from Check Point Research.
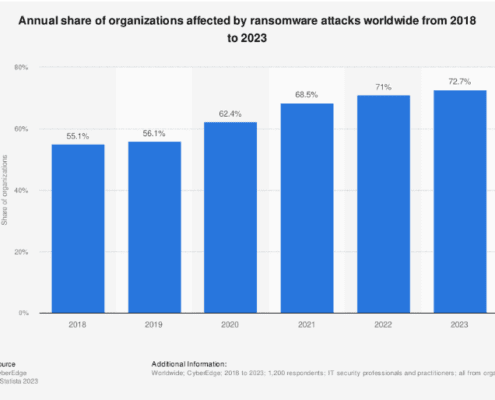
To get an even fuller picture of the impact ransomware has on all of us, look at this chart from Statista (below). It shows the Annual Share of Organizations Affected by Ransomware Attacks Worldwide from 2018 to 2023. Click on the chart to visit Statista.
What does this mean?
It means that 1 in 34 organizations may be experiencing the attacks, but more than 72% of organizations are impacted. So maybe you didn’t get hit, but your vendor did. Or one of your software providers. And so on.
To add more layers to this colorful threat landscape, Huntress, a managed security service founded by former NSA cyber operators, reports that 60% of ransomware incidents in their Q3 SMB Threat Report were from uncategorized, unknown, or ‘defunct’ ransomware strains.
Their researchers explain this significance, “While we often hear about headline-grabbing ransomware entities, many lesser-known ransomware strains are prevalent in the SMB space. This diversity suggests that size is no deterrent for cyberattacks, and small businesses should not underestimate the risk posed by ransomware, regardless of the strain’s notoriety.”
Huntress also points out that Business Email Compromise (BEC) poses a big threat for SMBs and that “identity-based attacks are on the rise with threat actors targeting cloud services to steal identifying information or break into business emails.”
Bottom line?
You still have to keep training your employees not to click on unexpected links and attachments. You still have to make everyone aware of proper verification processes so they don’t fall for impersonated texts and emails. But you also need to look at suspicious behaviors in network activity, too.
But don’t get discouraged.
As the threats evolve, our protections evolve. It’s only natural that the criminals will keep trying new things to separate us from our data/money. So we will continue to develop and implement better monitoring, detection, and defense.
As always, the point of this security brief is to make you aware, not afraid.
One Last Smishing Stat
Zimperium, a mobile security company, shares data that reminds us to include mobile devices in our employee awareness training. As the image shows, their 2023 Global Mobile Threat Report finds that users fall for text attacks 6-10 times more than email-based attacks now.
Click the stat to view more insights from their report. And remember to think before you click even, or maybe especially, on your phone.
Security Brief – November 1, 2023
Quishing
Quishing, or using QR codes to send malicious links, is the latest trend on the cybercriminal block.
I’ve talked about the risks of QR codes before, most recently in August and most thoroughly in March 2022. And now we’ve reached the point at which using QR codes in scams has become popular enough that it has its own term.
Malicious emails are called phishing, scam SMS/texts are called smishing, voice call scams are called vishing, and using QR codes to send malicious links is now called quishing.
In fact, last week I received the email below.
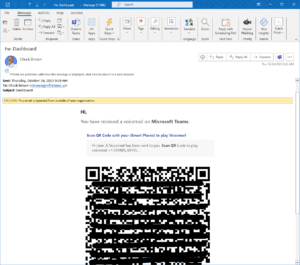
As you can see, this message claims to be a link to a voicemail. There are a few obvious red flags though.
- This is not how voicemails come to us at work: wrong sender, wrong message, and no attachment.
- It seems strange that a voicemail would come ‘on Microsoft Teams.’
- The word ‘recieved’ is misspelled.
- ‘Smart Phone’ is in parentheses for no reason.
- The subject line says ‘Dashboard.’
For someone who is rushing, however, those warnings could be missed. And we have been trained to pick up our cell phones when we see QR codes to get information.
That’s part of the danger with quishing. We switch from our typically protected computers to our often less protected mobile devices. And we rarely check to see what the QR code link is pointing to; we simply click on it.
Please stay alert for QR codes sent to you via email, and immediately stop yourself if you see one. Ask yourself why the sender wouldn’t have just included a clickable link. Remember to check for the usual warning signs in sender, subject, and urgency. And report any messages you are unsure of.
4 Scary Stats
1 Approximately 10,000 harvested credentials are put up for sale monthly on the dark web.
– Microsoft Digital Defense Report 2023
2 Targeted email campaigns that add phone calls (vishing) were 3X more effective than those that didn’t.
3 In a research project performed by IBM, a human-crafted scam email was only 3% more successful than the AI-generated one.
What’s more, the human-crafted one took 16 hours to make versus the AI taking about 5 minutes.
4 Senior citizens are being targeted and losing their life savings:
Between January and June 2023, 19,000 complaints related to tech support scams were submitted to the FBI Internet Crime Complaint Center (IC3), with estimated victim losses of over 542 Million.
Almost 50% of the victims reported to IC3 were over 60 years-old, comprising 66% of the total losses. As of August 2023, losses have already exceeded those in 2022 by 40%.
– FBI ‘Phantom Hacker’ Public Service Announcement
Global News Scam Reminder
The FBI put out a Public Service Announcement last week about charity frauds taking advantage of the Israel HAMAS conflict.
If you’ve been getting this security brief for a while, then you already know that headlines give scammers everything they need to prey on people’s emotions. And the bigger the news–especially a disaster–the larger the audience they can target.
We’ve talked about aid scams following hurricanes, ticket scams to events like the Olympics, donation scams related to the war in Ukraine, and far too many others. Now, the FBI is warning us all to be alert for fake humanitarian donation scams.
These schemes show up in emails, on social media, and in ads. They can use real agency names but direct to spoofed websites, or they can make everything up. Their goal is to separate you from your money by whatever means possible.
So please remember to verify independently any entity that you want to donate to and never give your personal banking information away to do so.
October was Cybersecurity Awareness Month
October 2023 marked the 20th anniversary of Cybersecurity Awareness Month.
Infinity was proud to champion this collaboration between the government and private industry again, aiming to empower everyone to protect their personal data from digital forms of crime. As we become more dependent on technology, it’s more important than ever to strengthen and adapt our cybersecurity habits.
This year’s focus was on 4 simple actions we can take as individuals and business owners to make our networks more secure.
- Create Strong Passwords and Use a Password Manager
- Turn on Multi Factor Authentication (MFA)
- Recognize and Report Phishing
- Update Your Software
Consider this:
Only 33% of individuals create unique passwords for all accounts. (National Cybersecurity Alliance)
Imagine 2/3 of your team using their work password as their streaming services password, or for their social account, or their Amazon password. Now if any of those get breached, they’re all at risk.
No matter how many layers of protection you have in place on your business network, a non-unique password opens it right up.
This is why building employee awareness is so important and why Cybersecurity Awareness Month has been around for 20 years and continues to make an impact.
Click on the image below to view and download an infographic you can share with your team.
Security Brief – October 1, 2023
October is Cybersecurity Awareness Month
October 2023 marks the 20th anniversary of Cybersecurity Awareness Month.
It’s a collaboration between the government and private industry to empower everyone to protect their personal data from digital forms of crime. It’s celebrated all over the world, and as we become more dependent on technology, it’s more important than ever to strengthen and adapt our cybersecurity habits.
The theme is Secure Our World as you can see above. And this year’s focus is on 4 simple actions we can take as individuals and business owners to make our networks more secure.
- Create Strong Passwords and Use a Password Manager
- Turn on Multi Factor Authentication (MFA)
- Recognize and Report Phishing
- Update Your Software
Consider this:
Only 33% of individuals create unique passwords for all accounts. (National Cybersecurity Alliance)
Imagine 2/3 of your team using their work password as their streaming services password, or for their social account, or their Amazon password. Now if any of those get breached, they’re all at risk.
No matter how many layers of protection you have in place on your business network, a non-unique password opens it right up.
This is why building employee awareness is so important and why Cybersecurity Awareness Month has been around for 20 years and continues to make an impact.
For an infographic you can share with your team, click on the image below to view and download.
And for tips throughout the month, visit our Facebook and LinkedIn pages.
You can also meet our new mascot here.
Warn Your Social Media Managers
A new malware attack is targeting millions of businesses on Facebook. It has a 1 in 70 success rate according to Guardio researchers so please be alert.
It begins as a message through Facebook Messenger. The topic may be about misusing a photo, the business page violating Facebook policy, or someone claiming they want to buy your product.
The good news is that each of these attacks include a link with .rar in the name, and if your people are up on their awareness training, they’ll know to never trust an unsolicited RAR file.
If you don’t already know, a RAR file is similar to a ZIP file; it’s a data container or archive containing one or more compressed files. It can contain almost anything and should never be opened or extracted when sent unexpectedly.
But it’s still good to share the alert since it’s clearly being successful. Unfortunately, people will always be curious and tempted to click and see the photo they’re being accused of misusing or just exactly how they supposedly violated policy, etc.
Fake Scan Details in Email
Researchers at Bleeping Computer shared this warning just a few days ago:
“Hackers are utilizing a new trick of using zero-point fonts in emails to make malicious emails appear as safely scanned by security tools in Microsoft Outlook.”
Essentially, the criminals insert text or characters in a message that looks like an official statement of the email being scanned, and then set the font size to 0. That makes the text invisible to readers but not to the email system. Then in the email listing pane, that fake secure message shows up and could easily trick someone into thinking it’s real.
In the image below, the red-boxed text in the listing pane is not visible in the email preview. It says, “Scanned and secured by Isc®Advanced Threat protection (APT): 9/22/2023T6:42 AM.” It should appear in the message where the yellow highlighting is, but the font size was set to zero.
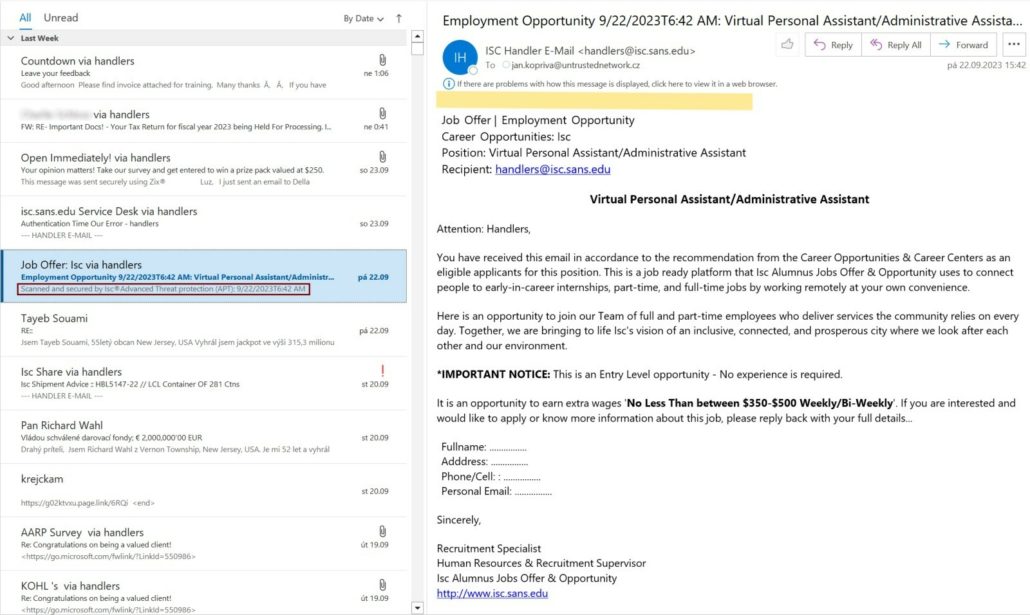
This tactic alone is not going to download malicious files, but it could make someone who is quickly scanning their emails believe the message is legitimate. And that person could click on a link they never would have otherwise.
It’s just something new to be aware of so we won’t be fooled by it if we see it.
Security Brief – September 1, 2023
Windows Server 2012 and 2012 R2 End of Life
This is a reminder that Microsoft has announced the End of Life for Windows Server 2012 and 2012 R2 on October 10, 2023.
End of Life means no more “security updates, non-security updates, bug fixes, technical support, or online technical content updates.” It means increased risk. So please make sure you have a solution lined up. If my team and I can help, please don’t hesitate to reach out.
At-risk Accounts
A couple of weeks ago, the Cyberint research team observed and reported on “an ongoing and successful hacking campaign targeting LinkedIn accounts.”
They saw posts of LinkedIn users saying they had been locked out of their accounts and found a 5,000% increase in the last few months of search terms for LinkedIn ‘hack’ or ‘recover record.’ There were also reports of users being pressured to pay a ransom to get access back.
Cyberint says the motive is unclear, but the impact could be vast:
“Threat actors could exploit compromised profiles for social engineering, manipulating others into engaging in harmful activities under the disguise of a trusted colleague or supervisor. Furthermore, instances of blackmail have surfaced, wherein victims are forced to pay for the threat actors’ financial gain. Moreover, valuable information exchanged in LinkedIn conversations between colleagues could be leveraged by threat actors for data gathering. Additionally, reputational damage is serious, as users often rely on LinkedIn to showcase their accomplishments, publish content, and bolster their professional image. Hacked accounts could be used to spread malicious content, erase years of contributions, or send damaging messages to connections, severely damaging an individual’s reputation. Users’ substantial efforts in building connections, followers, and reputations over time could be destroyed in seconds.”
So if you have a LinkedIn account, make sure your password is strong and unique, and turn on two-factor authentication (2FA) if you have not yet.
Duolingo
If you, or someone you know has ever used the language learning app Duolingo, be on the lookout for targeted attacks.
Hackers have released 2.6 million real names, emails, and Duolingo details on the dark web. Experts warn that convincing and personalized messages could go out targeting these people to download malware, give up their payment information, or outright pay the criminals money by impersonating Duolingo.
As I’ve mentioned before, you can use the website HaveIBeenPwned to see if your email has been compromised. But if you’re not comfortable with that, try to be extra careful and alert with any messages about Duolingo or related topics. Even if you get one that looks legitimate, go to the app or website independently, without clicking on any links.
CISA, the NSA, and the FBI recently co-authored a cybersecurity advisory, along with agencies from Canada, Australia, New Zealand, and the UK, on the 2022 Top Routinely Exploited Vulnerabilities.
The reason for the report is this: “In 2022, malicious cyber actors exploited older software vulnerabilities more frequently than recently disclosed vulnerabilities and targeted unpatched, internet-facing systems.”
Why?
“Malicious cyber actors generally have the most success exploiting known vulnerabilities within the first two years of public disclosure.
…developing exploits for critical, wide-spread, and publicly known vulnerabilities gives actors low-cost, high-impact tools they can use for several years.”
Click the image above to view the pdf and get details on the common vulnerabilities and weaknesses, as well as recommended mitigations.
If I can save you some time, however, I would boil it down to this: apply timely patching to your systems.
The report includes more, including setting up detection and analysis tools, for example, but if you can apply patches, or work with a partner who will do so for you, your business will be less at risk.
2 Final Warnings
Trip Advisor Fake Complaints
You are likely too savvy to fall for this one, but just in case.
Beware emails containing a ZIP file or HTML attachment claiming to contain a TripAdvisor complaint. Clicking on the attachment (which you know you should not do) appears to open a browser with another button to click to read the complaint. That alone should set off alarm bells. Then if you do click again, an Excel sheet opens up with the option for you to enable an add-in–yet another red flag.
Remember to not let your curiosity get the better of your cybersecurity awareness training.
Beta Testing Apps
This heads up comes from the Internet Crime Complaint Center (IC3) division of the FBI.
“The FBI is warning the public that cyber criminals are embedding malicious code in mobile beta-testing applications (apps) to defraud potential victims. Beta-testing apps are online services for testing of mobile apps prior to official release. The beta apps typically are not subject to mobile operating systems’ review processes.”
They warn to look out for these red flags if you download one of these malicious apps:
- Your phone battery drains faster than usual
- Unauthorized apps gets installed on your device without your knowledge
- You get persistent pop up ads
Click here to read the public service announcement and get other safety recommendations.
Security Brief – August 1, 2023
Data Breach Stats and the SEC’s New Rule
Left image – Identity Theft Resource Center’s H1 2023 stats show that the number of data compromises in just the first half of 2023 is outpacing every year on record. 1,393 so far, when all of 2022 had 1802. Click the image to access the report.
Right image – IBM’s annual Cost of a Data Breach Report, reveals that the global average cost of a data breach reached 4.45 Million, an all-time high for the 18 year old report. The comprehensive analysis by the Ponemon Institute covers 553 organizations with actual data breaches. Click the image for more highlights from the report including the impact of AI and involving law enforcement.
SEC Rule
On July 26th, the Securities and Exchange Commission (SEC) adopted new rules that require public companies to disclose significant cybersecurity incidents within 4 days. You may have seen this on our LinkedIn page last week.
Brandon Quinn, a lawyer and technologist says, “These new cybersecurity incident reporting rules are set to take effect in December. However, smaller companies will be granted an additional 180 days before they are required to provide Form 8-K disclosures.
…This reporting requirement will no doubt for consistency spread in the coming years to other stock exchanges due to the financial and reputational impact of substandard Cybersecurity controls.
This will certainly raise Cybersecurity and Data Protection importance in the board room in budgeting decisions due to the potential liability of the board for any inaccurate disclosures.”
Why does all this matter to you?
The number of breaches continues to increase. The cost of identifying, mitigating, and trying to recover from breaches continues to increase. Regulations about the handling of breaches are being implemented.
Unless your business keeps no records and has no digital transactions, you need to protect yourself. What worked 5 years ago is not enough anymore.
You don’t need to spend a lot of money, but you do need to take security seriously. Enable MFA. Use proper access control. Invest in awareness education for your team. Get the latest best practices for data privacy, strong passwords, and digital hygiene, and follow them.
And let me know if you have any questions. My team and I are happy to help.
“Nearly One Quarter of All Emails are Considered to be Malicious”
That’s a headline on the KnowBe4 blog.
They go on to discuss Fortra’s latest quarterly report from July, Phishing Trends and Tactics: Q1 of 2023.
“The ripple effect from cybercrime-as-a-service launching a few years back has reached critical mass, where we’re seeing significant increases in the percentage of emails that are either clearly determined to be malicious (7.7%) as well as those suspicious enough that users are recommended to not engage with (15.9%).”
Now, this doesn’t mean 1 in 4 emails in your Inbox is malicious. As a client, you have spam filters and a variety of tested tools in place protecting you from known and suspected scam messages.
But some will always get through. And their numbers are increasing. So it is critical that you and your team know how to identify potential threats and handle them without jeopardizing your network.
Creative Criminals – The Latest Tactics
Barbie Scams
Researchers at McAfee report that scammers are taking advantage of the Barbie craze to lure victims.
“As Barbie makes her debut on the big screen, scammers are aiming to cash in on the summer blockbuster,” says Steve Grobman, McAfee’s Chief Technology Officer. “A rash of scams have cropped up online, including bogus downloads of the film that install malware, Barbie-related viruses, and fake videos that point people to free tickets—but lead to links that steal personal info with spyware instead.
Cybercriminals are always on the lookout for opportunities to make scams more attractive and believable. They often leverage popular and well-publicized events such as movie premieres, concerts, or sporting events to trick users into clicking on malicious links.”
Threads App Spoofs
Since Meta launched its Threads app to compete with Twitter, researchers at Veriti have observed hundreds of spoofed domains.
“In recent weeks, we have observed a surge in the creation of suspicious domains, with over 700 domains related to Threads being registered daily,” the researchers write. “These domains pose a significant risk as they can be used to deceive users, distribute malware, and lure unsuspecting individuals into downloading untrusted versions of the app.”
Malicious QR Codes
Computer security service Inky reports a new scam tactic that uses QR codes to trick employees out of their login credentials.
Love them or hate them, QR codes surged in popularity during the pandemic. We all got used to scanning them in restaurants and other businesses, and they haven’t gone away since.
Now Inky has multiple reports of emails that appear to come from within the company and claim to have some sort of issue to resolve such as account verification, 2FA, or password change. The message impersonates Microsoft and includes a QR code that you’re supposed to scan to go to a secure page to fix the issue.
This shouldn’t work. No one should receive an email and then have to use their phone to scan an image to follow a link. The link should simply be included in the email.
However, when we’re rushing, we don’t often think these things through. And this scam is particularly devious because, as Stu Sjouwerman, CEO of KnowBe4 says,
- “I’m not aware of any security solution that can follow a QR code-based URL to determine if the resulting URL is malicious or not.
- It shifts the actual threat action to another device – specifically one that has far less protections than a user’s endpoint.”
.Zip Domains
Researchers at Fortinet warn that cybercriminals are exploiting the introduction of “.ZIP” as a new generic Top-Level Domain (gTLD) to launch email attacks.
“Cybercriminals are always on the lookout for new opportunities and techniques to exploit, and the recent availability of ‘.ZIP’ domains for public purchase has unfortunately created such an opportunity,” the researchers write. “While the pool of new gTLDs has made detection more difficult, adding .ZIP is especially noteworthy given its more common use as a file extension for compressed files.
This new domain extension will likely create confusion, especially among non-technical users, giving [scammers] a new and potentially effective tool to add to their attack arsenals. In [these] campaigns, a common tactic is to make malicious websites appear as legitimate as possible. Using a .ZIP domain can add an air of authenticity to a fraudulent site. A user may mistake the .ZIP in the URL for a file extension, believing they are downloading a file rather than visiting a malicious website.”
On the Horizon
In addition to the scams described above (that you should look out for and share with others), this is one experts expect to see in the near future. It has not been reported yet, but if you’re prepared for it, you’re protected either way.
Google recently announced that they will begin deleting accounts that have been inactive for 2 years or more. The earliest this will start is in December. However, they have begun sending notifications out now.
Experts expect scammers to send their own spoofed notifications to try to steal login credentials. “It’s only a matter of time” they say.
How can you stay safe?
If you have a Google account, you can keep it active through any number of activities including reading an email, watching a YouTube video, using Google Drive, etc.
And if you get any urgent account alert emails, you should examine them carefully. Don’t click on any links in the email, and log into your account independently.
Security Brief – July 1, 2023
Seasonal Scam Alert
CISA, the Cybersecurity & Infrastructure Security Agency, has issued a warning about scams in the aftermath of natural disasters.
You can click the logo to view this warning (and others), but essentially, they want us all to be on alert for criminals using “email or malicious websites to solicit personal information by posing as a trustworthy organization, notably as charities providing relief. Exercise caution in handling emails with hurricane/typhoon-related subject lines, attachments, or hyperlinks to avoid compromise. In addition, be wary of social media pleas, texts, or door-to-door solicitations related to severe weather events.”
Welcome to Hurricane Season, where the weather is not even the biggest part of the disaster anymore.
3 Headlines
1. JP Morgan Fined for Deleting 47 Million Emails
The Securities and Exchange Commission (SEC) has just fined JPMorgan Chase 4 Million for deleting 47 million emails from early 2018.
The emails were deleted in 2019 from 8,700 inboxes belonging to as many as 7,500 employees in the retail banking division of the nation’s largest bank.
The SEC says the contents of some of the emails, which could not be recovered since they were permanently deleted, were requested in subpoenas for at least a dozen civil securities-related regulatory investigations.
JPMorgan claims the messages were mistakenly deleted due to miscommunications between the bank’s corporate compliance technology division and an outside vendor tasked with archiving and deleting communications dating back to the 1970s and 1980s. JPMorgan reported the deletions in 2020 when they discovered it.
The SEC order reports, “a member of JPMorgan’s compliance department acknowledged in an internal email after the deletion event was discovered that lost documents could relate to potential future investigations, legal matters and regulatory inquiries.”
JPMorgan has agreed to some sanctions from the SEC and has implemented some new policies. This is the third time the investment advisor has agreed to punishment for failing to preserve electronic records.
Why does this matter to you?
First, let me just say that I’m not going to debate whether the amount of the fine is hefty or a slap on the wrist. I’m also not going to speculate how the emails were permanently deleted and unrecoverable. Accidents can and do happen. What I want to point out is that the vendor did not get fined. JPMorgan did. JPMorgan’s reputation is getting hit for this, not the vendor’s.
Almost every type of business is subject to some sort of governance or oversight. JPMorgan apparently got this fine because the vendor failed to apply the proper retention setting (3 years) for those emails.
What I want for you and your business is to a) know your regulations and compliance requirements, b) put the proper safeguards and policies in place to protect yourself from situations like this, and c) communicate and overcommunicate with your staff about what’s happening with your company. Help them be invested so they will help keep you protected. And choose partners you can trust to be diligent and have your best interests at heart.
2. Massive Impersonation Campaign Imitates More than 100 Brands
Bolster, a software company that builds AI/ML technology to ‘protect regular citizens from bad actors on the internet,’ recently reported on a year-long campaign that impersonated 100+ of the most popular clothing, footwear, and apparel brands.
Names you know, such as Nike, Adidas, and Tommy Hilfiger, were all targeted. The investigation revealed an extensive network of brand impersonation scam sites, with over 3,000+ live domains identified.
And these sites were very well made, so much so that they were appearing as the second and third listing in search results and visitors were completing online shopping visits, providing credit card and other payment details.
So why should you care?
This is the perfect reminder that criminals are not the sloppy, typo-ridden Nigerian princes of days past. They have tools to look professional and to scale quickly.
And while your company may not be as big a household name as Nike to be targeted in this particular campaign, the ease with which these scams can be rolled out means that we are all targets.
So as users, we need to remember to be vigilant about the websites we visit. Look carefully at URLs for copycat domains, and never enter passwords or payment information on sites you do not independently navigate to.
As business owners, we can consider tools like reputation management monitoring so we find out quickly if something like this scam campaign is using our brand, or maybe work with a business like Bolster, though I have not used it and cannot vouch for it. More importantly, we need to keep educating our employees, stakeholders, and partners about the kinds of scams that are out there and how to recognize them so we don’t fall prey. Security awareness training cannot be a once-a-year email or webinar. It needs to be ongoing.
3. FTC Reveals 5 Most Common Text Scams
According to the FTC’s Consumer Sentinel database, text message scams cost consumers more than 330 Million in 2022.
Texts have an estimated 98% open rate, so knowing the top 5 scam types can help keep you and anyone you share this with safe.
- Copycat bank fraud prevention alerts – these messages may ask you to reply YES or NO to verify whether a transaction was authorized or give you a number to call ASAP about suspicious activity. Remember not to reply to unsolicited emails or texts, and always independently check any bank or other account when you get an unexpected alert.
- Fake gifts or rewards…for a small fee. If you really win a prize, you do not have to give your credit card information; legitimate companies will cover shipping.
- Phony package delivery problems – Even though you’ve received tons of mail with no problem, suddenly there’s an issue with a mysterious package. And when you try to get the details, they ask for payment information for a ‘redelivery fee.’ If you’ve already made a purchase and paid for shipping, you won’t have pay twice. And if someone sent you a gift that went out for delivery, you can rest assured they paid for shipping.
- Bogus job offers – These are sometimes fake ‘mystery shopper’ positions or opportunities to make money while driving around in a vehicle with ads on it. Other times, these texts target people who have posted their resumes on employment sites. No matter what the angle, never give your social security number or other private information to an unknown texter. Try to get the details on a company and job so you can confirm it by other means before giving any of your data away.
- Amazon impersonations – These texts ask you to verify a big-ticket order by calling a number in the message. If you do, you are connected with a fake Amazon rep who makes a mistake and refunds you too much. You are then asked to pay back the difference, usually via untraceable gift cards. Similar to other scams above, always check your accounts independently when you get any kind of alert like this. You’ll see there is no order in your account, and you can report the text to the FTC here https://reportfraud.ftc.gov/#/.
Try to remember that criminals will use any means available to reach you and separate you from your money or your data. It’s not just email anymore. It’s fake social media accounts, spoofed calls, and very often, texts.
2 Quick Stats
29,880
Check Point Research warns us that 29,880 domains related to holidays or breaks were created in May 2023. This is up 23% from last May. And last year, 1 in 83 of those live websites were malicious or suspicious.
Check Point Research also notes several scam email campaigns centered around summer vacation deals and approved leave requests that we should all look out for.
1 in 3
According to a June survey by PasswordManager.com, 1 in 3 job seekers has been tricked into applying and/or interviewing for a fake job in their searches over the past 2 years.
38% reported encountering fake job postings.
15% had personal information stolen.
9% had money stolen.
Good News
An attacker in the UK was convicted of man-in-the-middle cyber crimes.
A Man-in-the-Middle or Manipulator-in-the-Middle attack is when some form of tech is used to intercept communications, manipulate those communications for the criminal’s own devious purposes, and control a conversation between two systems, networks, entities or people.
According to the conviction details, in 2018, Ashley Liles’ employer became the victim of a ransomware attack. Liles’ role was IT Security Analyst, working alongside law enforcement to respond to and mitigate the attack. But Liles himself intercepted a board member’s email over 300 times, altering the payment details on blackmail emails in an attempt to have the ransom paid to himself. According to The Register, he also used an email address almost identical to the attacker’s to help pressure the company to pay up, though they did not.
Liles’ downfall was access logs showing that the board member’s email had been accessed from his home. Liles had tried to wipe his devices, but the proof was recovered. Despite the evidence, he maintained his innocence for 5 years until appearing in court in May. He will be sentenced in July.
Granted, this is an interesting twist that should be rare, but it’s a good lesson for any infosec professionals who may be tempted to join the dark side–you’ll get caught. And more importantly, this conviction reinforces the best practices we know that organizations should always maintain and audit security logs and that all members of a network–not just employees–should be educated with security awareness training to avoid falling victim to a ransomware attack in the first place.
Security Brief – June 1, 2023
Before we get into the security items, I want to note that today marks the official start of Hurricane Season. And as you may have seen in the paper, Adam Van Brimmer points out we usually ignore disaster planning until the Fall when storms tend to hit us. I want you to be as ready as possible, so please take advantage of the free disaster recovery resources and blog articles here on our website.
Seasonal Scam Alert
CISA, the Cybersecurity & Infrastructure Security Agency, has issued a warning about scams in the aftermath of natural disasters.
You can click the logo to view this warning (and others), but essentially, they want us all to be on alert for criminals using “email or malicious websites to solicit personal information by posing as a trustworthy organization, notably as charities providing relief. Exercise caution in handling emails with hurricane/typhoon-related subject lines, attachments, or hyperlinks to avoid compromise. In addition, be wary of social media pleas, texts, or door-to-door solicitations related to severe weather events.”
Welcome to Hurricane Season, where the weather is not even the biggest part of the disaster anymore.
AI News to Know – 3 Headlines
AI-generated Photo Impacts the Market
You may remember the Pope’s puffer jacket image and story from April. This is a bit more serious.
Last week an AI-generated image of an explosion near the Pentagon was posted on social media and shared widely, even by some verified accounts. Officials confirmed no such event had happened, but not before the markets dipped.
The good news is that no lasting damage was done.
The bad news is that this is going to happen again. And we need to know how to recognize these fake images.
Al Jazeera reports “Artificial intelligence still has a difficult time recreating locations without introducing random artefacts… This can result in people having extra limbs and objects that are morphed with their surroundings.”
You can verify buildings by comparing to Google Street View.
And we should all keep in mind that news doesn’t happen in a vacuum. One single report with no eye witnesses and no other corroboration should be treated with skepticism.
Lawyer Submits Fake Cases Cited by ChatGPT
A District Court case happening in New York right now is dealing with AI issues that will have rippling effects.
Simon Willison breaks it down here:
“The TLDR version
A lawyer asked ChatGPT for examples of cases that supported an argument they were trying to make.
ChatGPT, as it often does, hallucinated wildly—it invented several supporting cases out of thin air.
When the lawyer was asked to provide copies of the cases in question, they turned to ChatGPT for help again—and it invented full details of those cases, which they duly screenshotted and copied into their legal filings.
At some point, they asked ChatGPT to confirm that the cases were real… and ChatGPT said that they were. They included screenshots of this in another filing.
The judge is furious. Many of the parties involved are about to have a very bad time.”
Willison thinks there may be more to the story than we know right now, and he heard from other lawyers that this is happening in other places as well.
So what’s the lesson here?
Pay attention to the fine print. There is footer on every page of ChatGPT stating, “ChatGPT may produce inaccurate information about people, places, or facts.”
And as Cat always like to say, ‘Trust, but verify.’ I talked about some of the possibilities and limitations of AI in this video, and specifically pointed out the importance of fact checking and doing your own research.
I’m no lawyer, but I would have expected an associate of mine to independently confirm the cases he or she was going to name in a court filing or present to a judge.
AI Presents Political Peril for 2024
As if election season wasn’t already too long and aggravating enough, the Associated Press recently wrote about AI’s threat to mislead voters in the upcoming presidential election.
“Sophisticated generative AI tools can now create cloned human voices and hyper-realistic images, videos and audio in seconds, at minimal cost. When strapped to powerful social media algorithms, this fake and digitally created content can spread far and fast and target highly specific audiences, potentially taking campaign dirty tricks to a new low.
The implications for the 2024 campaigns and elections are as large as they are troubling: Generative AI can not only rapidly produce targeted campaign emails, texts or videos, it also could be used to mislead voters, impersonate candidates and undermine elections on a scale and at a speed not yet seen.”
The article includes disinformation examples we have already seen go viral, and these tools are only getting more sophisticated.
So what can we do?
First, we need to accept that deepfakes are becoming more common. They’re easier to make, and they are becoming more convincing. So we have to be more critical of everything we consume on social media.
Consider the source of who’s posting and whether there is verifiable information on other reputable websites, not just social media.
Look for indications of deepfakes, such as movements that look ‘wrong’ somehow or that don’t align with sound.
Confirm that something is authentic before sharing it, and report posts that you know are fraudulent. Helping to stop the spread of misinformation can go a long way in shutting down the deception.
Note: I’m not sharing these articles because I think AI is evil. It’s not, and I don’t. It’s a tool. I just want you to be aware of the ways it can be used against you — ideally before that happens — so you will recognize the warning signs.
Good News
A scam email and text operation in Madrid, Seville and Guadalajara has been taken down by the National Police of Spain with over 40 arrests.
KnowBe4 reports on the Los Trinitarios gang that is believed to have defrauded 300,000 people. And cybercrime was just their side gig. Their main criminal activity involves weapons and narcotics, which the cybercrime activity helped to fund.
As much as I want you to be aware of all the threats out there, it’s good to keep in mind that agencies all over the world are working tirelessly to stop them, too.
Security Brief – May 1, 2023
Pulled from the Headlines
Florida Principal
“I am a very smart lady. Well-educated. I fell for a scam.”
That was Dr. Jan McGee, the principal of a well-regarded charter school in Florida, speaking after she was forced to resign a few weeks ago.
She thought she was sending money to Elon Musk in exchange for an investment in her school.
The scammer pretended to be Musk’s partner and communicated with her for at least 4 months. She then wrote a check from the school’s account for twice the amount she had authorization for. Luckily, the check was stopped before it was cleared.
It is also reported that staff at the school had told her it was fraud.
Federal Reserve Chairman Powell
You’ve probably seen this in the news over the past few days. Fed chair Jerome Powell’s call in January was not with Ukrainian President Zelensky but actually with a Russian comedy duo.
There is video being circulated on the internet, but a spokesperson from the Federal Reserve says it has been edited, so they cannot confirm that it’s authentic. It could be a deepfake. They also say no sensitive or confidential information was exchanged during the 15-minute call.
The duo is known to be Putin supporters and has pulled this kind of prank before. The BBC reports Canadian Prime Minister Justin Trudeau, European Central Bank Chief Christine Lagarde, and Elton John have all been targets of the duo.
What does this mean for your business?
Scams don’t just happen to dumb, careless people. Everyone needs to be alert.
Put the right processes with checks and balances in place, and your organization can avoid a lot of headaches.
When the Math Doesn’t Quite Add Up – Interesting Stats
Get a high-level view of the cybersecurity landscape today with some interesting statistics from 2 recent reports.
- Fortinet’s 2023 Global Ransomware Report
This study seems to show that the majority of organizations say they take the ransomware threat seriously…yet fall victim nonetheless.
- 78% of cybersecurity leaders say they are ‘very’ or ‘extremely’ prepared to stop ransomware attacks.
- 91% say ransomware was either the ‘most important’ or a top 3 priority.
And yet
- 50% of organizations were a victim of ransomware in the last 12 months.
Plus, it’s worth noting that 67% of organizations were a target of a ransomware attack and 46% were targeted two or more times.
Fortinet also says scam emails remained the top initial attack vector in more than half of the attacks.
- Identity Theft Research Center’s Q1 2023 Data Breach Analysis
The image above shows overall stats from this report. Click on it to view a larger infographic and enter your info if you want to download the report. But here’s the main takeaway:
Many (which is too many) organizations do not know how to find the root cause of an attack resulting in a data breach. And if you can’t find the root cause, you can’t be sure you’ve addressed the vulnerability.
- In this report, Q1 saw 445 reported data breaches, down from 512 the previous quarter. That’s good.
- However, the percentage of breaches where there was no actionable information about the root cause of the compromise increased to 42%. That’s bad.
- And just for fun, 60% of the top ten data breaches reported could not identify a root cause.
As KnowBe4 explains, “Not knowing how threat actors got in leaves the door open for continued leverage of the likely persistence established to either attack again or sell off the access to another threat group.”
KnowBe4 also points out that “Even without knowing the root cause, there are really only three major initial attack vectors to address:
- RDP access (simple fix: get rid of any external remote access),
- vulnerabilities (a bit tougher, but patch and scan for vulnerabilities), and
- email attacks (address with a layered set of security solutions matched with a user base that is enrolled in continual security awareness training to ensure any malicious content that gets pass security solutions is spotted by users before they unwittingly help the attacker).”
What Does This Mean for Your Business?
Think about cybersecurity like that line from Law Abiding Citizen – “It’s not what you know; it’s what you can prove.”
Don’t just say cybersecurity is important to your business. Invest time and tools into protecting yourself.
Don’t just believe you have the right systems and protections in place. Test them.
Don’t just think your team knows how to handle fishy messages. Train them.
Don’t just know you should have strong, unique passwords and MFA enabled. Actually do it.
Before you wish you had.
Security Brief – April 1, 2023
Today is April Fool’s Day, and I still remember when a rubber band around the kitchen sink sprayer was the height of hilarious pranks.
Newspapers, radio, TV, and Google have pulled off some noteworthy hoaxes in good fun over the years, but plenty have backfired as well. And given the state of the world today with deepfakes and AI-created content that people can’t tell is real or not, it’s getting tempting to distrust everything every day of the year, not just April 1st.
But I’m not here to trick you. In keeping with the expanded scope I introduced last month, please find your revamped security brief below to stay ahead of threats, scams, and upcoming security changes that may impact your business.
Awareness is the key to protection, so arm yourself and your colleagues with this information.
Thank you.
– Chuck
 Seasonal Scam Alert
Seasonal Scam Alert
Be on the lookout for tax-related scams.
* Emails with a fake W-2 link
* Threats of your social security number getting cancelled
* Emails about liens on your assets
Click the IRS logo to get more info direct from the source.
Banking Failures Increase Risk of Scams
As you most likely know, two large banks, SVB and Signature, failed a couple of weeks ago. A third bank, First Republic, remains on the brink of failing as well. Given the global visibility of the situation, bad actors will take advantage to steal information and ultimately money.
Whether you previously banked with SVB, Signature, or First Republic, these scams will be non-discriminant. Exercise increased vigilance to protect yourself and your organization from possible scams and fraud.
What Does This Mean for Your Business?
While we have not seen specific attacks impact customers yet, we encourage you to take extra precautions in light of this news.
Here are some best practices and tips to keep in mind always, but especially over the next few weeks as the threat of email and text scams are likely to be on the rise:
- The FDIC does not send unsolicited email notifications or offers to increase deposit insurance. If you are a customer of SVB or Signature Bank, correspond with them via the FDIC Claims Portal.
- Check that your account information is accurate, and keep an eye out for unexpected changes.
- If you receive emails regarding changes to vendor deposit information, call a representative you’ve worked with in the past to confirm the information before making any changes.
- Avoid using a search engine when visiting websites that hold sensitive personal information. Criminals pay for sponsored links that show up at the top of search results and look legitimate but will redirect you to their spoofed sites. Manually type in the URL or set a browser bookmark.
- Verify the website’s secure domain in your browser address bar to ensure you’re on the intended website.
- Use strong and unique passwords and use multi-factor authentication whenever possible.
Remember, as the general public is questioning the stability of their financial institutions, scammers are taking advantage of the situation by sending fraudulent messages in an attempt to capture your personal or account information.
In general, if someone presents you with information designed to make you afraid and then proposes that you give them money or personal information to make that fear go away, be extremely suspicious and ALWAYS verify first.
 Microsoft Security Updates
Microsoft Security Updates
These are a couple of notable updates that will impact Microsoft 365 users in the near future.
Microsoft Exchange Server
Bleeping Computer explains the new security feature being rolled out:
“Microsoft is introducing a new Exchange Online security feature that will automatically start throttling and eventually block all emails sent from ‘persistently vulnerable Exchange servers’ 90 days after the admins are pinged to secure them.
“The new system’s primary goal is to help Exchange admins identify unpatched or unsupported on-prem Exchange servers, allowing them to upgrade or patch them before they become security risks.
“However, it will also be able to throttle and eventually block emails from Exchange servers that haven’t been remediated before reaching Exchange Online mailboxes.”
The Exchange servers that will be impacted by this include on-premise or hybrid environments that a) have reached their end of life such as Exchange 2007, Exchange 2010, and, as of April 11th, Exchange 2013 or b) are significantly behind on updates for known vulnerabilities, such as Exchange 2016 or Exchange 2019 servers that remain unpatched.
Check your server’s health. Keeping it up-to-date and protected will keep this new feature from impacting you and your team at all.
Microsoft OneNote
With rollout beginning in late April and expected to be complete by the end of May, OneNote will block embedded files with dangerous extensions. These will be the same extensions considered dangerous and already blocked in Word, Excel, Outlook, and PowerPoint.
This change only affects OneNote for Microsoft 365 on devices running Windows. It will not affect OneNote on a Mac, OneNote on Android or iOS devices, OneNote on the web, or OneNote for Windows 10.
Like the Exchange update above, this is intended to protect users and networks. When it has been rolled out to you, the change you’ll see is a popup that lets you know an administrator has blocked from opening the embedded file with a dangerous extension. Currently you get a warning popup and can click OK to continue opening the file anyway.
If the file is from a trusted sender and you need to open it, you may be able to save it to your local device and open it there. You can also ask your IT team to check it out for you, which we’re happy to do and recommend just to be safe.
Ransomware Reminders
The following US businesses and agencies have been hit by ransomware attacks in the past month. Why does this matter? Because it’s not just one industry. It’s not just one attacker. It’s not just one tactic used to get the criminals access. We ALL need to be prepared.
- DISH Network, including Sling TV and Boost Mobile
- US Marshals
- City of Oakland, CA
- Tennessee State University
- Carats and Karats (gem, jeweler, appraiser business in Hawaii)
These are just the ones in the United States. And the ones making headlines.
According to independent research company Vanson Bourne, “73% of organizations polled by a new study reported being hit with at least one successful ransomware attack in 2022 – and 38% said they were hit with two or more.”
News coverage of the Hawaii business attack reported that “even her online medical records were infiltrated.”
Roseann Freitas of the Better Business Bureau Hawaii says, “We saw a huge increase of 39% of scams being done via text messaging.”
The battle against online scams will only get tougher as technology advances, and fake emails and texts look more like the real thing.
“You know how it used to be the misspellings, the incorrect grammar? Well, you have AI, you have ChatGPT — all of those resources that can help them write and make it look legitimate,” said Frietasks.
3 Final Thoughts
Speaking of Artificial Intelligence (AI), here are 3 different angles to keep in mind.
Voice Cloning Scams
The Federal Trade Commission (FTC) has issued a warning about family emergency scams. You get a call from a loved one who claims to be in trouble and need money. What makes this so difficult is that the voice really sounds like your family member.
“A scammer could use AI to clone the voice of your loved one. All he needs is a short audio clip of your family member’s voice — which he could get from content posted online — and a voice-cloning program. When the scammer calls you, he’ll sound just like your loved one.”
So how can you tell if a family member is in trouble or if it’s a scammer using a cloned voice?
Always be suspicious when someone asks for money to be wired or sent via gift cards. Don’t trust the voice. Call the person who supposedly contacted you and verify the story. Use a phone number you know is theirs. If you can’t reach your loved one, try to get in touch with them through another family member or their friends. And report any scams to the FTC.
The Pope’s Puffer Jacket [Video 3:28 min]
Did you see or hear about the photo of the Pope in a white puffer jacket last weekend? It went viral (‘mega-viral’ some outlets called it).
This CNN segment features a tech expert discussing what happened, some of the dangers of AI, and some suggestions for how we can spot created images. Watch it here: https://www.cnn.com/videos/business/2023/03/27/pope-puffer-jacket-fake-ai-generated-photo-cnntm-cprog-sot-vpx.cnn.
Content Credentials [Video 5:36 min]
This video from CBS News also starts with the Pope’s jacket, but it shows what companies like Microsoft and Adobe are doing to help us identify AI-generated images and videos.
See the tough-to-tell examples and unprecedented partnerships here: https://www.cbsnews.com/news/pope-francis-puffer-jacket-fake-photos-deepfake-power-peril-of-ai/.
Security Brief – March 1, 2023
Did you know it’s been 4 years since I started sending these top scams messages? I hadn’t realized it was that long.
And I’m proud to say that the feedback you’ve given me shows it has been worth doing. So thank you for that.
But now I think you’re ready for more. Well, different, not really more. I’m not going to send you anything more.
What I’m going to send now is still one single email on the first of the month but with an expanded scope. It will no longer be limited to the top 3 scams my team and I are hearing about or dealing with.
And that’s not because they’re no longer relevant. It’s because no matter how sophisticated the delivery methods get, the principles of handling the scams we talk about remain the same. And I don’t want you to get bored hearing the same old advice. You’re probably sick of it already. And there are many other security risks out there.
So going forward I -may- include a noteworthy scam. But I will also include critical software warnings, relevant business trends that can impact your costs such as cyber insurance, and other items that fall under the security brief umbrella.
I hope you continue to find it useful, and I’d love to hear your feedback. Reply to me anytime, good or bad.
From my perspective, the better prepared you are, the more protected you are. And awareness is still the key to protection. I just want to help broaden that awareness.
Arm yourself and your colleagues with the information below.
Thank you.
– Chuck
 Seasonal Scam Alert
Seasonal Scam Alert
Be on the lookout for tax-related scams.
* Emails with a fake W-2 link
* Threats of your social security number getting cancelled
* Emails about liens on your assets
Click the IRS logo to get more info direct from the source.
Ransomware Recovery in the Wild
Who: Suffolk County, NY (government)
Impact: Most populated county in the state outside NYC’s 5 boroughs. Attack impacted civil service title searches, purchasing contract searches, Medicare direct deposits, workers’ compensation direct deposits and more. Websites down for the municipal government, county police department, mass transit system, and more.
Brief Timeline:
September 8, 2022 – Ransomware attack in County Clerk’s office forced systems offline
October 2022 – Systems certified as clean from malware
December 2022 – Specialists could begin to access computer systems in the County Clerk’s office
February 24, 2023 – Online services began to be restored and systems began to be reconnected to the Internet
Cost: 5.4 M dollars on investigation and recovery
My Take: Imagine the City of Savannah website down for 5 months, its employees unable to access computer systems for 3 months. How would they work? What open projects or information would they have lost? How could they continue to serve residents, visitors, and businesses? If you normally pay utility services online, would you have to use your time to go to an office in person and wait in line? What if you had a permit or zoning application in progress when this happened? How would it impact the courts, sanitation, or police operations?
Government is a well-known target for criminals because they have historically been slow to update their systems. Often this is due to time and money. But take a look at the time and money an attack costs above. Proper cybersecurity is critical. Invest in setting it up properly now or you’ll pay far more later.
Good News
KnowBe4 shared this headline that made me smile:
“Business Email Compromise Gang Gets Jail Time for Stealing Millions”
They mostly operated in Europe, specifically targeting France, but no matter where in the world they are, it’s good to know the criminals are getting caught.
Lonely at the Top…and More Vulnerable
The Wall Street Journal recently covered how changes in leadership at a company can make it more vulnerable to attack.
“A change in leadership in an organization is often a time of uncertainty, confusion and insecurity.
It’s also the perfect time for cybercriminals to strike.”
Their research showed that the likelihood of someone falling for a malicious email is higher during times of leadership change. And that hackers know it and often time their attacks to take advantage of such changes.
Makes sense, right? If you’re the new leader, you don’t know everyone yet. A well-spoofed email could easily seem legitimate.
On the flip side, if you’re an employee and you know there is a change at the top, you could understandably fall for fake announcements, policy change messages, or otherwise unusual requests.
Clear communication is key.
If you consistently make sure your team knows the standard methods of official company communication, plus the proper procedures for request approvals and raising the red flag on anything out of the ordinary, your times of transition should not turn into times of successful attacks.

Common Question & My Answer:
Should I click the Unsubscribe link on an unwanted email?
If you know me well enough, you know my answer is going to be, “it depends.”
I don’t say it to be vague; there are just various factors to consider.
- If the message is from a company or subscription you know–and that isn’t setting off warning bells that it might be spoofed–yes, it’s safe to click the Unsubscribe link. In fact, all businesses should include a safe and easy way to unsubscribe. Companies that require you to send your information to a mailing address or call to unsubscribe could be in violation of the CAN-SPAM Act.
- if you think the message is a scam or you’re not sure of the sender, no, don’t click the unsubscribe link. You could end up verifying that your email address is valid and start to receive even more junk or attacks.
A couple of other options to keep in mind are that your email service may offer their own ‘unsubscribe’ feature that you can take advantage of, and you can usually set up filters that automatically send certain senders or subject lines to your Junk or Trash folder.
When you’re at work, you can always ask my team to check an email out for you. And when in doubt at home, you can always delete.
Top 3 Scams – February 1, 2023
 RMM Software Refund Scam
RMM Software Refund Scam
What kind of dastardly criminals would pose as the people who are supposed to protect your network, people like me and my team?
Unfortunately, a lot of them.
Help Desk-themed scams have proven successful in the past and will continue to do so until none of us falls for them anymore. This time, it was employees at the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Multi-State Information Sharing and Analysis Center (MS-ISAC) offices who were targeted.
The attack came in as emails to employees, appearing to be from some kind of IT Support. The messages were designed to get employees to download remote monitoring and management (RMM) software. The kicker is that the RMM software was legitimate. But the criminals used the software fraudulently. (Remember that warning in December?)
“They first connected to the recipient’s system and enticed the recipient to log into their bank account while remaining connected to the system. The actors then used their access through the RMM software to modify the recipient’s bank account summary. The falsely modified bank account summary showed the recipient was mistakenly refunded an excess amount of money. The actors then instructed the recipient to ‘refund’ this excess amount to the scam operator,” CISA reported.
What can you do to protect yourself?
- Always learn the official ways in which legitimate businesses and services will contact you. For example, we email tickets to and from support@infinityinc.us. If you were to receive a message from ITsupport@infinityinc.us, it would be understandable to think that’s us, but it would be a trick.
- Use extra care any time someone asks you to download something, even the ‘help desk.’ Check with a coworker or call to confirm before clicking. There are definitely times when we need to ask a client to download a program or click on a link, and we always prefer you to be safe rather than sorry.
- Remember to be suspicious of anyone asking you to log into your bank account. Most legitimate businesses communicate issues of refunds via letters, not emails and software downloads.
- Make sure everyone is aware of this breach. Share with them the importance of strong, unique passwords for their own protection and yours. Let them know to expect targeted attacks.
- Stay alert for red flags. Scammers keep getting more sophisticated, but you can train yourself to notice when a message or request feels ‘off.’ Trust that feeling and confirm it’s legitimate before taking any action.
 Super Bowl Betting Scams
Super Bowl Betting Scams
The Better Business Bureau’s Scam Tracker is seeing increased reports from people who accidentally placed bets with scam sports betting websites or apps.
The BBB often sees more online betting scams around significant events like the Super Bowl.
Scammers will get you to place a bet online, then make up excuses when you go to redeem money.
Some scammers will want you to deposit more money to get your winnings. The BBB warns against falling for that.
Scam websites often have a letter misspelled in the domain name and re-direct you to a false site to capture your information.
“If you’re betting online, make sure that the website that you’re going to is for the correct company that you want, not something that’s just similar enough,” said BBB of Greater Kansas City Operations Manager Nikolas Reese.
How can you avoid these scams?
- Nationwide or global events will always attract scammers. They know they have the potential to reach a lot of people with minimal work. From sporting events to natural disasters to the pandemic that continues to provide criminal fodder, items that get a lot of news coverage should remind us to be extra careful. Check closely for misspelled URLs or spoofed links. And be wary of clicking on ads.
- Don’t bet. Just kidding. But not really. Sports betting is not currently legal in Georgia. Bills to change that keep going through the General Assembly, but none have passed yet. Sources tell me you can legally bet online in Georgia, but make sure you confirm that and use a reputable site or you’ll be out more than just money.
 AI-Improved Scams
AI-Improved Scams
ChatGPT is everywhere right now, isn’t it? The Artificial Intelligence-powered chatbot has people equally thrilled at the possibilities or hopelessly convinced it will put us all out of our jobs.
Well, here’s another angle on it.
“Cybersecurity researchers from Check Point Research (CPR) have observed the tool being used by cybercriminals to improve – and sometimes build from scratch – dangerous malware and ransomware.
…To make matters even worse, some of the authors seem to be complete newbies to the world of programming, signaling that the tool might be used to dramatically lower the barrier to entry into cybercrime.”
Horrified yet?
Now, don’t get me wrong. I don’t want you to be terrified. Technological advancements are exciting and offer so much promise.
But any tool can be used for good or for bad. I want you to be aware.
I’ve used this monthly email for a long time now to show you examples of scams that work, to give you ways to prevent them from working, and, maybe most importantly, to indicate where they might be heading so you can avoid future scams, too.
Reading about criminals using ChatGPT in these ways tells me their evolution of tactics and messaging could speed up exponentially.
It’s critical that we all build up and share our cybersecurity awareness.
So how can you stay safe from this?
- As I’ve said many times before, it’s not the malicious email, link, or attachment itself that creates the problem. It’s what we, as people, do with it. A scam that gets to its target but doesn’t get opened or clicked on fails. Nothing happens. Crisis averted. It’s our behavior that makes the difference, and we can control our behavior.
- Start with the basics of recognizing red flags and build on that. Check sender names. Check sender email addresses. Pay special attention to unsolicited requests or anything that seems ‘urgent.’
- Trust your gut when something seems suspicious even if you’re not sure why.
- Call or chat or confirm information independently online before taking any action.
- Send any questionable messages to your IT team to check. We have the tools to do this safely and are happy to do so.
- Cybercrime is big business. It makes a lot of money for a lot of people. It’s not going to go away, and we’re not all going to disconnect from our online lives and live in caves. So we need to deal with it. And we can do that by sharing information and helping each other stay safe.
- If you’d like to know whether there’s more you could be doing to protect yourself and your business, give me a call. From security policies to scam simulation programs, there are a variety of options to explore.
Top 3 Scams – January 1, 2023
 LastPass Breach Risk
LastPass Breach Risk
You’ve probably seen the recent headlines. LastPass, one of the most popular password management tools, was hacked this past August. The investigation is ongoing, and an update last month revealed that customer information was accessed.
Now, before you say, ‘Don’t you keep telling me to use a password manager?!’ Yes, I do. And I will continue to recommend it over bad habits such as saving passwords to a text file on your computer. Or even worse, using the same password for multiple accounts.
Think of it like this: St. Joseph’s/Candler suffered a massive breach in 2021. But you don’t say, ‘that’s why I don’t use hospitals.’
These hacks are a fact of life and of business now. What’s important is how we protect ourselves through tools, education, and best practices.
Back to the hack, LastPass recommends businesses review and update their passwords, review their security measures, and stay vigilant for social engineering attacks on their accounts.
Why? Because LastPass says that although users’ plaintext passwords were not accessed, the hackers did get the following:
- website URLs for the users’ stored passwords
- end-user names
- billing addresses
- email addresses
- telephone numbers
- company names
- IP addresses from which customers were accessing the LastPass service
- AND LastPass user’s encrypted passwords for each stored logon.
Now the encryption protection is strong as long as the user’s master password for LastPass was strong. Strong meaning at least 12-characters long, contained some complexity, wasn’t an easy-to-guess password, and was not used on any other site or service.
But the unencrypted information means an attacker can specifically target a potential victim using information not known to the general public and other hackers.
For example, with a list of the websites that someone logs onto, a criminal can craft specific emails that pretend to be from that website. They could include the user’s name and address. Add their phone number to that and consider how each additional detail adds to the impression that the social engineering email is real. Each included detail increases the percentage of people who will become victims.
Criminals can also blast entire companies pretending to be the LastPass user who had their information breached. Or they could use IP addresses to find remote workers with lax home computer security to try to gain access to business networks.
There are many ways they can try to use this data. You need to be prepared.
What can you do to protect yourself?
If you’re a LastPass user, check the strength of your master password. If it doesn’t meet the criteria above, then change it AND all the other passwords you were storing in LastPass.
For your business,
- Make sure everyone is aware of this breach. Share with them the importance of strong, unique passwords for their own protection and yours. Let them know to expect targeted attacks.
- Send employee awareness campaigns – test scam emails that employees can respond to in real-time and get immediate feedback to learn from. We offer this for clients and send them to our own team.
- Consider dark web monitoring to be notified of compromised accounts.
- Use your IT team to check any messages you are the least bit suspicious about. We offer a one-click reporting tool in Outlook that makes this simple for everyone, and we’re always happy to check something for you.
- Enable MFA on every account that allows it. I bet you were hoping I would stop harping about MFA this year, but it is too easy and too effective to not use it wherever possible.
 Cable and Internet Provider Scams
Cable and Internet Provider Scams
Now, I’m not including this scam because Comcast’s Xfinity is raising prices this month or because my team and I often get mixed up with them. They are, and we do, but that’s not why this is here.
This also isn’t about Clearwave Fiber digging up your yard to lay new cable or newcomer Coastal Communications planning to bring faster Internet to the Islands. You’ve probably seen headlines or social posts about both of those recently, too, but they’re not behind this scam either.
These companies being in the news just means you may be more susceptible to this scam.
The FTC recently issued an alert about provider imposters reaching out with an offer to lower your monthly TV, cable, or internet bill. People across the country have reported calls, texts, and voicemails.
One woman told this story to the radio station:
“We just received a scam phone call yesterday addressing my husband by name and claiming to be Cox Cable. We had just canceled Cox cable TV two or three days before, which this caller [knew] about. They offered a 40% discount if we reconnected. I inquired about the cost, but before he would give me the cost, he wanted to verify our account and asked for my mother’s maiden name. That’s when the red flag went up. I said, ‘May I call you back in 15 minutes’, with the intention of checking out the phone number and calling Cox Cable. The caller replied that he’d call me back. Once I did a Google search of the number and called Cox Cable, I realized it was, in fact, a scam call. The caller didn’t call back. I followed up with a call to my older parents to warn them about these types of scams.”
The FTC shares another example:
“You get a phone call, recorded message, or text with an offer to lower your monthly payments. The caller — or the person who picks up when you call the number they give you — says you need to “prepay” part of your bill to qualify. They tell you to pay using gift cards because they’re partnering with a company for a promotion, and to call them back with the gift card number. Once you do, they collect that and other personal information over the phone.”
It all sounds so tempting and almost reasonable that many people are giving away their information and paying a much higher price.
How can you avoid these scams?
- Never give out your personal, account, or payment information to someone who contacts you out of the blue and asks for it. Legitimate businesses you have accounts with already have this information and don’t need to call you to verify it.
- Don’t implicitly trust caller ID. Scammers can easily fake caller ID so it shows a company’s name or phone number. And never call back a number from a recorded message or listed in an unexpected email or text. Look up the phone number on the company’s official website.
- Remember that gift cards are for gifts. If anyone tells you to pay with a gift card, or to buy gift cards for anything other than a gift, it’s a scam. You’ll lose your money, and you won’t be able to get it back.
- Try not to be fooled by a great-sounding deal, especially if it is urgent. Scammers want you to act without thinking and will try to prey on your emotions. Get in the habit of pausing. Give yourself time to think and consider whether any of the red flags above are there, trying to warn you.
 SVG and XLL Malware Deliveries
SVG and XLL Malware Deliveries
This last one is less about a specific scam and more about the tactics to look out for.
You already know to be suspicious of unsolicited attachments. But you also know from previous scams that criminals can sometimes send messages from people you know, sometimes that even appear to be part of an existing email thread. And that can make you think the attachment is trustworthy.
Please be careful, however. And confirm via phone or chat that any attachment you were not expecting is legitimate before opening.
Criminals are evolving to smuggle malicious HTML code inside SVG files, which are vector, or image, files. They are also using XLL add-ins to deliver malware through Microsoft documents more frequently now since Microsoft has begun phasing out support for VBA macros, which have commonly been exploited.
Without getting into the technical details of how each of these tactics work, essentially the malicious code gets downloaded or activated when the attachment is processed.
Talos, one of the largest commercial threat intelligence teams in the world, explains the SVG angle:
“HTML smuggling can bypass traditional network defenses and is increasing in frequency. Once a victim receives the email and opens the attachment, their browser decodes and runs the script, which then assembles a malicious payload directly on the victim’s device.”
They also talk about XLL:
“XLL files can be sent by email, and even with the usual anti-malware scanning measures, users may be able to open them not knowing that they may contain malicious code.”
The attachments used in these attacks can be webpages, pdfs, and nearly any kind of Office document. The messages may be about invoices, budgets, ‘the file you requested,’ or even no description at all, counting on your curiosity to open it.
It is critical that we all train ourselves not to.
So how can you stay safe from this?
- As I said above, the best thing you can do whenever you get an unexpected attachment is to check with the sender before opening it. And checking cannot be via email in case that sender has been compromised. Reach out to the sender via phone call, chat, or text.
- You can also send any questionable messages to your IT team to check. We have the tools to do this safely and are happy to do so.
- Pay attention to any feelings you might have that something is wrong even if you can’t put your finger on it. Many of the hijacked email threads that criminals use to send these attachments are not current conversations. Look at the dates. If the message is a reply to an email from a year ago, be suspicious. If the tone sounds unlike the sender, be suspicious.
- Remember that any attachment has the potential to be hiding malicious code. If you are not 100% sure it is safe, check before opening
Top 3 Scams – December 1, 2022
Notable Trends
Security vendor Talos recently released their Q3 Incident Response trend report. It identifies the use of “valid accounts to gain initial access, especially in cases where accounts were misconfigured, not disabled properly, or had weak passwords” as the most common initial infection vector.
The report also points out that “a lack of MFA remains one of the biggest impediments to enterprise security. Nearly 18 percent of engagements either had no MFA or only had it enabled on a handful of accounts and critical services.”
Both of these factors are controllable, meaning those incidents were preventable. Click the image to see the whole report.
 Beware of Malicious Installers
Beware of Malicious Installers
 Microsoft’s Security Threat Intelligence team has been tracking a threat actor that uses emails and other methods “to distribute malicious installers for legitimate applications, including TeamViewer, Microsoft Teams, Adobe Flash Player, Zoom, and AnyDesk.”
Microsoft’s Security Threat Intelligence team has been tracking a threat actor that uses emails and other methods “to distribute malicious installers for legitimate applications, including TeamViewer, Microsoft Teams, Adobe Flash Player, Zoom, and AnyDesk.”
The attacks began as links in malicious ads, fake forum pages, blog comments, or through scam emails. They have evolved into using website contact forms, legitimate software depositories, and Google Ads to distribute their links.
Microsoft describes these attacks as showing “a pattern of continuous innovation, with regular incorporation of new discovery techniques, defense evasion, and various post-compromise payloads, alongside increasing ransomware facilitation.”
What can you do to avoid these scams?
Downloading programs and software updates is a regular part of our lives now. But it should still be done with extreme caution.
- Never download something you did not independently navigate to unless you know, trust, and confirmed with that sender that it is valid. For example, you know and trust your Support team. And it wouldn’t be crazy for them to tell you you need a new version of Zoom or Teamviewer, right? But ask yourself if we would send you a link to download or if we would just install it for you. And keep in mind that any sender can be spoofed, including us. So always verify in some way before downloading.
- Microsoft recommends implementing mail flow rules and safe links security tools to help prevent these campaigns from reaching you in the first place. They also encourage limiting local admin privileges. But the most effective prevention they recommend is what you’re doing right now: gaining awareness of the threats and learning how to handle them.
So think of a download as a stray dog. It might be the sweetest, most friendly, most lovable creature in the whole wide world. Or it might try to rip your arm off. Unless you know for sure, protect yourself.
 Unusual Login Scam
Unusual Login Scam
 More than 22,000 mailboxes were targeted in this recent Instagram impersonation scam. And it’s a good one to learn from even if you don’t have Instagram because it will most likely be replicated and used for other platforms.
More than 22,000 mailboxes were targeted in this recent Instagram impersonation scam. And it’s a good one to learn from even if you don’t have Instagram because it will most likely be replicated and used for other platforms.
Security researchers at Armorblox describe how this scam starts as an email with the subject line ‘We Noticed An Unusual Login, [user handle]’.
“The email looks like a notification from Instagram, notifying recipients about unusual login activity on his or her account. The body of the email coincides with the spoofed email subject and sender, with details around a login from an unrecognized device. This targeted email attack was socially engineered, containing information specific to the recipient – like his or her Instagram user handle – in order to instill a level of trust that this email was a legitimate email communication from Instagram. The victim is prompted to review the details provided and secure his or her account if the login attempt was not legitimate.”
Clicking on the link in the email takes you to a well-made but fake landing page. It shows the fake login location with buttons below for you to click ‘This wasn’t me’ or ‘This was me.’
It’s the kind of notification we are all used to seeing now, often when we travel. The kicker is that if you click on ‘This wasn’t me,’ the next page is where they harvest your credentials. Instead of a reset password link or fields for a new password and confirmation, they want your old password, too.
How can you protect yourself?
- Always stop yourself before entering credentials on a page you did not independently navigate to. Always.
- Try to pay attention to emails like this that are designed to make you feel fear and react without thinking. None of us wants to deal with a hacked account. But that’s why it’s even more important now to slow down when we get messages like this. Carefully check the spelling of sender names, emails, and URLs. And open a new tab or window to check your account rather than clicking the link. Especially when it leads to a page asking for both old and new passwords.
 Clone Phishing
Clone Phishing
 “Imagine receiving a legitimate email from a brand you know and trust. Later you receive the same email again, only this time the sender explains they forgot to include additional recipients or information.
“Imagine receiving a legitimate email from a brand you know and trust. Later you receive the same email again, only this time the sender explains they forgot to include additional recipients or information.
Without knowing the obvious signs of clone phishing, you trust the email as authentic and accept the sender’s reasoning without a second guess. After all, the email’s content and context give you no reason for suspicion. It turns out, however, that this second email isn’t legitimate, but a clone of the original message, intended to deceive you into clicking a malicious link or downloading a harmful attachment.”
This is how researchers at Vade Secure describe the new scam tactic of cloning emails. And it doesn’t end there. These cloned messages are often sent out to numerous recipients. Whenever someone falls for it, they access that individual’s contacts and forward them the cloned email, spreading the reach of the initial attack. And once they have penetrated a company’s network, they can use additional campaigns to target other employees, customers, or partners.
“Highly deceptive and devastating, especially to organizations like SMBs,” they call it.
So how can you stay safe from this?
- To start with, the usual rules apply. Carefully check the sender name and email for any misspellings or red flags. Then check the message itself. If anything at all about the language or tone seems ‘off’ to you, trust that instinct.
- Verify with the original sender before clicking any links or opening any attachments. Pick up the phone or send a quick chat. If you are the sender, email services like Outlook give you the option of Recalling and Resending a message so you can simply replace the original email rather than forwarding or replying and looking like this clone tactic. And you can usually communicate company-wide with Teams or another chat tool to say whether or not it is legitimate.
- Don’t be afraid to report messages to us to check for you. Tools like PhishMe make it as simple as a click right in Outlook to let us know you think a message is suspicious. We can test it in a secure environment and let you know if it was real or if you just saved the whole company from an attack.
Top 3 Scams – November 1, 2022
Special Notice
Friday, November 11th is Veterans Day. A national holiday is a common excuse for criminals to target people all across the country, so please tell your veteran loved ones to be alert for scams.
The Federal Trade Commission (FTC) issued a Consumer Alert just days ago reminding veterans that they do not have to pay to file claims. Click the image for details and links to legitimate veteran resources.
 Neverending Pandemic Scams
Neverending Pandemic Scams
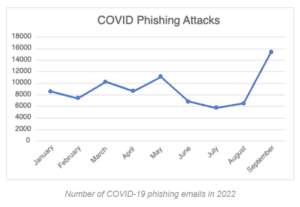 Security researchers at email security vendor Inky have spotted a new wave of email attacks using familiar tactics from during the middle of the pandemic.
Security researchers at email security vendor Inky have spotted a new wave of email attacks using familiar tactics from during the middle of the pandemic.
As you can see in the chart to the right, pandemic scams spiked in September of this year. One particularly slippery angle they recently detected combined brand impersonation, credential harvesting, and Google Forms abuse tactics.
Targeting businesses, this one begins as an email claiming to be a grant application from the Small Business Administration (SBA). The email looks real enough and may have text directly copied from legitimate SBA messages.
The Apply Now button takes you to a Google Form that could also be convincing since it has language copied from the real grant application and questions that are very similar to actual questions the SBA asks. However, submitting the form sends all of your information to the criminals.
What can you do to avoid these scams?
As the Inky researchers described above, this scam is slippery because of the effort the criminals put in to copy from the real SBA and the fact that they are using Google Forms, meaning the link is real and shouldn’t trigger email filters.
That said, there are still ways you can determine this is a scam and stay safe.
- Anytime you receive an offer out of the blue, whether for a loan, grant, or surprise winnings, do a little independent research. A couple of clicks on the SBA website would show that they are no longer accepting applications for pandemic relief loans or grants.
- Inky also points out a few grammatical errors in the message and form questions that should alert you to the likelihood that it is a scam.
- With regard to the form itself, always stop yourself before submitting personal information such as SSN, date of birth, or even your driver’s license number unless you are 100% certain it is safe. Often that will only be in a password-protected portal or highly secure system, not a Google Form that anyone can create and share to collect data.
 Geek Squad Renewal Scam
Geek Squad Renewal Scam
 In another recent alert from the FTC, criminals are impersonating Geek Squad, Best Buy’s tech support service. This scam starts as a text or email, and its goal is to get you to call a number rather than click a link.
In another recent alert from the FTC, criminals are impersonating Geek Squad, Best Buy’s tech support service. This scam starts as a text or email, and its goal is to get you to call a number rather than click a link.
The message claims you are about to have a membership renewed for hundreds of dollars unless you call within 24 hours. If you call the number provided, you may be convinced to give the caller remote access into your computer. This won’t remove anything, but it will allow them to install malware or spyware on your machine so they can steal your data.
You may also be asked for your banking information so they can issue you a refund. Instead, they’ll show you a fake transaction that is ‘accidentally’ more than you should have been refunded. Then they’ll ask you to pay the overage in gift cards or other untrackable funds.
How can you protect yourself?
- Don’t be lulled into thinking it’s not a scam just because there isn’t a link to click. Like the Paypa| scam from September or the phone scam statistics I sent in July, taking these attacks offline and over the phone has been growing steadily more popular and successful.
- You can also foil these scammers by looking for the business phone number online, not using the number they include in their message. A call to the real company would clear everything up.
- And remember to always be suspicious of emails or texts that make you feel a sense of urgency. Most legitimate businesses give you ample warning before renewing or changing your paid subscriptions. A message claiming you have to take action immediately or within 24 hours should always raise red flags.
 Social Security Administration Scam
Social Security Administration Scam
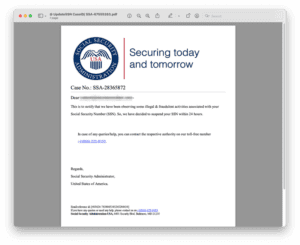 Security researchers at Inky are also warning us of a recent influx of scams about social security numbers.
Security researchers at Inky are also warning us of a recent influx of scams about social security numbers.
They arrive as an email appearing to be from Social_Security_Administration.
“All of the SSA brand impersonation emails INKY caught contained a PDF attachment that opened in the form of a letter with SSA-branded elements. [T]he letter starts with one of SSA’s widely used logos alongside a short tagline. It’s an image that looks sharp and is readily available online. In the body of the letter, the sender claims that illegal & fraudulent activities have been associated with the recipient’s SSN and, as a result, their SSN will be suspended in 24 hours. A phone number is given to resolve this issue.”
The following examples are some of the subject lines that were used to seem authentic (by including ID numbers) and urgent enough to get people to open the messages.
- Hi [redacted_email address] SSN going to be suspended (Case ID- SSA-75214260).
- Hi [redacted_email address] SSN found under suspicious activities, Docket No. 79851704.
- Fraudulent activity detect in your SSN Account.. Case id:15383815
- Suspicious activity detect in your SSN account. Docket id:13161614
- Your SSN id will be discontinued from service due to suspicious activity. Case id:18191915
- Your SSN id shortlisted for intimation. Case id:20101028
Inky explains some of the psychology behind these attacks’ success:
“What do you worry about the most? If you’re like most Americans surveyed on the subject, at the top of your list are money, the future, and political instability. On their own, each of these topics has the power to create a pretty hefty amount of anxiety. Combine them, however, and you have the perfect recipe for mayhem.
We all have reason to worry. The annual rate of inflation is the highest it’s been in 41 years. The Federal Reserve has raised interest rates five times thus far in 2022 – to the highest they have been since 2008. And, an uneasy feeling about Social Security has been brewing for years, with funds expected to be depleted by 2034.”
So how can you stay safe from this?
- A quick visit to the Social Security Administration website shows one of the most common questions they get is about being contacted about a problem with your SSN. The first sentence in their answer says, “If there is a problem, we will mail you a letter.” Along with other information, they remind us that “Caller ID or documents sent by email may look official but they are not.”
- Remember to stop yourself anytime you read an unsolicited message that evokes any kind of emotion, whether that’s fear, anger, etc. Scammers like to make their targets feel emotional so they act quickly, without thinking things through.
- Look carefully at the sender and the language used in the message. Legitimate government email addresses should end in .gov, and professional messages should not have grammar mistakes.
- Always be suspicious of unsolicited messages with attachments. In this case the attachment is not flagged by email filters because it does not have any malicious links in it. The scammers want you to call, not click. But if you dial that number, you’re not calling the official government agency.
- Always search for contact information independently.
Top 3 Scams – October 1, 2022
Since 2004, October has been recognized as Cybersecurity Awareness Month. It originated from the Department of Homeland Security and has grown from a national to an international effort. Infinity is proud to be a Champion of it.
Why should you care about it?
In simplest terms, because our modern (online) lives put us at risk.
Everything is connected now. From our phones with all our emails and accounts, to our social networks, to our smart home devices and the world at large.
Unless you’re living off the grid without email and Internet somewhere (in which case, you wouldn’t be reading this), then you are connected.
And those connections need to be protected.
So this month we’re focusing on 4 ways you can do just that.
- Enable multi factor authentication on every account that offers it. This simple step to enter a code or click one extra time has been proven to be 99% effective against account takeover attempts.
- Run your software updates. Whether it’s on your phone, your computer, or even your smart TV, get out of the habit of hitting ‘remind me later.’
- and 4. Find here with additional details.
Here’s the extra I mentioned. It’s a tipsheet that basically sums up what I try to illustrate in these emails each month. I know these examples can get long sometimes, and they may not be as fascinating to you as they are to me. That doesn’t mean I want you to stop reading them, of course, but this sheet is succinct guidance you can print out and refer to at any time.
 Post Hurricane/Disaster Scams
Post Hurricane/Disaster Scams
In June, we heard it from the Federal Trade Commission (FTC). And just 2 days ago our own Attorney General issued another warning for consumers to be on the lookout for price gouging and scams in response to Tropical Storm Ian.
“Unfortunately, con artists will try to take advantage of those impacted by a weather-related disaster or individuals looking to donate to their neighbors in need,” said GA Attorney General Chris Carr. “As we continue to pray for the families and communities in the path of Tropical Storm Ian, we want to remind consumers of the important steps they can take to protect themselves from price gouging and scams. We know this is a difficult and scary time for many, and anyone who is artificially increasing costs on the backs of hardworking Georgians will be held accountable.”
It is fairly easy for a scammer to set up a realistic-looking website, copy a logo, or create a name that sounds very close to that of a well-known charity. Many scammers offering work will even come to your door.
It’s important to be careful when responding to ads or posts on social media or crowdfunding sites, as these are not always legitimate – even if they have been shared or liked by your friends.
It is very important to take your time to review an organization thoroughly before you give someone your money.
What can you do to avoid these scams?
CISA, the Cybersecurity and Infrastructure Security Agency, says to exercise caution in handling emails with hurricane-related subject lines, attachments, or hyperlinks. Remember that events that impact a large area or a lot of people will always be a hot topic for criminals.
The Attorney General’s Consumer Protection Division offers the following tips to help consumers avoid scams and other fraud in the aftermath of a storm.
- Steer clear of any contractor who asks for full payment up-front, only accepts payment in cash, or refuses to provide you with a written contract.
- Avoid door-to-door offers for home repair work. Instead, ask friends and neighbors for referrals.
- Be skeptical of any contractor that offers to pay your insurance deductible or offers other no-cost incentives, as these can be signs of fraud. Always talk to your insurance company before committing to any storm-related repairs or inspections.
- Ask contractors for references and check them out.
- Check with the Better Business Bureau to see if there are any complaints against the business.
- Ensure that the contractor has the required licensing and/or affiliation, especially for work involving tree removal and treating water damage or mold. Not all contractors are required to be licensed by the state, but you can see those that are at sos.ga.gov.
- Legitimate contractors should be able to provide the following:
- Business license
- General liability insurance
- Workers compensation insurance
- Written manufacturer warranties
- Written labor warranties
 New Browser-in-the-Browser Technique
New Browser-in-the-Browser Technique
This is another example of how the criminals are getting more sophisticated in their tactics. A new credential-stealing technique pops up looking like a new window used for authentication; only it’s actually part of the initial malicious site.
Browser-in-the-Browser (BitB) takes advantage of sites that use a pop-up window for user authentication. With a little bit of code, conveniently available in a kit, hackers can make a scam window which at first glance is indistinguishable from the authentic one.
Researchers at GroupIB report messages with attractive offers being sent to lure victims to a scam page with a login button.
Almost any button on the bait webpages opens an account data entry form mimicking a legitimate window. It has a fake green lock sign, a fake URL field that can be copied, and even an additional window for two-factor authentication.
Currently, this is only being reported by gamers on Steam, but with the common use of third-party authentication (such as Google, Facebook, Microsoft 365, or any cloud-based directory service) – this same technique could soon be used to trick users into providing business credentials.
How can you protect yourself?
- Ideally, you don’t have to worry about the following ways to identify this as a scam because you do not click on links in unsolicited messages. That said, there are ways to see if the popup window is real or not.
- First, look at your taskbar. Did another browser window open? If not, then this isn’t a real popup window. (Keep in mind we are not talking about new tabs in the same browser window. This scam appears as its own window popup.)
- Try to change the size of the popup window. Dragging the corners or clicking the maximize button will not work in this kind of scam.
- Check for inconsistencies in fonts and design between the ‘real’ window and the popup.
- Test the padlock symbol in front of the URL on the popup. Authentic browsers display SSL certificate information when you click on the lock.
 Dark Web Email Scam
Dark Web Email Scam
The Federal Trade Commission (FTC) has recently issued a Consumer Alert about emails claiming your data is for sale on the dark web.
People report getting messages that can include some of the ‘stolen information,’ such as all or part of the person’s Social Security number, date of birth, and driver’s license number.
The FTC wants everyone to know that these emails themselves could be the trick.
Granted, if you use a credit monitoring service or a credit card with a company that monitors the dark web, then this kind of message could be real. However, this is also an effective scam scare tactic.
Kelle Slaughter, the FTC’s Identity Theft Program Manager, says, “These emails may contain links and people may be subject to click them which could download malware, and compromise personal information on their computers.”
So how can you stay safe from this?
- Remember to stop yourself any time you read an unsolicited message that evokes any kind of emotion, whether that’s fear, anger, overwhelming sympathy, etc. Scammers like to make their targets feel emotional so they act quickly, without thinking things through.
- Look carefully at the sender name and address. If it seems like a legitimate company you should be receiving this kind of information from, then navigate to their website independently of the email and log in.
- Don’t be fooled by the ‘information’ of yours included in the message. Far too much of our data is publicly available, and the millions of data breach records can easily fill in the rest.
- However, the FTC recommends treating the message as real and acting accordingly to better protect yourself. 1. Change the passwords on your email accounts. Email accounts often are the weak link in online security because password resets for other accounts go to your email. 2. Check your credit reports. After securing your accounts, make sure nobody has opened new accounts using your information. Visit AnnualCreditReport.com to get an annual free credit report from each of the three nationwide credit bureaus, Equifax, Experian, and TransUnion. Through December 2023, you can get a free credit report every week from each of them at the website.
- Consider signing up for dark web monitoring so you’ll know from a reputable source whether your data is at risk. This can often be helpful for businesses as well as individuals.
Top 3 Scams – September 1, 2022
In this line of work, we see so many scams. And while many are evolving and sometimes even creative, there are often 3 factors in common that you can use to identify a suspicious email, text, or phone call.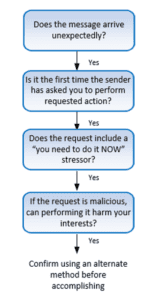
The first 3 boxes in this diagram from KnowBe4 show these red flags:
- The message is unexpected/unsolicited.
- You’re being asked to do something out of the ordinary from that sender.
- There is urgency to perform the action ‘now.’
If you ask yourself these questions, and the answers are ‘yes,’ then ask yourself the last question before taking any action such as clicking a link, opening a pdf, etc.
And if that answer is yes, too, then report the message to us. We’ll check it out.
Healthy suspicion can protect you.
 ‘Inflation’ Scams
‘Inflation’ Scams
The Federal Trade Commission (FTC) has recently issued consumer alerts about a variety of rising cost issues. As they point out, “Across the country, people are worried about high prices impacting their budgets. And scammers are taking notice.”
- Government grants for home repairs or unpaid bills
- Investment opportunities
- Enticing job offers
- Utility bill shutoff threat
These scams are showing up in emails, calls, and texts.
“They might say they’re from the government and giving away grant money for home repairs or unpaid bills. Or they have an investment that’s guaranteed to deliver quick and high returns. Or they know of a high-paying job that’s yours as soon as you pay a fee or give them your personal information. [Or] you get a call or text from someone pretending to be your utility company. The caller or text says you owe money (which is a lie). The scammers then send you a text—sometimes including your utility company’s logo— with a QR code and tell you to scan it at a Bitcoin ATM to make a payment or your service will be disconnected.”
What can you do to avoid this?
In each of these situations, the scammer is reaching out to you, which should immediately make you suspicious. And in the case of the utility payment scam, no legitimate company will text you that your services are about to be shut off. They are required to notify you in writing and offer some sort of repayment plan. In addition,
- The government won’t get in touch out of the blue about grants. It won’t call, text, reach out through social media, or email you. In fact, real government grants require an application, are completely free to apply for, and are always for a specific purpose.
- All investments have risks. No one can guarantee a specific amount of return on an investment, or that an investment will be successful.
- Honest employers won’t ask you to pay to get a job. If someone claims you can make a lot of money in a short time with little effort — you just need to pay for starter kits, “training,” or certifications — that’s a scam.
- Only scammers demand nonstandard payments. Real utility companies won’t demand payment by Bitcoin, gift cards, or money transfer through a company like MoneyGram or Western Union. Only scammers do.
Remember that if an offer seems too good to be true, it probably is. Look into it independently–do a quick Google search–before taking any action.
 PayPal Invoice Scam
PayPal Invoice Scam
A new scam has been reported by numerous security experts, using invoices from PayPal, with an updated spin.
If you prefer to listen than read, go to the 23:25 mark of this Secplicity podcast to hear about this scam.
Here’s how it works. A criminal sets up a PayPal account. From there, they use the PayPal platform to send fake invoices that either a) spoof an existing company or b) claim you have a pending charge to your account. In either case, they want you to call to dispute the charge.
That’s the new twist. These criminals take advantage of PayPal’s system to send real emails with real PayPal links but put their own language and phone number in the notes. So when you get this invoice and know you didn’t sign up for anything from Norton or Microsoft, you’d naturally call to dispute the charge.
If you do call, you’ll be greeted by some generic ‘customer service’ rep who listens to you and ultimately suggests you download a remote administration tool so they can ‘resolve’ your issue.
Spoiler alert: Any download will only cause you even more issues.
As Brian Krebs explains, “today’s scammers are less interested in stealing your PayPal login than they are in phishing your entire computer and online life with remote administration software, which seems to be the whole point of so many scams these days. Because why rob just one online account when you can plunder them all?”
How can you protect yourself?
- Accept that criminals are evolving their tactics. Up until now, you may have known to check the logo and sender in an email to make sure it wasn’t a bogus PayPal message. But since this scam is using the real platform, you need to be alert to other dangers.
- Log in to your account independently from that message to see if the invoice is legitimate. If not, then once you’re in the real system, you can contact Customer Service through the proper channels. Do not use phone numbers in unexpected emails that are designed to make you anxious or worried. Look up the phone number online if you don’t want to log into your account.
- Never download tools or programs to help resolve an issue with your account. PayPal or your bank or Microsoft, etc. can manage everything they need to within their own system; there is nothing they require on your computer.
 Rising Robotext Scams
Rising Robotext Scams
Did you know the Federal Communications Commission (FCC) has a Robocall Response Team? Well, they do. And now they are warning Americans that robotexts may be surpassing robocalls as a tool for criminals.
“Like robocalls, texts can be spoofed to mask the originating number and make it appear that the text is coming from a number you’re more likely to trust. Spoofers may opt for a local number, or impersonate a government agency, such as the IRS, or a company you’re familiar with. Scammers use these methods to get you to respond to a text.”
A recent FCC consumer alert lists some of the approaches you may see:
“Scam text message senders want you to engage with them. Like robocallers, a robotexter may use fear and anxiety to get you to interact. Texts may include false-but-believable claims about unpaid bills, package delivery snafus, bank account problems, or law enforcement actions against you. They may provide confusing information–as if they were texting someone else, incomplete information, or utilize other techniques to spur your curiosity and engagement. Some scammers may be after your money, but others may simply be trying to collect personal information or confirm that a number is active for use in future scams.”
One of the members of my team recently shared a text that appeared to be from TeleService. You may have seen it on our LinkedIn page.
TeleService is a legitimate tool used by BMW to send automatic car service needs and schedule appointments for you. But the person who got the text doesn’t have a BMW.
In another example last week, multiple employees at Axios, the news website, got fake messages appearing to be from the company’s president. Not everyone on staff received the message, but each one who did had it addressed specifically to him or her.
A security researcher from Sophos said it’s a scam tactic he has seen before and that a human takes over after someone responds to the initial robotext. He also said he hadn’t seen several employees at the same company be targeted like that before.
So how can you stay safe from this?
- If you don’t already, start thinking of your text messages just like your emails. Use the questions from the diagram at the top of this message to check for red flags.
- Remember not to click on unexpected links. And don’t provide any information about yourself or your accounts via text.
- Make sure your phone’s operating system is kept up-to-date as bug fixes and security improvements are rolled out.
- The FCC says you can forward unwanted texts to SPAM (7726).
- Check with your phone provider on ways to block or report unwanted messages.
Top 3 Scams – August 1, 2022
 Hijacked Google Ads
Hijacked Google Ads
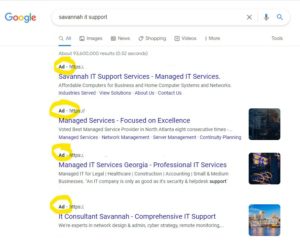 If you typically click on the first link that comes up in your search results, you may want to reconsider.
If you typically click on the first link that comes up in your search results, you may want to reconsider.
Researchers at Malwarebytes, a software company that aims to protect network endpoints, warn about a recent trend that has gone mainstream. Criminals posting malicious ad links is not new. But effectively targeting major brand names in this way is.
They describe it like this:
“The threat actors are abusing Google’s ad network by purchasing ad space for popular keywords and their associated typos. A common human behavior is to open up a browser and do a quick search to get to the website you want without entering its full URL. Typically a user will (blindly) click on the first link returned (whether it is an ad or an organic search result).
Let’s say you want to load YouTube and type ‘youtube’ instead of entering the full address ‘youtube.com’ in the browser’s address bar. The first result that appears shows ‘www.youtube.com’ so you are likely to trust it and click on it.”
The first link, however, may be an ad–a link someone paid to show up first.
If you click on the malicious ad in this scam, you will be redirected to a page that makes you think your computer has been infected. If you click on any of the prompts for help there, or call the ‘support’ phone numbers, you are contacting the criminals.
So what can you do to avoid this?
This is a tricky scam. It works on 2 very common human behaviors – 1. searching for a website rather than typing the URL directly into the address bar and 2. clicking on the top link in the search results.
- Bypass this threat by typing the website you want directly into the address bar or by bookmarking the site and navigating to it using your bookmarks.
- If you aren’t sure what the address is, go ahead and search, but be careful to look for the bold “AD” in front of any search results. Businesses pay to show up there, but criminals do, too. And they are cloaking and redirecting their links to appear as the website you want. Scroll down to links that do not have Ad in front of them.
- If you click an ad link and suddenly see warnings on your computer screen that you have been compromised or that there is a security alert, do not click anything. If it’s your work computer, call your IT team. If it’s your personal device, disconnect your Internet and restart. Remember that companies like Microsoft and Google are not going to call you, so if you suddenly receive any phone calls offering ‘tech support,’ they are also a scam.
 Beware of Unknown USBs
Beware of Unknown USBs

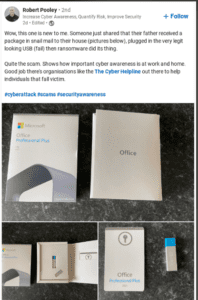 Penetration testing teams – the people you hire to check your security systems for weaknesses – have used USB drives as a vulnerability tool for years.
Penetration testing teams – the people you hire to check your security systems for weaknesses – have used USB drives as a vulnerability tool for years.
As KnowB4 computer security consultant Roger Grimes says, “My favorite trick, when I was a full-time penetration tester, was to label the dropped USB keys with the company’s name and include a malicious file labeled “Pending layoffs”. Employees could not wait to plug those in and open the file.”
Now, you may be aware enough to be suspicious of a random USB drive or key lying in your work parking lot or in the lobby. But what if it came to you in the mail as part of a Microsoft or other software company package?
That’s the new scam researchers are warning about.
Examples include free software downloads and ‘updated’ devices that users should install because of security compromises. They arrive in fully branded packaging that may be real and repurposed or just very successfully copied.
No matter what the premise is though, installing the USB will install whatever malicious code or scam the criminals put on it.
How can you protect yourself?
- Never plug in a USB to your computer that you aren’t 100% sure is safe. It doesn’t matter if you picked it up off the ground, received it in the mail, or were handed it at a trade show. Unless you know exactly who the USB came from and what is on it, do not expose yourself and your company to the risk.
- Give any unknown USBs to your IT team to check for you. It’s absolutely possible that a colleague left their USB on the conference table. But ask them or get the USB checked. Do not plug it in thinking you’ll take a quick look and find out who it belongs to.
- Keep in mind that criminal tactics will continue to evolve. The USB lying in the parking lot may be obvious, but the one sent in the mail that looks like it’s really from Microsoft is not. These attacks do happen, and we need to stay alert for them.
 Giveaway Scams
Giveaway Scams
 A recent scam circulating through WhatsApp motivated Heineken to issue a formal statement. They were not, in fact, giving away 5,000 coolers of free beer in honor of Father’s Day.
A recent scam circulating through WhatsApp motivated Heineken to issue a formal statement. They were not, in fact, giving away 5,000 coolers of free beer in honor of Father’s Day.
But how many people do you think saw the fake competition, versus how many saw the official statement? According to onlinethreats.com, the scam spread “like wildfire.”
And before you dismiss this as irrelevant because you don’t even use WhatsApp (neither do I), consider how many online competitions you have entered or seen. The Savannah Morning News website frequently promotes giveaways, for example. They are an effective tool for businesses to get new leads and build engagement. And they can be inexpensively distributed to large quantities of people via email, text, and social media.
All a criminal has to do is set up a webpage or form for capturing the data they want.
So how can you tell which giveaways are legit?
- Read the fine print. I know, I know. None of us wants to do this. But inside the terms and conditions, or even within a social media contest post, legitimate businesses typically spell out how and when you may be contacted, as well as by which social handle or email address. If this kind of information is missing, you’re probably looking at a scam.
- Stop if you see the contest asking for any banking or financial information. As the FTC explains in this article, real contests and giveaways do not require you to pay.
- Use caution if you feel any kind of urgency or pressure to enter. Official contests often, if not always, have a deadline for entering, but scams will be pushier. They’ll make it seem like you have to ‘enter now’ due to limited quantities or an expiring time so you rush.
- Take a moment to check the sponsoring company’s official website to see if the giveaway is mentioned. Alternatively, search for the company name and ‘giveaway’ or some related term to see if results come back warning you of a scam.
- As always, stop and think before clicking on any unsolicited links you get via email, text, or served to you online.
Top 3 Scams – July 1, 2022
Summer Stats
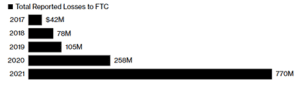 Now that we’re halfway through the year, many reports are being released with full 2021 data. I’m including some quick statistics for you here to stay alert on scams already covered in the past.
Now that we’re halfway through the year, many reports are being released with full 2021 data. I’m including some quick statistics for you here to stay alert on scams already covered in the past.
- Fraud losses on social media last year were 18 times higher than in 2017.
More than 95,000 people in the US reported fraud initiated on social-media platforms in 2021, with losses totaling about 770 million, according to the Federal Trade Commission. In 2017 that number was 42M. See chart above.
Scams tied to romance were the second-most profitable on social media, after investment fraud, the agency’s data show. And it’s important to remember this can happen to anyone.
“The younger crowd likes to think they are more tech savvy, but there are a huge amount of the younger crowd being victimized,” said Kathy Waters, founder of Advocating Against Romance Scammers. “All of them say, ‘I never thought it could happen to me.’”
- According to TrueCaller’s 2022 report, a staggering 39.5 billion USD was lost to phone scams in America over the past 12 months.
1 in 3 Americans (33%) report having ever fallen victim to phone scams, with 20% more than once.
Scam texts have more than doubled over the previous 3 years with males over 65 years old being the biggest targets.
The scams communicated over text vary ranging from consumer issues like changing cable TV providers, to cyber security issues, to data breach notifications.
- Researchers at Abnormal Security report vendor impersonation overtaking CEO fraud as a tactic.
“In January 2022, the number of attacks impersonating third parties surpassed those impersonating internal employees for the first time,” the researchers write. “This trend has continued each month since, with third-party impersonations making up 52% of all BEC attacks in May 2022.”
Abnormal Security notes that this tactic allows threat actors to target organizations of all sizes.
“We’ve seen this shift to what we’ve termed financial supply chain compromise for a number of reasons,” the researchers write. “Most notably is that the approach gives threat actors a plethora of additional trusted identities to exploit. Even the smallest businesses likely work with at least one vendor, and larger companies have supplier numbers in the hundreds or thousands. And while the average employee has some level of familiarity with the company’s executive team, they may not have that same awareness of the organization’s entire vendor ecosystem—particularly in larger enterprises. Further, the vendor-customer dynamic has an intrinsic financial aspect to it, which means emails requesting payments or referencing bank account changes are less likely to raise red flags. All of these factors combine to make a perfect environment for exploiting end user trust.”
 Hiring Scams
Hiring Scams
In today’s climate of employee shortages and competitive recruiting, it’s more important than ever to make sure the person you’re hiring is truly that person. HR personnel and all hiring managers should be especially alert for these 2 scam tactics.
1. The FBI warns of an increase in “the use of deepfakes and stolen [identities] to apply for a variety of remote work and work-at-home positions. Deepfakes include a video, an image, or recording convincingly altered and manipulated to misrepresent someone as doing or saying something that was not actually done or said.”
These reports are primarily for IT jobs, but you can expect them to spread if scammers find them to be effective. And the goal of the imposters, according to Gizmodo, could be a “desire to steal sensitive information as well as a bent to cash a fraudulent paycheck.”
2. Contrast Security reports attackers using job-listing and networking sites such as LinkedIn to identify potential targets. Then they hide malware in documents claiming to be resumés and CVs.
Experts at KnowB4 explain, “As part of their job, HR employees frequently interact with people outside of the organization and are more likely to open external files.”
So what can you do to avoid this?
To address the deepfake issue, the FBI recommends paying close attention to the actions and lip movements in a video to see if they line up with the audio. Things like coughs and sneezes that do not show in the video can be a strong indication that you’re seeing a deepfake.
In addition, you can use the tips below from an MIT Media Lab research project that was designed to help people identify manipulated videos. These tips can also be used on the video and audio you see on social media to make sure you’re getting the true story.
- Pay attention to the face. High-end DeepFake manipulations are almost always facial transformations.
- Pay attention to the cheeks and forehead. Does the skin appear too smooth or too wrinkly? Is the agedness of the skin similar to the agedness of the hair and eyes? DeepFakes are often incongruent on some dimensions.
- Pay attention to the eyes and eyebrows. Do shadows appear in places that you would expect? DeepFakes often fail to fully represent the natural physics of a scene.
- Pay attention to the glasses. Is there any glare? Is there too much glare? Does the angle of the glare change when the person moves? Once again, DeepFakes often fail to fully represent the natural physics of lighting.
- Pay attention to the facial hair or lack thereof. Does this facial hair look real? DeepFakes might add or remove a mustache, sideburns, or beard. But, DeepFakes often fail to make facial hair transformations fully natural.
- Pay attention to facial moles. Does the mole look real?
- Pay attention to blinking. Does the person blink enough or too much?
- Pay attention to the size and color of the lips. Does the size and color match the rest of the person’s face?
Test your skills on the MIT project website, DetectFakes.
To address resumés and other attachments with malware hidden in them, continue or even increase your employee awareness training.
- Make sure your team uses caution when handling unsolicited messages. Be immediately suspicious of ZIP file attachments, and never click “Enable content” in a Microsoft document unless it is an expected file from someone you trust and have confirmed that they sent it.
- Take advantage of your IT partner and ask us to check attachments before opening them.
- When you set up phone interviews, let the call come through the office and be routed to you; do not give strangers your direct cell phone number.
Dmitri Alperovitch, chairman of the Silverado Policy Accelerator, warns of texts that contain implants that use the iMessage protocol to send spyware to your smartphone. He says nothing will show on your device when it happens, and he recommends getting in the habit of rebooting your cell phone every night because they can be brushed off fairly easily, at least sometimes.
“Oftentimes when they land on the device, while the device is running, they can collect information, they can communicate, they can activate the microphone, but once you reboot, the flag goes away, and unless you’re retargeted, you’ll be free of the malware.”
 Monkeypox and Mail Order Brides
Monkeypox and Mail Order Brides
As we’ve seen again and again, globally trending news will likely become the topic of the next scam message in your inbox.
Researchers at Mimecast, an IT security company, report scam emails using Monkeypox to target businesses. The messages impersonate companies in an attempt to trick employees into visiting phony health safety sites that steal their information. The subject line tries to grab your attention as something official and important, and the message claims to be about Monkeypox safety awareness training that you need to complete.
Another scam seems to combine the headline news about Ukraine with the success of romance scams. Researchers at Bitdefender, a cybersecurity technology company, report, “in the past couple of weeks, spammers have been targeting internet users with a mixed bag of online dating opportunities such as mail order bride services and dating platforms where single western men can meet Ukrainian women.”
These ads and messages want you to click a link that will take you to their dating platform. That, of course, is not secure and asks for personal information such as your date of birth to set up an account. Once you do, you’re redirected to another platform where you can interact with these beautiful women. For a price. Emails, chat times, even unlocking photos has a cost. And guess who gets your financial information when you enter payment details.
How can you protect yourself?
- Start with the basics, checking your sender and subject line carefully. Researchers reported a spelling error in the Monkeypox subject lines they saw, which should set off a red flag. And when emails seem to come from within the company, make sure the name matches the email. Or that it is the exact right department email such as hr@ versus humanresources@.
- Pick up the phone and call or chat to confirm mandatory training at your company before clicking a link. Especially if that’s different from how you normally receive important information or training.
- Stop yourself any time you click a link and are asked to enter credentials. It is always safer to navigate independently to any login page.
- When it comes to online dating sites, stick to the ones you can verify are secure.
- Check the URL to make sure it is spelled correctly and not hosted in another country.
- Avoid clicking on an online ad altogether and navigate to the advertised site on your own.
- Always think twice (or three or more times) before entering any payment information online. There are many reputable websites, but there are far too many scams.
 MGM Hotels Breach
MGM Hotels Breach
This last one is different in that it is not about a specific scam but a general and very serious warning.
The VPNMentor security research team reports that a previous breach has now been released in full, for free, on Telegram, an app accessible to anyone.
The breach includes 142 million records of personally identifiable information (PII) of MGM Hotels customers prior to 2017. Different pieces of the breach had been exposed previously, and the data as a whole had been sold on the dark web, but now it is all public.
They estimate at least 30 million people had their data leaked with the following information:
- Full names;
- Postal addresses;
- Over 24 million unique email addresses;
- Over 30 million unique phone numbers;
- Dates of birth
KnowB4 explains why this is concerning:
“If you received a medical bill that had your birthdate, phone number, and name mentioned in it, you’d at very least give it a moment of your time to determine what the bill is, whether you owe it, etc. And you probably wouldn’t think that it was a scam, but – at worst – a mistake, right?
“This information could be used for [email, SMS, and voice] scams intent on using the compromised personal data to gain the trust of a potential victim in order to trick them into giving up banking and credit card details, credentials, and more.
“And given the actual breach occurred two years ago, people whose information is contained in the breached data aren’t expecting such attacks.”
So how can you stay safe from this?
- If you’ve never stayed at an MGM Hotel before 2017, you are not impacted by this particular breach. It’s just one of many, however. And it’s disturbing to wonder about the motivation behind releasing stolen records on public platforms like this. If you think you might be on this list, you should reach out to MGM.
- To best protect your online data, always use strong, unique passwords for every login. Your password won’t prevent that account’s network from being hacked, but it will protect all your other accounts from being accessed. Get tips and resources on good password hygiene here.
- Implement Multi Factor Authentication (MFA) on any accounts that allow it. That extra verification step takes just a few seconds but makes an exponential difference in your protection.
- Something else you can do, though it’s not preventative, is checking your email, phone number, and even your passwords on the haveibeenpwned site. Their search can tell you if your information has been included in a breach so you can address those accounts.
Top 3 Scams – June 1, 2022
Video: Pranks Destroy Scam Callers – Glitterbomb Payback
I’m starting this month’s message with a video for 2 reasons.
- This video is impressive, and one of my guys shared it with the team. It’s long, about 26 minutes, but it’s fast-moving, entertaining, and informative. It’s by the creator of the glitterbomb and backyard squirrel maze, and it’s worth the watch.
- Reading about these scams can be sort of vague or theoretical if they have never happened to you or a loved one. ‘They’re just emails, right? Why can’t people just delete them?’ Well, these cyber criminals are big business. They keep evolving, and they like to target people who aren’t even aware such scams exist. This video includes actual experiences people have had, yet it’s still creative and funny. And it hits a very satisfying note of revenge against scam callers and the terrible damage they wreak.
 Preparing for Hurricane Season and Storm-Related Scams
Preparing for Hurricane Season and Storm-Related Scams
Today kicks off the 2022 Hurricane Season. We have a lot of disaster recovery resources on our website, but a recent alert from the Federal Trade Commission (FTC) warns everyone to not only prepare for the weather but also to be on the lookout for the scams that follow.
“Hurricane-related threats also come in the form of scammers who use those weather emergencies to cheat people. Some of the most common weather-related frauds and scams include people who promise to help you with clean-up or repairs, but disappear with your money; those who pretend to be FEMA or other government agencies; people who promise you a job – if only you pay to get it; and those who promise you a place to rent – if only you wire them the money to get the place sight unseen.”
These scams will come in the form of emails, texts, and online ads or listings. Stay vigilant and follow the FTC recommendations below to stay safe.
The FTC recommends the following precautions. You can also download and print this infographic for your colleagues or community groups.
For clean up and repairs:
- Ask for IDs, licenses, proof of insurance, and references. See if local contact info is on their trucks. Check with state and local consumer protection offices for complaints.
- Get more than one estimate. Ask people you trust for recommendations.
- Read the contract carefully. Make sure all promises are in writing and that you understand what you’re signing.
- Never pay in cash. And never make the final payment until the work is done and you’re satisfied with it.
For imposter scams, people pretending to be government officials, safety inspectors or utility workers who say immediate work is required:
- Ask for IDs. If anyone asks you for money or your financial information, like your bank account or credit card number, it’s a scam.
- Know that FEMA doesn’t charge application fees. If someone wants money to help you qualify for FEMA funds, it may be a scam.
For fake job postings or rental listings:
- Be alert for up-front payment demands. You should not have to pay to apply for a legitimate job. You should also not have to provide a security deposit or rent before you’ve signed a lease or for the ‘opportunity’ to see a property.
Be on the lookout for disaster-related charity scams as well.
- If you get an email or text – especially if it is the saddest, most urgent need to pull on your heartstrings – do not click any included links. Navigate independently to legitimate charity websites and only make donations on secure websites.
- If someone calls you, do not give any personal information, and do not donate over the phone. Get the charity’s information and look it up yourself online.
 Fake Overdue Tax Bills
Fake Overdue Tax Bills
The Resecurity HUNTER team, an elite group within the cybersecurity company, warns of a recent scam about fake overdue IRS bills.
Now that tax season has ended, criminals are trying to trick people into thinking they owe the government money.
The scam comes as an email with no links and a From address that could seem real at a quick glance. The message may have “urgent” in the Subject Line, and it is noteworthy that the emails come through without being flagged. The examined messages had been sent through multiple ‘hops’ using legitimate-seeming hosts and domains.
The email is simple and typically includes an overdue amount, fake invoice number, and due date with instructions to view and pay using the attachment. The attachment is an html file, and the criminals have embedded “obfuscated JavaScript code that does the following:
- Checks the victim’s location based on IP address to selectively target countries or regions
- Presents a spoofed Microsoft 365 logon screen
- If credentials are presented, checks the credentials’ validity by attempting to logon via IMAP to Microsoft 365
- Transmits the credentials back to a threat actor-controlled server.”
How can you protect yourself?
- If you didn’t already know, the IRS does not use email, texts, or social media to discuss tax debt or refunds. So keep that in mind and share it with your friends and family. In fact, any time you are contacted by a ‘government agency,’ do a quick search online to see if they would ever contact you that way. Forms of official communication are typically at the top of an FAQ list.
- Always be suspicious of ‘urgent’ unsolicited messages that want you to take an action (click a link, open an attachment, etc.). Be even more careful when money is involved.
- Carefully check the From address of any unsolicited message. We get so many emails that we tend to skim rather than read carefully, and that’s exactly what criminals count on. Senders can look okay at a glance, but closer inspection shows the domain is wrong or there are misspellings or character substitutions.
- You can always send messages to your IT team to check for you. We appreciate your care in protecting the network, and we can safely check links and attachments.
 Fake Chatbots
Fake Chatbots
As I mentioned above with the video, the criminals keep evolving. Like any business trying to make money, they will continue to adapt their tactics to what is successful. And that means we need to keep our guard up.
Researchers at Trustwave, a leading cybersecurity and managed security services provider, warn of a new scam that mixes simple and sophisticated tactics. The simple part is an email that directs you to a non-malicious website. The advanced part is the interactive chatbot on that website that walks victims through a step-by-step scam to steal their credentials and payment information.
Trustwave describes why this is effective:
“In general, using chatbots adds an interactive component to a website. This often results in a higher conversion rate because it makes the site more interesting and engaging for the users. This is what the perpetrators of this [scam] are trying to capitalize on. Aside from spoofing the target brand on the email and website, the chatbot-like component slowly lures the victim to the actual [scam] pages. Also, the addition of fake OTP and CAPTCHA pages makes the [malicious] website seem more legitimate.”
Here’s how it works.
You receive an email about a shipping update or delivery problem. It appears to be from a well-known brand such as DHL. The email is a simple, professional-seeming message claiming your package cannot be delivered. There is a button for you to click to rectify the matter.
If you click on the button, you are directed to an online pdf with spoofed branding that shows you more information about the package and has a button to “Fix delivery” plus a link below it. If you click either of these, you will land on the website with the chatbot.
The chatbot greets you and tricks you into trusting it by having you confirm the fake information it provides, such as the tracking number they gave you. It follows a script and asks you simple questions such as choosing between ‘home’ or ‘business’ for the new address. There is even a CAPTCHA they use to appear authentic, but it is only a picture of one.
Ultimately, you are directed to the credential harvesting site where the criminals steal the login and payment information they guide you to enter.
So how can you stay safe from this?
- The good news about this scam is that it starts with an unsolicited email about a delivery problem. We have seen enough of those that you shouldn’t fall for it. If you check the sender carefully, you’ll notice red flags that cause you to delete it or ask your IT team to check it first.
- The second red flag is that the link in the email directs you to a page that wants to send you somewhere else. That should always make you suspicious. It is a common tactic now for criminals to hide their links from email security filters.
- If you were to click on both the email and the link in the fake pdf, you would still want to closely check the URL of the new website. Here you should be able to tell that it is a spoofed delivery service site. You could even bypass all of this by independently navigating to the shipping website and looking up the tracking number they provided.
- Noticing that the chatbot is fake will take more practice. We expect simple, canned responses in automation, so that might not cause concern. The point where they ask for your credentials or any payment is where you need to train yourself to stop. Remember to not ever enter your logins on pages you did not independently navigate to. And anytime someone asks for financial information, ask yourself why. In this example, if a package was supposed to be delivered, then shipping should have already been paid for.
Top 3 Scams – May 1, 2022
Infographic: Q1 2022 Report
KnowBe4’s latest quarterly report on the top-clicked scam email subjects is here. They analyze the top categories, general subjects (in both the United States and globally), and ‘in the wild’ attacks.
Takeaways include:
- Business scam emails remain the highest-clicked category around the world. This category contains typical communication that employees might receive. The subjects of these emails include fake invoices, purchase orders, requests for information, shared files, and more.
- Holiday-themed emails were the most tempting for employees to click on. HR-related messages such as a change in the schedule for the holidays likely piqued interest from employees to see if they would receive an extra day off or shortened work schedule due to the holidays.
- IT and online service notifications that could potentially affect users’ daily work…are effective because they cause a person to react before thinking logically about the legitimacy of the email.
Click the image to view the entire infographic with stats and analysis, and continue to encourage your employees to recognize red flags and remain vigilant.
 Phony Bank Fraud
Phony Bank Fraud
The criminals keep evolving. As we get used to apps and accounts alerting us to unusual activity, scammers try to take advantage. The FBI recently put out a Public Service Announcement warning about texts claiming bank fraud alerts that are fake.
This is how it works:
You receive a text, seemingly from your bank, alerting you that someone has attempted to initiate a money transfer on your account. It will look official, include an amount of the supposed instant payment, and ask you to respond Yes or No if it was you.
If you respond to the text, you get a call from that financial institution’s spoofed number.
The caller claims to be a representative of your bank’s fraud department. To trick you into believing they are legitimate, they may provide personal information such as your old addresses for you to confirm. Then they walk you through the steps necessary to ‘reverse’ the transaction mentioned in the initial text.
But instead of reversing anything, you’ve just sent money to the criminal’s account.
The FBI recommends the following precautions:
- Be wary of unsolicited requests to verify account information. If a call or text is received regarding possible fraud or unauthorized transfers, do not respond directly.
- If this happens to you, contact the institution’s fraud department through verified contact information on official websites or documentation, not through those provided in texts or emails.
- Enable Multi Factor Authentication (MFA) for all financial accounts, and do not provide MFA codes or passwords to anyone over the phone.
- Understand financial institutions will not ask customers to transfer funds between accounts in order to help prevent fraud.
- Be skeptical of callers that provide personally identifiable information, such as social security numbers and past addresses, as proof of their legitimacy. The proliferation of large-scale data breaches over the last decade has supplied criminals with enormous amounts of personal data, which may be used repeatedly in a variety of scams and frauds.
 Prompt Bombing or ‘Being Annoying’ as a Social Engineering Tactic
Prompt Bombing or ‘Being Annoying’ as a Social Engineering Tactic
As Multi Factor Authentication (MFA) increases in use as one of the most effective ways to help people secure their accounts, criminals are trying to find ways around it. Ars Technica, a website for technologists, reports on MFA prompt bombing as a tactic that essentially tries to annoy you into allowing access.
Methods include:
- Sending a bunch of MFA requests (texts or app notifications) and hoping the target finally accepts one to make the noise stop.
- Sending one or two prompts per day. This method often attracts less attention, but “there is still a good chance the target will accept the MFA request.”
- Calling the target, pretending to be part of the company, and telling the target they need to send an MFA request as part of a company process.
An actual member of the criminal hacking group Lapsus$ that has used this tactic gives an example of why it works for them, “No limit is placed on the amount of calls that can be made. Call the employee 100 times at 1 am while he is trying to sleep, and he will more than likely accept it. Once the employee accepts the initial call, you can access the MFA enrollment portal and enroll another device.”
How can you protect yourself?
- First, keep in mind that having any form of MFA in place is always more secure than not having it.
- If you ever get an MFA prompt that was not a result of you trying to log in yourself, call your IT team. Do not accept or allow the prompt, and change your password if you are able.
- Be cautious of unsolicited phone calls that ask you for access. If the caller tells you it’s part of the company process, tell them you need to confirm it. Then independently contact someone you know and trust at your company. Any legitimate professional will appreciate your caution.
- Remember to practice vigilance with your phone texts and notifications just as you do with your emails. For every security measure companies put in place, there will be criminals trying to undermine or smash through it.
 Charity Scams
Charity Scams
Experts warned us, and now we have multiple examples of scammers impersonating various charities and fundraising efforts for the people of Ukraine.
As I’ve mentioned before, most recently in March, global issues and events will always attract criminals because it turns the whole world into their potential targets.
These latest examples include:
- Texts that appear to be from legitimate charity Mercury One. Some of the texts even copy actual texts from the charity. But the links do not go to the Mercury One website. They go to spoofed sites that want your personal information and/or payments.
- Emails seeming to be from the legitimate United Help Ukraine charity that link to a convincingly spoofed site. As Bitdefender researchers describe, “The threat actors behind this campaign go way past any previous nickel-and-dime antics, impersonating the United Help Ukraine organization. Criminals are using IP addresses in the US to deliver this scam across Europe and North America. The DONATE NOW button sends recipients to a cloned version of the official United Help Ukraine Website. The fake website offers users a single donation method, and it closely resembles the official Donate page of the non-profit charitable organization.”
- A series of “help Ukraine” donation posts on webpages, in forums, and sent via email that are really a scam enticing users to send donations to counterfeit addresses. Bleeping Computer describes “attackers using a variety of means—from emails that appear to originate from npr.org or the United Nations Office for the Coordination of Humanitarian (OCHA) domains, to posting forum posts claiming to be behind the “Help Ukraine” movement.”
These tactics are disgusting, but you need to know they’re out there so you can avoid them.
So how can you stay safe from this?
- Always be suspicious of unsolicited texts or emails asking for money. Especially the heart-string-pulling emotional pleas that seem so desperate for help NOW and ‘aren’t even really asking for that much.’ If it’s not a charity you have previously donated to and signed up to be contacted by, then do not click any links. You can look them up independently and donate through legitimate channels.
- Pay particular attention when an email or text elicits an emotional reaction, and make yourself stop and think. Scammers jump into action whenever there is a crisis so they can exploit people’s generosity by clouding their judgment.
- Train yourself to carefully check the sender and link details on any unsolicited messages. Look for misspellings and numbers used in place of letters to appear to be legitimate URLs. And trust your gut if you feel like something is ‘off.’ Sometimes a logo has the wrong colors or is an outdated version. Sometimes the tone of the message is strange. Your brain can notice little things like this before you consciously recognize what felt wrong.
Top 3 Scams – April 1, 2022
Special Alert: Guidance on Global Threats
 On March 21, 2022, both the White House and the Department of Homeland Security issued statements and guidance about the urgency of all US businesses acting now to protect against cyber attacks.
On March 21, 2022, both the White House and the Department of Homeland Security issued statements and guidance about the urgency of all US businesses acting now to protect against cyber attacks.
They both referred to the Shields-Up campaign as a resource for the private sector and stressed the critical importance of shoring up protections.
As our partner, you will always be covered with the best security we can provide. This fact sheet should merely reinforce what we recommend/handle for you.
Click the image to view the White House fact sheet for businesses.
Excerpt from the White House:
“The Biden-Harris Administration has warned repeatedly about the potential for Russia to engage in malicious cyber activity against the United States in response to the unprecedented economic sanctions we have imposed. There is now evolving intelligence that Russia may be exploring options for potential cyber attacks.
The U.S. Government will continue our efforts to provide resources and tools to the private sector, including via CISA’s Shields-Up campaign and we will do everything in our power to defend the Nation and respond to cyberattacks. But the reality is that much of the Nation’s critical infrastructure is owned and operated by the private sector and the private sector must act to protect the critical services on which all Americans rely.
We urge companies to execute the following steps with urgency.”
Excerpt from Secretary of the Department of Homeland Security, Alejandro N. Mayorkas:
“As the Russian Government explores options for potential cyberattacks against the United States, the Department of Homeland Security continues to work closely with our partners across every level of government, in the private sector, and with local communities to protect our country’s networks and critical infrastructure from malicious cyber activity. Organizations of every size and across every sector should continue enhancing their cybersecurity defenses. Organizations can visit CISA.gov/Shields-Up for best practices on how to protect their networks, and they should report anomalous cyber activity and/or cyber incidents to report@cisa.gov or (888) 282-0870, or to an FBI field office. DHS will continue to share timely and actionable information and intelligence to ensure our partners and the public have the tools they need to keep our communities safe and secure, and increase nationwide cybersecurity preparedness.”
 Fake Law Enforcement or Government Officials
Fake Law Enforcement or Government Officials
The FBI issued an alert this March warning of scammers impersonating law enforcement or government officials. This is similar to the SEC scam I sent in December, but like many scams that prove to be effective, it is evolving and expanding.
“Scammers will often spoof authentic phone numbers and names and use fake credentials of well-known government and law enforcement agencies. Scammers will use an urgent and aggressive tone, refusing to speak to or leave a message with anyone other than their targeted victim; and will urge victims not to tell anyone else, including family, friends, or financial institutions, about what is occurring.”
Some of the angles these scams take include the following:
- Your identity was allegedly used in a crime, such as a drug deal or money laundering. You are asked to verify your identity, including social security number and date of birth. You are threatened with arrest, prosecution, or imprisonment if you do not pay to remove charges or assist in the investigation against the “real” criminals.
- You are accused of not reporting for jury duty and being fined, or you missed a court date and there is a warrant for your arrest unless a payment is made.
- Text messages from spoofed Government agencies requesting information regarding passport or driver’s license renewals.
- A notification that your personal information has been compromised and to contact the agency immediately.
- Medical practitioners are contacted to warn of the expiration of their medical licensing, or that their license was utilized to conduct a crime. The scammers will threaten revocation of the license or registration, and the medical professional is compelled to renew their license to protect their professional reputation.
- A romance scam victim begins to realize they are being defrauded and stops communicating with the scammer. Often, the victim is contacted by a law enforcement impersonator attempting to extort the victim to clear their name for participating in a crime or to aid in the capture of the romance scammer.
- A lottery scam victim is contacted by law enforcement to collect taxes and fees. Sometimes the impersonator will state a victim is caught in a scam, and the victim needs to pay to get their money back.
- A victim is contacted regarding a government grant, but must pay taxes and fees to claim their funds.
The goal of all of these approaches is payment.
So what should you do?
Always be suspicious of unsolicited emails, texts, or calls demanding payment.
No matter how official or threatening the person sounds, remember that law enforcement authorities or government officials will never contact members of the public or medical practitioners by telephone to demand payment or to request personal or sensitive information. Any legitimate investigation or legal action will be done in person or by official letter.
Always ask for credentials to validate identity.
Never give personally identifying information to anyone without verifying the person is who they say they are.
The FBI recommends the following steps if you become a victim of this type of scam:
- Cease all contact with the scammers immediately.
- Notify your financial institutions.
- Contact your local law enforcement and file a police report.
- File a complaint with the FBI IC3 at www.ic3.gov.
- Be sure to keep any financial transaction information, including banking records and all telephone, text, or email communications.
 Customer and Tech Support Fraud
Customer and Tech Support Fraud
In another bulletin from the FBI this March, we are warned about more impersonators – criminals posing as tech support and customer support.
This is a threat to all businesses and an even bigger risk to those with remote workers using personal devices at home.
If you’ve been a subscriber for a while, you may remember the February 2020 scam of criminals claiming to be from Microsoft offering to ‘help’ update your Windows 7 machine or give you support past its end-of-life. For a fee, of course. Or remote access into your machine. These scams are similar, but they have expanded.
These recent fraud attempts see criminals impersonating well-known tech, financial, or utility companies, offering to fix non-existent technology issues and renewing fraudulent software or security subscriptions.
They may offer support to resolve such issues as a compromised email or bank account, a virus on a computer, or a software license renewal.
Recent examples:
- Banking support impersonators: You are usually contacted via text or call to indicate a problem with your account. You are persuaded to allow access to your computer and bank account to correct the issue. The scammer uses that access to initiate transfers from the account and others associated with it. By the time you realize what happened, your account is often empty.
- Drivers employed by ride-share or transportation mobility companies: Drivers report being contacted by someone impersonating support staff of their rideshare company with an issue regarding a rider complaint or the driver’s account. The driver is convinced to allow access to their account and all funds in the account are taken by the impersonator.
- Utility, cable, or internet companies: You are contacted by someone impersonating a utility company with claims of an unpaid bill you must pay immediately to avoid shutoff, or you are contacted by a cable, phone, or internet company with offers of great savings.
- Travel industry: Scammers are impersonating customer support of the car rental, airline, and hotel industries with offers of great deals or taking fake reservations. Payment is usually requested by prepaid cards. Unsuspecting victims report to a reservation counter, only to find no car, hotel, or flight reservation exists.
How can you protect yourself?
- Always be suspicious of unsolicited calls, texts, or emails with amazing, incredible offers or urgent demands to pay. Criminals want to elicit strong emotions, such as fear or missing out on a deal, and push you into immediate action so you don’t have time to stop and think.
- Remind yourself that legitimate customer, security, or tech support companies will not initiate unsolicited contact with individuals. Microsoft is not going to call you. It’s more plausible that your bank might, but they often prefer to send official business through the mail. And if it is a real call from your bank, you can get off the phone and call back using the numbers on their website to conduct any business you need to.
- Ensure all computer anti-virus, security, and malware protection is up to date and consider installing ad-blocking software to reduce pop-ups and malvertising (online advertising to spread malware).
- Be cautious of customer support numbers in caller ID as they can be spoofed. And if you search independently for a valid customer service number, make sure you do not accidentally choose an Ad. Phone numbers listed in a “sponsored” results section are likely boosted as a result of Search Engine Advertising and could be a fake listing paid for by criminals.
- Never give unknown, unverified people remote access to your devices or accounts.
 Rethinking ReCAPTCHA Forms
Rethinking ReCAPTCHA Forms
 Researchers at Avanan, an email security company, have found new ways that hackers are using CAPTCHA forms to bypass filters and lull us as end-users into a false sense of security.
Researchers at Avanan, an email security company, have found new ways that hackers are using CAPTCHA forms to bypass filters and lull us as end-users into a false sense of security.
They report emails, often appearing to be faxes with an attached pdf, sent from a legitimate but compromised domain, being used to try to steal credentials.
How it works is that you receive this email with the attached ‘fax.’ You open the attachment, which takes you to a website. There you see a reCAPTCHA form asking you to click to prove you are not a robot.
Once you click, you are asked to enter your credentials in order to view the document. If you do, you have just given them to the criminals.
The researchers explain why this is effective:
“In this attack, hackers are using CAPTCHA forms to bypass scanners.
Perhaps the most popular CAPTCHA is Google’s reCAPTCHA. Google is inherently trusted by most security scanners, since you can’t just block Google. The reCAPTCHA service makes connections to IP addresses that belong to Google and are already in most allow lists.
One of the main tasks of reCAPTCHA challenges–those annoying image games you have to play before proceeding to a site– is to make content inaccessible to crawlers and scanners that do not pass the verification process; therefore, the malicious nature of the target websites will not be apparent until the CAPTCHA challenge is solved.
Further, because the content of this attachment is a seemingly harmless reCAPTCHA, and the mail client will not be able to solve the CAPTCHA, the email client will have no way of determining the safety of the actual attachment’s content. Adding to the challenge for scanners is that the email is being sent from a legitimate domain, in this case, a compromised university site.
To the end-user, this doesn’t seem like [a scam] but more like a nuisance. Given how often the average user fills out a CAPTCHA challenge, it’s not out of the ordinary. Neither are password-protected PDF documents. Plus, the PDF is hosted on a convincingly-spoofed OneDrive page, adding another veneer of legitimacy.
By providing end-users with innocent enough content, and scanners with enough to be fooled, this is an effective attack for hackers to pull off.”
So how can you stay safe from this?
- Always be careful with unsolicited attachments. In a case like this, consider whether or not it is the normal way you receive faxes. Is the sender correct? Does the sender typically send faxes? Confirm it is legitimate with the sender via chat or phone call if this is not a regular occurrence. If you’re in any way unsure, send it to us to check it out for you. We’re happy to do so.
- Be suspicious of attachments, pdf or any file type, that send you to websites. Using a web browser to view an attachment is different than opening an attachment that then directs you to a website. It should send up red flags.
- Carefully check URLs before filling out CAPTCHA forms. Look for misspellings and numbers used in place of letters to appear to be legitimate sites.
- Question whether a pdf you received should be password protected. It can certainly be valid depending on the contents, but you should confirm with the sender in some other method than email before proceeding.
Top 3 Scams – March 1, 2022
 Russia-Ukraine Alert
Russia-Ukraine Alert
This is not a specific scam, but it may be critical to your cybersecurity. And before diving in, I’d like to take a moment and say that our thoughts and prayers go out to the people of the Ukraine currently under siege.
Now that a full-scale invasion is under way, we as business owners need to be ever more vigilant against cyberattacks out of Russia. There have been a series of cyberattacks against several of Ukraine’s bank and government agencies since the tensions began. There is every reason to assume that as these attacks are successful in Ukraine, they will also be directed towards the US and other NATO allies.
The Department of Homeland Security last week launched a “shields up” drive to protect the U.S.’s critical infrastructure from Russian actions. The shields up initiative encourages organizations of all sizes to take steps to reduce their chances of a cyberattack and ensure that they’re prepared in the case of a breach. The recommendations include assessing unusual behavior, assembling a crisis-response team, and shoring up vulnerabilities that might exist in your network.
While most of the press deals with defense and banking systems, cyber attackers are not discriminatory; they will be happy to destroy or disrupt your company as well.
“The reason why there are these bulletins coming out, especially directed at small and medium-sized businesses, is that we have learned the hard way about the fragility of the global supply chain,” says Theresa Payton, a former White House Chief Information Officer under George W. Bush.
So what should you do?
- We recommend the following actions be performed by or with your IT services provider. These are not new or one-off activities, but now is a good time to ensure they’re being handled to your satisfaction.
- Make sure your backups work, and test the restore function.
- Patch all known vulnerabilities and test the patches.
- Deploy strong MFA to as many employees as you can (some MFA can be easily circumvented).
- Remind employees of the role they play in keeping your business secure. For example, employees should actively look out for indicators of a potential business email compromise attack:
> Be skeptical—Last-minute changes in wiring instructions or recipient account information must be verified by some other method than email.
> Double check that URL—Ensure the URL in the email is associated with the business it claims to be from.
> Spelling counts—Be alert to misspelled hyperlinks in the actual domain name.
Consider stepping all employees through at least a 15-minute security awareness training module to keep security top of mind. This email is designed to help, but not everyone reads their messages and others have unsubscribed.
Now might also be a good time to review your Incident Response Plan. Dust it off if it hasn’t been looked at in a while, or put it on paper if it only lives in your head right now.
And be on the alert for scammers pretending to be Ukrainians on social media looking for financial help. Experts at Avast have seen it already.
Remember that with every major disaster, criminals will try to prey on your emotions. Be suspicious of unsolicited emails and social media posts requesting payment in digital currency. A quick search came up with this list from the Washington Post of legitimate nonprofits and organizations.
 Right-to-Left Trick Targeting Microsoft Users
Right-to-Left Trick Targeting Microsoft Users
Everything old becomes new again.
Right-to-Left Override (RLO) is a 20-year-old technique that can make file extensions appear to be different than the file types they really are. For example, a file named “abctxt.exe” would use RLO like this “abc[U+202e]txt.exe” and appear as “abcexe.txt” in Windows. So it looks like an innocent text file now, even though it is actually an executable file.
Vade, a global leader in threat detection and response, has detected a recent wave of attacks using this old, often overlooked tactic scoping Microsoft 365 accounts. They’re seeing it typically come through as ‘voicemail’ attachments.
You get an email saying you have a voicemail from a specific person or a ‘private caller’ with a datestamp included, and there is an mp3 or wav file attached. When you click to open the voicemail, you are taken to a Microsoft login webpage that requests your credentials to access the ‘sensitive information.’ In some instances, entering your login takes you to a fake voicemail message, and in others, you see an error message. In all cases, your Microsoft credentials have just been submitted to the scammers.
How can you protect yourself?
- Start by familiarizing yourself with the way your company officially sends voicemail notifications. If you get a message that’s different, it should raise a red flag. For example, ours come from the same noreply email address each time, and the attachments are wav files. So if we were to suddenly see mp3 files or a different sender, everyone should be on alert.
- Train yourself to slow down before taking any action on attachments. Whenever a message comes through with a file attached, carefully check the sender, the message itself, and the name of the file. If you have any questions or doubts, forward it to your IT services provider to check out for you. We’re happy to do that for our clients; it helps protect us all.
- Always stop before entering your credentials on a page someone else sent you to. Especially in this case when you thought you were opening an audio file, being directed to a website should make you suspicious. If you did not independently navigate to a page you expected to have to log into, then do not enter your credentials.
 Using QR Codes for Crime
Using QR Codes for Crime
In another what’s-old-is-new-again tool, QR codes are on the rise as a scam tactic.
QR codes are the black-and-white square barcodes that you can scan with your phone’s camera and have a webpage link or other information appear. You’ve probably used them for restaurant menus and event or airline tickets. And you may have seen the Coinbase commercial during the Super Bowl that was so popular it briefly crashed their app.
They’ve been around since the ’90s and were used for automotive inventory initially, but they didn’t really catch on publicly until the late 2000s. And since the pandemic, they’ve surged. So much so that the FBI recently issued a warning about QR codes.
“Cybercriminals are taking advantage of this technology by directing QR code scans to malicious sites to steal victim data, embedding malware to gain access to the victim’s device, and redirecting payment for cybercriminal use.”
The FBI and other security experts give the following examples of QR code criminal tampering:
- For parking spaces to steal payment information
- Redirecting an app download to the criminal’s malicious app or download
- Scanning to send a tweet or SMS (text) message for a contest can have the number changed to spam a person with those messages
- Automatically connecting to a business’s Wi-Fi can send you to the criminal’s malicious network instead.
So how can you stay safe from this? The FBI offers the following tips.
- Once you scan a QR code, check the URL to make sure it is the intended site and looks authentic. A malicious domain name may be similar to the intended URL but with typos or a misplaced letter.
- Practice caution when entering login, personal, or financial information from a site navigated to from a QR code.
- If scanning a physical QR code, ensure the code has not been tampered with, such as with a sticker placed on top of the original code.
- Do not download an app from a QR code. Use your phone’s app store for a safer download.
- If you receive an email stating a payment failed from a company you recently made a purchase with and the company states you can only complete the payment through a QR code, call the company to verify. Locate the company’s phone number through a trusted site rather than a number provided in the email.
- Do not download a QR code scanner app. This increases your risk of downloading malware onto your device. Most phones have a built-in scanner through the camera app.
- If you receive a QR code that you believe to be from someone you know, reach out to them through a known number or address to verify that the code is from them.
- Avoid making payments through a site navigated to from a QR code. Instead, manually enter a known and trusted URL to complete the payment.
Top 3 Scams – February 1, 2022
Special February Warning:
The Rising Insider Threat – Ransomware Recruiting
KnowBe4 shares the Hitachi ID report that says hackers have approached 65% of executives or their employees to assist in ransomware attacks.
“Since our last survey conducted in November, there has been a 17% increase in the number of employees and executives who have been approached by hackers to assist in ransomware attacks,” the researchers write.
Perhaps you heard about the Tesla employee offered 1 million in 2020 to trigger a DDoS attack.
Kumar Saurabh, CEO and co-founder of LogicHub, explains, “The top ransomware groups are run like well-organized businesses, and paying ‘finder’s fees’ to insiders for access is well worth the investment.”
Click the image to view the infographic from Hitachi ID.
And revisit our article about National Insider Threat Awareness Month (September) here.
 Supply Chain Scams
Supply Chain Scams
Supply chain issues are impacting businesses worldwide. Threat actors like to take advantage of global trends and are using fake ‘shipping delays’ to deceive customers and businesses.
Troy Gill, senior manager of threat intelligence at Zix, a security technology company, explains:
“Over the last couple of months, the Zix Threat Research team has observed threat actors using new tactics to spoof logistics and supply-chain companies, hoping for an easy compromise. With shipping delays and supply shortages expected to continue well into 2022, it’s a good bet that these lures will continue to land in corporate inboxes.”
In fact, International shipping company DHL was the most impersonated brand during the fourth quarter of 2021 (pushed Microsoft out of the top spot) according to researchers at Check Point.
A recent scam works like this.
You receive an email that appears to be from a major shipping company.
The email is designed to get you to click the link, often to download a ‘shipping confirmation’ document. Other variations may imply that you will lose access to a valuable account if you do not respond quickly.
Clicking on that link takes you to a convincing yet fake website that asks for your credentials as if to confirm your email login. If you enter them, you’ve just given them to the criminals.
How can you protect yourself?
- Consider the message–any message–before taking any action. Should you have received a shipping confirmation? Were you expecting anything to be delivered? Do you normally handle that at work? If not, then send the message to your IT team to check before simply forwarding it to a coworker who may think it’s safe because it’s coming from you.
- Always stop before entering your credentials on a page someone else sent you to. If you did not actively navigate to a page you expected to have to log into, then do not enter your credentials.
 ‘Consent’ Attacks
‘Consent’ Attacks
Be careful of the apps you download.
Scammers have caught on to people not wanting to enter credentials online and are trying a new route. They are creating apps that request access to your email as part of their setup.
Microsoft Security Intelligence identified (and disabled) apps that were asking for OAuth permissions. Granting permission, or consenting to this, allowed the app to create Inbox rules, access contacts and calendars, and pull emails out of your Inbox.
That is unusual behavior for another app to perform, and Microsoft’s app governance feature in Microsoft Defender for Cloud Apps flagged it. But experts warn that new apps will keep trying this, so be on your guard.
What makes this tricky is that we often blindly agree to everything once we’re in installation or setup mode. Terms and Conditions? Agree. Send notifications? Sure. Access email and contacts? Why not.
So how can you stay safe from this?
- The simplest way is to only download apps from reputable sources like the App Store or Google Play. Bad apps can still get in, but they are often quickly reported and removed, and this will always be safer than downloading from a random link somewhere on the internet.
- Train yourself to always ask Why.
If you download an app in order to play a game, why would it need access to your email or your calendar? Many chat or meeting apps want access to your contacts. That seems reasonable. So pay attention to what level of access is being requested. Do they want to just read or be able to add, update, and remove things?
Legitimate apps often explain why – that they want to access your contacts in order to invite them or allow you to communicate with them through the app, for example. If you know it’s a trusted app, like Microsoft Teams, then feel free to give your consent. But if anything seems odd or off to you, don’t blindly agree.
You can almost always add more permissions. It can be very difficult or impossible to remove them after consenting.
 No Comment
No Comment
Last July I shared ways that scammers use Google docs to hide malicious webpages and send messages that make it past security scans (because they are legitimately from Google). Now we have a new approach using this same foundation.
Avanan, an enterprise AI cloud security company, has “observed a new, massive wave of hackers leveraging the comment feature in Google Docs, targeting primarily Outlook users [though not exclusively].
In this attack, hackers are adding a comment to a Google Doc. The comment mentions the target with an @. By doing so, an email is automatically sent to that person’s inbox. In that email, which comes from Google, the full comment, including the bad links and text, is included. Further, the email address isn’t shown, just the attackers’ name, making this ripe for impersonators.”
This scam is hard to spot for multiple reasons.
1. The comment notification email is likely to come through to you despite security filters because it is truly from Google.
2. The email does not show you the email of the sender. A scammer can create any free Gmail account they want, such as john.doe@gmail.com, but the only name that will show in the comment email is the name they created (John Doe), not the full email. So if you know someone named John, you could think this was legitimate.
3. The link in the email contains the payload. You do not have to enter credentials. You won’t see an attachment that makes you think twice. You’ll simply be notified that you were mentioned in a comment on a document by ‘John’ with a link to that document.
How can you avoid this trap?
- Be alert for unsolicited Google docs. If you don’t normally work in them or share them with friends, then stop yourself before you click. If you think you recognize the sender’s name, think about whether the included note sounds like them. If you know someone with that name but you don’t know why they’d be tagging you in a comment on something, reach out to them separately from this message. Call, chat, or send them a text to see if it’s legitimate.
- Remind yourself to stop whenever you can’t verify a sender’s email address.
- And if you have any doubts, ask your IT team to check the message for you.
Top 3 Scams – January 1, 2022
A Couple of Stats to Set the Stage:
 1. A December report from the FTC (click image to view) shows that people lost more than 148 million in gift card scams in just the first 9 months of 2021.
1. A December report from the FTC (click image to view) shows that people lost more than 148 million in gift card scams in just the first 9 months of 2021.
- Tip: Always be suspicious when payment is requested via gift cards. As the FTC report says, “Scammers can get quick cash, the transaction is largely irreversible, and they can remain anonymous.”
 2. Truecaller’s 2021 Global Spam Report shows spam calls on the rise and becoming more sophisticated.
2. Truecaller’s 2021 Global Spam Report shows spam calls on the rise and becoming more sophisticated.
“Americans receive approximately 1.4 billion spam calls per month, based on the number of smartphone users and average number of spam calls Truecaller users receive daily.”
- Tip: Never give out personal information to an unsolicited caller. Get whatever details you can and get off the phone. Find some way to verify the information and then call back if it’s legitimate
 Fake Spam Notifications
Fake Spam Notifications
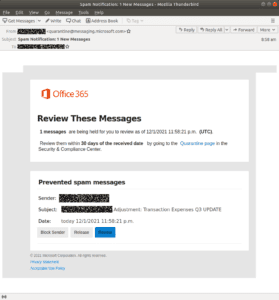 This new scam on the rise targets Microsoft users.
This new scam on the rise targets Microsoft users.
You receive an authentic-looking email from ‘quarantine’ with Microsoft in the domain.
The message tells you that you have 1 or multiple messages that have been blocked and need to be reviewed.
The message has a convincing look and format, including the Office 365 logo.
If you click the blue Review button, you will be taken to a page that requires you to log in. A tricky detail on this page is how they show ‘Session Expired’ in the login box which could trick you into thinking it is legitimate.
If you do type in your credentials, however, you have just given them to the criminals.
How can you protect yourself?
- Always stop before entering your credentials on a page someone else sent you to.
Even if you think this is a legitimate Microsoft login page and you see a padlock in the URL.
Even if the message that contained the link looks completely convincing.
If you did not actively navigate to a page you expected to have to log into, then do not enter your credentials.
- Backing up to the message itself, knowing how your company communicates quarantined messages will help you identify this as fake.
Do you get them directly from Microsoft, from a spam filtering service, or from your IT team? Do they look like this message and include all the security measures your company told you to expect? If not, or if you are in any way uncertain, send the message to us to check out.
 TSA PreCheck Scam
TSA PreCheck Scam
 Planning any travel in 2022? Many businesses are, and even more personal trips are expected. This scam targets anyone considering signing up for or renewing their TSA PreCheck.
Planning any travel in 2022? Many businesses are, and even more personal trips are expected. This scam targets anyone considering signing up for or renewing their TSA PreCheck.
It begins as an email that includes some version of ‘Visa’ or ‘Immigration’ in the sender.
You may notice a red flag that the sender is not a ‘tsa.gov’ email address, but not everyone would notice that or consider it strange. Many TSA PreCheck Enrollment Centers are not government entities.
What makes this scam scary is how it does “one of the best jobs impersonating a website ever seen,” according to KnowBe4. Rather than to a quickly thrown together landing page, clicking the link in the email takes you to a nearly full-fledged website with an entirely believable application process.
In addition, unlike most scams, it doesn’t ask for payment up front.
You go through the steps to fill out your personal information and select a security interview time from the windows available. Then, when you certify that everything has been entered correctly, you are asked to pay, along with believable disclaimers of processing time.
Researchers at Abnormal Security say that “This is not the first time this scam has appeared, and it’s not likely to be the last… While this scam mostly targets consumers, organizations that pay for or reimburse employees for TSA PreCheck and related services should be wary of these emails reaching employee inboxes. As business travel resumes around the world, organizations should provide this information to employees as an added precaution.”
So how can you stay safe from this?
- As tempting as it is to click on links in unsolicited emails, train yourself not to. This entire scam can be avoided if you see the message about TSA PreCheck but navigate to the website on your own.
It seems easier to click a link that’s right in front of you, but the risks make it far more work and less worth it.
- Also remember to check for secure URLs (https) with the exact right spelling.
- And if you have any hesitation about a sender, a message, or a link or webpage, trust your instincts. You can always ask your IT team to check something out for you.
 Another Pandemic Warning
Another Pandemic Warning
 The global trend that just keeps giving to criminals still isn’t stopping. With the new omicron variant, scams about testing and getting information about restrictions have been reported.
The global trend that just keeps giving to criminals still isn’t stopping. With the new omicron variant, scams about testing and getting information about restrictions have been reported.
As researchers at BleepingComputer put it, “Threat actors are quick to adjust to the latest trends and hot topics, and increasing people’s fears is an excellent way to cause people to rush to open an email without first thinking it through.”
Current examples (my Marketing person says we should call them ‘ex-scam-ples’) show offers of free testing.
If you click the links or buttons in the emails, you are directed to a spoofed health services website. There, they want you to enter your contact information and send a minimal fee, supposedly to cover the cost of shipping the results.
What’s interesting is that the fee isn’t important to these criminals. Getting a couple of dollars off a few hundred or thousand people can add up nicely, but what they are really taking is your financial information. And that can add up to a whole lot more.
What can you do against this?
- Continue to be vigilant about any unsolicited emails related to global or national trends
If you receive something that appears to be from an official health service or government agency, check their website independently. They should have the same information there that you saw in the message.
- Take note of the emotions an email makes you feel, if any. Scammers like to evoke fear and urgency so you are compelled to take action quickly
Always stop and think before entering login credentials or financial information.
- Be suspicious of any free offers. Some can certainly be real, but remember the saying: “If you’re not paying for it, you’re not the customer; you’re the product being sold.”
Top 3 Scams – December 1, 2021
 SEC Scam
SEC Scam
The US Securities and Exchange Commission (SEC) has recently issued a warning of scam calls, voicemails, and emails.
The investor alert describes calls and messages that appear to come from the SEC. The topic is typically an unauthorized transaction or suspicious activity in your checking or other financial account. The scammer may say they need to confirm some information before allowing a trade to go through, or they may threaten you with penalties and fees that you need to pay before more serious action is taken. Their goal is to get you to share account information, PINs, passwords, etc., or to send money.
Some of these calls and emails have been reported to use actual SEC employee names, but the official alert states that the SEC does “not make unsolicited communications – including phone calls, voicemail messages, or emails – asking for payments related to enforcement actions, offering to confirm trades, or seeking detailed personal and financial information.”
How can you protect yourself?
- Be immediately skeptical if you ever receive an out-of-the-blue call or email from a government agency. In this case with the SEC, you can call (800) SEC-0330 or email help@SEC.gov to see if a communication is legitimate before sharing any personal information.
- This type of scam tries to use fear and intimidation to trick you into responding quickly. By spoofing the phone number and email of a real government agency, they appear to be an authority you shouldn’t question. But the point of sharing all these scams is to train you to do exactly that – question. Any real agency will allow you to confirm or verify before blindly taking action. These scams try to make you panic so you act without thinking. So remember, anytime a call or email elicits a strong reaction, especially of fear, stop and take a deep breath. Think through whether it makes sense, and verify independently before following their directions.
 Don’t Take the Bait
Don’t Take the Bait
There’s a new kind of email to look out for–the one that’s just bait.
According to Barracuda, an IT security company, “bait attacks, also known as reconnaissance attacks, are usually emails with very short or even empty content. The goal is to either verify the existence of the victim’s email account by not receiving any ‘undeliverable’ emails or to get the victim involved in a conversation that would potentially lead to malicious money transfers or leaked credentials.”
What’s tricky about bait emails is that there is nothing malicious to trigger your security filters. The messages often come from a Gmail address, and there are no suspicious links or attachments. In fact, many bait emails don’t have any text in them at all.
The goal of a bait email is to see if it gets opened, which lets the scammer know that the email address is valid, or even better, gets you to reply to it, so the scammer knows you are willing to respond. They then use your email address in a targeted attack later.
One example of a bait email simply said ‘Hi’ in the subject line. The recipient replied with ‘Hi, how can I help you?’ And within 48 hours, the recipient was part of a targeted attack.
Bait attacks show how scammers continue to evolve. When they send a bunch of malicious emails that get reported, their servers can be shut down. When they send a bunch of emails that bounce, they can get flagged, which means they are less likely to reach inboxes. When they send mysterious emails that people don’t know are part of their scam, two things happen. 1. They don’t get reported. 2. They have a list of email addresses that they know won’t bounce, which means many email filters won’t automatically reject them.
So how can you stay safe from this?
- The best thing you can do is to not open emails from people you don’t know. I realize that’s not always possible though. So if you do see any kind of message like this, please report it. Even though there is nothing malicious in the message, and even if you feel silly, it could be a bait attack. And if it is, the fact that you got it and opened it means you could receive a targeted attack. If you let us know about it, we may be able to increase security or monitoring for your account. And if you let us know about it before opening it, we can remove it and potentially keep you from being targeted.
- As tiring as it can be to remain alert for all the different email attacks and calls and texts we’re threatened with, paying attention to these scam trends is one of the best ways to stay safe and protect your network. Tactics will continue to change, and it always comes down to how we interact (or not) with these messages.
 Customer Complaint Scam
Customer Complaint Scam
Customer service is a fast-paced, critical part of any business. Questions need to be answered, fears calmed, and problems resolved. But what happens if, no matter what you do, a customer remains unhappy?
Experts at Sophos, a security software and hardware company, warn us of a scam that uses fake customer complaints to convince you to click on real malicious links.
The way it works is you get a message that appears to be from a manager or someone high up at your company. It says something along the lines of ‘we need to talk about…’ or ‘why didn’t you tell me about…’ and links to a supposed pdf of a customer complaint. It may also include an order to ‘call me immediately’ or something similar to make you nervous.
Naturally, you would be curious to know what the complaint is before calling. But clicking on the link takes you to a file download that will install malware on your computer.
As Sophos explains, “The goal of these cybercriminals is to make you feel guilty, and to convince you that through inaction on your part, you have caused serious inconvenience not only to the company as a whole, but also to someone more important than you in the organization.”
What can you do against this?
- Be good thing about this scam is that it has been reported with a couple of red flags we should all be able to recognize by now. For one thing, the messages often have obvious spelling or grammar errors. For another, if you click on the link, you’ll see it wants you to download a file. Someone within your company would much more likely attach a pdf or simply copy-and-paste the text of the complaint to discuss. Always stop yourself before downloading a file from a link you were not expecting.
- Try to recognize and stop yourself the moment you feel fear or panic as a reaction to an email. No one wants to look bad in front of their boss. But take the time to carefully check the to and from email addresses. Consider who the email appears to be from and ask yourself if it makes sense for them to be emailing you about a customer complaint. If you have any doubts at all, pick up the phone or send a chat message rather than clicking on the link. This scam is also trying to use your curiosity as a trigger, so try to be aware of that, too.
Top 3 Scams – November 1, 2021
Special Notice for our South Carolina Neighbors
Be on your guard. Our partners at the Department of Homeland Security shared a report with me on Friday about expected threats to South Carolina state, local, and critical infrastructure networks for the foreseeable future.
The report states that a “vulnerability scan of 14 South Carolina organizations revealed over 35,000 vulnerabilities in 2020, including over 6,000 vulnerabilities listed as ‘critical,’ according to a state report.” And it specifically points out ransomware and opportunistic and widespread targeting through emails and exploiting unpatched vulnerabilities as the 2 main threats.
The report’s conclusions came from studying incidents reported to the state, field rep information, and media coverage from October 2019 through April of this year. You may remember hearing about the Georgetown County network getting infected this past January. Or maybe you were one of the people who had to go in person to pay or pick up your license plate decal.
The bottom line is that “malicious cyber actors targeting South Carolina networks will continue to evolve tactics and develop effective business models to maximize the chance for financial gain.” If your network improvements have been on the back burner for a while, now is the time to make them a priority.
 Microsoft Warns of ‘Password Spray’ Attacks
Microsoft Warns of ‘Password Spray’ Attacks
Last week, Microsoft published a blog by their Detection and Response Team (DART) and threat intelligence teams detailing an uptick over the past 12 months of ‘password spray’ attacks. These are “authentication attacks that employ a large list of usernames and pair them with common passwords in an attempt to ‘guess’ the correct combination for as many users as possible. These are different from brute-force attacks, which involve attackers using a custom dictionary or wordlist and attempting to attack a small number of user accounts.”
The article explains how attackers have changed their approach. “Previously, threat actors focused on attacking computers to gain access into an environment. As software becomes more intelligent at detecting abnormal programs and vulnerabilities, attacks against our customers are rapidly becoming more focused on breaking into identities rather than breaking into a network.”
And one of the 2 methods used in a password spray attack, they call “Availability and Reuse: With a new breach being announced publicly every month, the amount of compromised credentials posted on the dark web is rising rapidly. Attackers can utilize this tactic, also called ‘credential stuffing,’ to easily gain entry because it relies on people reusing passwords and usernames across sites.”
The US Sun puts it a little more simply. “Hackers can plug these combinations into other websites in the hope that you’ve reused them across multiple online accounts.”
What does all this mean?
Google estimates that over 4 billion username and password combinations have leaked in recent years.
And a recent survey by PCMag found that 70% of people over 18 use the same password for more than one account, if not every login.
So if you or any of your employees reuse a password that is included in that estimated 4 billion, then your network is at risk.
How can you protect yourself?
- First, stop reusing passwords for more than 1 account or login, especially any passwords you use for work. Second, see if your email has been exposed at haveibeenpwned.com. Third, change any passwords shown in the results and close any accounts that you don’t actively use anymore.
- Get a password manager. There are quality free and paid tools that can store and even create strong, unique passwords for you. Many of them have apps or plugins for your browser so you can log in seamlessly once you’re set up. It can take time to add in your existing accounts and create stronger passwords, but putting in the effort now will better protect you and everyone in your network.
- Consider disallowing any password policy exceptions you may have made at work over the years. As Microsoft points out, “identities with a high profile (such as C-level executives), or identities with access to sensitive data are also popular targets” [in addition to administrator accounts], and those roles are typically where exceptions are made and therefore where weak spots can be introduced.
 Craigslist Notifications Scam
Craigslist Notifications Scam
Hearing about this one made me feel like I was back in the year 2000. But apparently Craigslist is still alive and well and being actively used. Maybe even by you.
According to INKY, this is what’s happening: “Craigslist, that old-fashioned website people still use to find things locally — and urgently — has become the latest [attack] vector. In the service of safety and anonymity, Craigslist lets people seeking or offering things send an email through the system to anyone else. Craigslist knows the identities of everyone, but unless a correspondent discloses details, they are perfectly anonymous to others on the system. [So criminals] can shoot their poisoned arrows from behind a local mail proxy. And shoot they did — a number of times in early October.”
The scam is a real-looking notification email sent from the Craigslist domain. It claims that your listing has inappropriate content or has violated the terms and conditions, and it includes instructions on how to avoid having your account deleted. The instructions are false, directing you via link or a button to download the form you need to fill out.
But if you click on the link, you go to a OneDrive page with an ‘online version not available’ error message and a download link. If you download the zip file and extract what’s in it, you will install malware on your computer.
So how can you stay safe from this?
- This example, while specific to Craigslist, is an attack type we’ve seen used effectively on other platforms and one we can all learn from. Get familiar with the ways your platforms communicate official information. Researchers believe Craigslist was compromised, which is why the emails came from their domain, but Craigslist users should know that a real message would have had the form attached to it, not linked.
- Always be suspicious when you are directed to OneDrive from another company’s ‘official’ message. It doesn’t make sense for Craigslist to send you to OneDrive when they could host whatever they need to on their own site
- Also be suspicious when extra steps are involved, i.e., when a link does not take you directly where it says it will take you. This message claimed the link went to the form. But clicking the link led to OneDrive where there was a separate link for downloading the form. And that download wasn’t a form, it was a zip file which can contain any number of things. These ‘extra steps’ have become a common tactic for criminals since you can store nearly anything in a zip file or on OneDrive or Google yet use their legitimate links to bypass security filters.
 Potluck of Scams
Potluck of Scams
With Thanksgiving coming up later this month, think of this last item as more of a cornucopia of miscellaneous warnings. Instead of one detailed scam, this is an assortment of recent threats to look out for beyond email attacks. You can think of them as your side to the feast: mashed potatoes, green beans, cranberry sauce, etc.
And I want to say Thank You as well. Cybersecurity is not always something people want to think about. With the frequent headlines of hacks and breaches, we can get overwhelmed by it all. But it is absolutely vital to us, professionally and personally. So thank you for reading these emails, for being vigilant and asking questions. Thank you for your trust in my team and for all you do to help us keep you protected. I appreciate you.
~ ~ ~
Experts are warning Facebook and Clubhouse users to be especially vigilant of malicious texts, social engineering scams, and profile hacking. Supposedly, a user on the dark web has taken the 3.8 billion phone numbers scraped from Clubhouse in July and matched it with Facebook information, creating a sort of “goldmine for scammers,” according to CyberNews senior information security researcher Mantas Sasnauskas. It gives contextual information about the owners of the leaked phone numbers, including usernames, locations based on phone number suffixes, their Clubhouse network sizes, and Facebook profiles.
If it’s genuine, this means that it would be much easier for scammers to run localized mass campaigns and craft personalized scams based on the data gleaned from the potential victims’ Facebook profiles.
“People tend to overshare information on social media. This could give insights for scammers on what vector to employ to run their scams successfully by, for example, calling people with the information they learned from their Facebook account,” says Sasnauskas.
It’s also important to note that you wouldn’t have to have a Clubhouse account in order to be on this list. Clubhouse used to insist subscribers shared their address book, so those contacts could be in the scraped information and this newly compiled database.
What can you do against this?
- Be careful of connection requests and messages on Facebook, especially if they include links. See if your email or your phone number has been exposed at haveibeenpwned.com. Be on the alert for spam texts, and be especially vigilant of social engineering attempts. You may also want to consider dark web monitoring so you will be notified if your information shows up for sale on the dark web.
Android apps that have been downloaded more than 10 million times have been found to be part of a premium SMS scam. The apps cover a wide variety of fake purposes including photo editors, games, custom keyboards, call blockers, and more. But when you download and open them, you are prompted to enter your phone number and sometimes email, which is used to subscribe you to a premium SMS service. Once you submit the info, you may see subscription options or the app may stop working. The sole goal is to sign you up for charges you may not even notice on your cell phone bill. As of the last week in October, 151 apps had been identified and removed from the Google Play Store, but experts believe others are still available.
Avast researchers share how to avoid this:
1. Remain vigilant when downloading new apps, especially apps advertised in short and catchy videos. Children may be particularly vulnerable to this type of scam.
2. Disable the premium SMS option with your carrier. While there are legitimate uses for premium SMS, such as donating to charities, it is an easy avenue for malicious actors to abuse. Disabling this option will nullify the UltimaSMS scam. Based on some of the user accounts that left negative reviews, it looks like children are among the victims, making this step especially important on children’s phones, as they may be more susceptible to this type of scam.
3. Carefully check reviews. Scam apps often have boosted review averages, but written reviews may reveal the true purpose of an app. Checking the developer’s history and profile may also be useful.
4. Don’t enter a phone number unless you trust the app. Being careful with personal details, including phone number and email, goes a long way to avoiding similar scams.
5. Read the fine print before entering details. Legitimate apps will have Terms of Service and a Privacy policy alongside a statement of how they intend to use your data and entered details.
6. Stick to official app stores when downloading apps. Although the known apps have been removed from the Google Play Store, they are still available for download elsewhere on the internet.
This one isn’t a scam, but it’s another threat worth being aware of. A WordPress plugin had a bug, known about for nearly a month, that allowed subscriber-level users to wipe an entire site’s content. Hashthemes Demo Importer is the plugin that has since been patched, but the implications are concerning.
What can you do against this?
- An estimated 455 million websites use WordPress, and plugins are constantly being updated and added. Keep your plugins up-to-date, and back up your website regularly so you can recover from an unexpected situation like this. Also keep an eye on your backend activity so you can see when something irregular happens.
Another set of bugs has recently been addressed by Adobe in 14 of their products. The company says there is no evidence of any of these vulnerabilities being exploited in the wild, but I mention it here to encourage you to update any of their design products you may use. Adobe PDF programs were not included in this group, so you may not need to update anything, but programs like InDesign and Illustrator were included.
- Software patching seems like a never-ending hassle, but it is critical. Bug bounty hunters and white hat hackers look for vulnerabilities so they can be addressed before they become a risk to end users. Our team stays on top of system updates for exactly this reason and will push out Windows and Microsoft patches automatically when they become available, but every business uses a variety of programs. So if you ever receive notices from industry-specific software or programs that only you or a handful of employees use, be sure to share that with your IT team. Let us help keep you up-to-date and protected.
Top 3 Scams – October 1, 2021
October is Cybersecurity Awareness Month.
The National Cyber Security Alliance & the U.S. Department of Homeland Security launched Cybersecurity Awareness Month in October 2004.
It was created as a collaborative effort between government and industry to ensure that every American has the resources they need to stay safer and more secure online. Now in its 18th year, the need for ‘digital hygiene’ and safe online practices is more important than ever.
Infinity is proud to be a Champion of this initiative again, and we’ll be sharing useful tips and practical guides all month long. To get started in your office or at home, please feel free to use and share resources like the following from CISA and the NCSA.
- Own Your Role in Cybersecurity: Start with the Basics (Tipsheet)
- Tech Support Scams and How to Avoid Them (Infographic)
- Security Tips for Remote Workers (Tipsheet)
- Mobile Device Security (Tipsheet)
- Cyber Safety Starts at Home (Infographic)
 Virtual Kidnapping
Virtual Kidnapping
This horrific scam actually happened to someone on our team.
You get a call from someone close to you, typically your mom. You answer and hear a woman’s voice crying before the phone is taken away. You think it’s your mother, so naturally you start to panic, wondering what’s wrong. Then a man threatens to kill her if you don’t send money. He threatens to kill her if you call the police or try to call anyone else. He’ll give you an amount and will demand you pay through an app like Venmo or CashApp.
The whole experience is designed to be fast and overwhelming. These criminals use spoofing tools to make the call look like it’s coming from the actual contact in your phone. They won’t let you speak with the caller (your mom) and will threaten to hurt or kill her if you do anything other than comply.
The amount of money demanded typically ranges from one to five thousand dollars. And in one case, the victim was walked through the steps of installing the preferred payment app on her phone by the scammer in order to complete the transaction.
It’s quick money for the criminal, and they have no shame.
How can you avoid this scam?
- This type of extortion scheme has been around for decades, dating back to cold calls from Mexican prisons. It used to target Spanish speakers living in the southwestern US. Now, residents across the country are at risk. The FBI recommends the following:
— Try to slow down the process. It can help you think more clearly.
— Avoid sharing information about you or your family during the call. The scammer can repeat names or other things you say to sound more convincing.
— Ask to speak to your loved one.
— Ask them a personal question about your loved one, such as birth date or hair or eye color.
— Have someone else try to text or call your loved one if your requests are refused.
— Report the incident to your local police and file an FCC complaint (1-888-CALL-FCC.’ - This scam has evolved over the years. With many of us blocking or ignoring unknown callers on our cell phones now, the effectiveness comes from the call looking like one of your contacts. Scammers need both phone numbers for a successful spoof, but with all the data breaches, that information isn’t hard to come by. And while we may take it seriously when we know social security numbers are involved, we don’t normally take action when we hear phone numbers get leaked. But we should. So check your email and your phone number at haveibeenpwned.com. The first step is knowing your risk or current exposure.
 Google Voice Scam
Google Voice Scam
With all the online selling platforms available (Ebay, Marketplace, Etsy, even parts of Amazon), it’s possible to find almost anything you could want…or at least think you have. The various programs have differing levels of verification and security, and nearly all of them warn you that you accept liability for your transactions. Naturally, with the rise in popularity of these one-to-one online sales comes an increase in scam opportunities.
The Identity Theft Resource Center (ITRC), a nonprofit organization dedicated to supporting the victims of identity theft, building awareness, and helping resolve cases, reports the following:
“If you are looking to sell anything online, you should be aware of the Google Voice scam. Scammers are posing as interested buyers on online marketplaces and are trying to steal your personal information to create a fake Google Voice account in your name.”
One such report had a woman describe the process of being contacted by a buyer. They agreed on their deal and the buyer asked the seller for her phone number in order to coordinate pickup. Then, instead of calling to make arrangements, the buyer said they’d like to confirm by sending a verification code, since they had seen so many fake posts. Sounds reasonable. The seller got the code and was about to send it when she saw the warning that tells her not to share this code with anyone. She pushed back on the buyer who insisted the code was necessary to prove the seller was legit. The seller refused, and the buyer vanished, removing the user profile, too.
Of the 1,824 victim cases the ITRC received in August, 49% of them were Google Voice scams.
The scam is that with the verification code, the criminal can create a fraudulent Google Voice account in your name that is used to scam others.
The ITRC is also receiving reports from victims who claim to not have a Google Voice account. In this scenario, scammers set up a Google Voice account and link it to the phone number of the person they call so they can create a fake post selling the same items as a legitimate seller.
So how can you stay safe from this?
- The need for increased protection of our online accounts is why multifactor authentication (MFA) has become so much more popular, if not downright required. It adds verification steps beyond entering your password in order to gain access to your accounts (watch a 90-second video here). And these extra steps force criminals to get more creative. They need you to pass along those codes or PINs or other verifying information. That means you need to start treating that info as you do your passwords: no sharing. The seller above said she almost fell for the scam. It was only seeing the warning that comes with the verification code that made her stop and think about it.
- Try to stay alert for red flags whenever you are conducting business with someone you don’t know. Cash apps can be legitimate, but they are generally less secure than credit cards that offer fraud protection. Sellers who don’t have a selling history or buyers who refuse to go along with whatever procedure you put in place for your own safety should set off warning bells. Try to dig around and do your research before diving into any kind of money exchange with an online stranger.
 Shortened LinkedIn URLs
Shortened LinkedIn URLs
According to Avanan, an email security company, scammers are using shortened LinkedIn URLs to disguise malicious links.
LinkedIn automatically shortens links that are longer than 26 characters. The URL is shortened to a “lnkd.in” link followed by several characters. Attackers are abusing this feature to avoid detection by users and security filters.
Examples report emails about missing information needed to move forward on a project, but the content of the message could be pretty much anything, and the target could be pretty much anyone.
By using a shortened link from a legitimate service, we are less likely to be suspicious. And the multiple redirects through harmless sites helps to fool security technologies that check for ph!shing pages. Ultimately, the link leads you to a page to download a pdf or tries to harvest your credentials.
“Check Point Research found that LinkedIn is the sixth-most impersonated brand in attempts globally in Q2 2021. That’s up two spots from Q1 2021.”
What can you do against this?
- Continue to be vigilant with every message, especially those with links or attachments. Scammers will continue to use more sophisticated tactics to hide their true intent and to get past the tools businesses put in place against them. Hovering over this link would likely do you no good, and that information can be manipulated as well. So it comes down to what you do when you are faced with the landing page. Question everything. If the email asked you for information, why would it offer a pdf to download? If you click on a link and end up on a login page, why would your login be the way to answer their question? Always stop before entering your credentials somewhere you did not navigate to independently.
- Keep reporting any scam messages you see, and remember that you can always ask your IT team to check messages you have doubts about. Trust your gut whenever something seems strange, and don’t hesitate to pick up the phone or send a chat to someone when you have a question.
Top 3 Scams – September 1, 2021
According to the latest Cyber Risk Index, scams are not going to stop until we learn how to stop engaging with them. See more highlights from the report before this month’s top 3 scams.
Cyber Risk Index (CRI)
Trend Micro and the Ponemon Institute investigate cybersecurity gaps
“Overall, the North American risk increased from the previous results and was the highest.”
- 78% of North American organizations have experienced one or more attacks in the last 12 months
- 15% have experienced seven or more attacks in the last 12 months
- Trend Micro estimate a 77% likelihood that organizations will suffer a critical data breach in the next year
Click here to view an infographic of the report’s findings, as well as an executive summary, and more information.
 LinkedIn Job Listing Scams
LinkedIn Job Listing Scams
LinkedIn, known for its business networking and recruiting tools, is often the first place you look for jobs nowadays. But Bleeping Computer researchers want you to be very careful before applying.
“Anyone can post a job under a company’s LinkedIn account and it appears exactly the same as a job advertised by a company… For example, if Google’s LinkedIn company page is vulnerable, we will be able to post a job on their behalf and add some parameters to redirect applicants to a new website where we can harvest [personal information and credentials].”
There have already been examples of fraud through the LinkedIn platform, and common wisdom has been to beware of recruiters since anyone can create a fake profile and claim to be recruiting. This scam is a little trickier because it is not a person. It is a job posting listed under a company profile. There is no obvious red flag. And when you are the one doing the searching and taking independent action, you don’t feel targeted and may be less alert.
How can you avoid this scam?
- As an individual: Carefully consider what information is being asked of you to submit. Your social security number, for example, is often required at some point in the job application process. But you may want to re-think sharing it unencrypted through a social networking site. When a company requires such sensitive information, ask them if they have a secure, private application portal. Same goes for your birthday and other personally identifiable information you wouldn’t typically include on your resume. And don’t be afraid to reach out to individuals at that company if you have questions or feel like something is ‘off.’
- As a company/employer: The first quick thing you can do is check your own job listings. Make sure the only ones out there are what you created, and report any that aren’t. Another fun discovery from the researchers is that you cannot take these unauthorized job posts down even if you are an admin on your company’s page. However, anyone can report a posting by clicking on the 3 dots in the right-hand corner. Companies can also email LinkedIn’s trust and safety team to ask about authorized user options and getting them enabled: tns-SAFE@linkedin.com.
 Pandemic Trends Continue
Pandemic Trends Continue
For scammers, the global pandemic is the gift that keeps on giving. The latest theme uses vaccinations and your HR department. INKY, an email protection service, describes the recent timeline and campaigns they’re seeing:
“In [spring], INKY data analysts began seeing campaigns that aimed to take advantage of people’s uncertainty about returning to the office. In June, things were looking positive. By August, the Delta variant cast its pall over everyone’s hopes for going back to normal. First, vaccinated workers felt nearly invulnerable. Then, breakthrough cases started making the news. This confusion was a perfect environment for black hats to introduce a new form of [scam].”
The messages they see now appear to come from HR. You’ll get an email claiming that a vaccination status form is required per county or company rules. The language is believable, and the sender is typically a legitimate, though hacked, account. There is a link to the form that takes you to a Microsoft login page. If you login, you will have your credentials stolen.
So how can you stay safe from this?
- As with any scam that targets internal communication at your company, know what to expect first. Get familiar with who will send emails out from HR–will it be a department email or certain individuals? Carefully check the sender information on anything that appears to be internal yet uses a link rather than an attachment. And pick up the phone to speak to your HR people if you have any questions or doubts.
- If you do click on the link in the email and you come to the login page, stop. Always be suspicious of pages requiring your credentials that you did not independently navigate to. Carefully check the URL of that page, looking for minor misspellings or numbers used to look like letters at first glance. And again, ask your HR people before logging in to an external webpage to view a required form that they could have sent as an attachment or told you where to find in your company’s shared drives.
 Microsoft Warning – 3 Different Angles
Microsoft Warning – 3 Different Angles
In a recent warning from Microsoft, three different ‘campaigns’ were found trying to deliver the same malware. Each attempt is similar to another I’ve shared in the past (see October 2020 and April 2021), and all 3 can be foiled if you remain alert.
What makes each one dangerous is what the criminals learn about our security systems and behaviors. For example, sending a Word document with a macro in it will likely set off alerts, but a zip file can slide by depending on what it contains and how your email filters are configured. Likewise, an email from outside the company would typically raise more flags or concerns than the same message coming from the company website. The criminals see what we click on and what we don’t, and then they send more of the kind that were effective.
Angle 1. This message comes to you appearing as part of another email thread, meaning it looks like someone you know. There will be a zip file attached to it, marked as some sort of information you need or requested. The zip file is password protected, and the email will contain the password. If you use the password and open the attachment, you will download the malicious software.
Angle 2. Your website’s contact form is used to submit some kind of phony threat. Typically, this message is about stolen images on your website and contains links to ‘prove’ the original content or copyright info. If you click on those links, however, you will download the malware. Apparently some people are still falling for this attack because they are afraid of the threat and they mistakenly believe the message is safe because it came from the company website. Unfortunately, many businesses configure their email filters to allow website form submissions, which can mean those messages bypass or go through less scanning than typical external emails.
Angle 3. You get a message designed to make you call the scammers. It may be a fake ticket confirmation to a concert or travel, which of course you will want to get a refund on. Back in April, the trend was a fake renewal for some software at a high price. In any case, they want you to call. A fake call center will answer and talk you through the cancellation or refund process. At some point, you will need to download a file. If you do, that file will have a macro in it that downloads the malware as soon as you open it.
What can you do against this?
- Continue to be vigilant with every message, especially those with links or attachments. Stop yourself when you notice an emotional reaction, such as fear or anger, and remember that scammers often try to use emotions to get you to act without thinking.
- Keep reporting any scam messages you see, and remember that you can always ask your IT team to check messages you have doubts about. Trust your gut whenever something seems strange, and don’t hesitate to pick up the phone or send a chat to someone when you have a question.
- With all the millions of people affected by various data breaches, combined with most people’s habit of re-using passwords, it is easier and more likely that someone you know will have their email compromised. You can help keep this from spreading by being alert, by practicing good password hygiene, and by encouraging others to be more cybersecure as well.
Top 3 Scams – August 1, 2021
 An Olympic Scam
An Olympic Scam
As with any global event, the Olympics are expected to be a popular topic of scams. TechRepublic reported:
“Events like the Olympics serve as an amplifier for cybercrime,” said Emily Wilson, vice president of research at Terbium Labs. Cyberattackers will be exploiting the “increased distraction around the Olympics, allowing them to be more successful.”
The warnings from last year about tickets, travel, and fake contests became less relevant as the decision was made to not allow attendees this year. But there are still scams to look out for.
Be careful of first-to-know winner lists and updated medal counts. Behind-the-scenes streaming links from spoofed companies and any videos trying to appeal to your emotions should also be treated with suspicion. Those are your ‘devastating moment’ or ‘shocking finish’ clips we can’t help clicking on. And be aware that these may come to you as emails or SMS texts.
This is not to say that all sensational headlines are scams. Unfortunately, even legitimate sources use click-bait language sometimes. But it does mean that scammers will try to sneak their similar-seeming emails in along with everyone else. So be on your guard.
How can you avoid this scam?
- Familiarize yourself with the legitimate emails and texts you receive. If you have the NBC News or Sports app, for example, it would be unusual to get a text from them rather than a notification in the app. If you get their emails, make sure the logo is correct and current. You may quickly glance at an email and recognize the NBC logo, only to find it is an old one the scammer copied off the Internet. Keep in mind you can navigate to legitimate articles and videos without clicking on questionable links. Anything accessible only to subscribers, meaning you have to log in, should especially be done independently.
- Always pay closer attention to messages about global topics or trends. When the audience is literally the world, the scams will follow. So look at the details: match the sender’s name and the sender’s address. Read carefully, don’t skim. When we skim, we see what we expect, rather than what’s there, and we can miss mistakes. Trust your gut if anything seems ‘off,’ and don’t click if you’re not sure.
 Word is Innocent
Word is Innocent
Scammers are using a new technique to bypass scanning tools for malicious code. McAfee Labs discovered it just a few weeks ago and explain how it works.
You’ll receive an email with a Word attachment. There is no malicious code in the Word attachment, so it passes through your email filters.
Once you open the Word document, you’ll see some sort of message about the document being ‘created in a previous version of Word,’ and that in order to view or edit it, you’ll need to enable macros. You know enabling macros is a red flag, but it looks like a reasonable Microsoft message. And the email wasn’t flagged as malicious…
If you do enable macros, a password-protected Excel document will be downloaded from a remote server. Then the two documents essentially talk to each other, taking data from the Word document and entering it into the Excel document as functions to create a new macro. This new macro turns off the policy that enables your macro download warning for Excel and then Excel downloads the malware.
It is creative and dangerous.
So how can you stay safe from this?
- The good news is that if you still abide by the ‘never enable macros’ rule, you will be safe from this. And if you are tempted to enable anyway, you can (and should) ask your IT team to check the message and attachment for you first.
- Remember that these scams are just business to these criminals. And that means they will continue to come up with new ways to make money. You wouldn’t keep spending money making a product no one buys anymore, and neither will they. They will continue to work on bypassing the tools we have in place, which means we have to stay alert. So always, no matter what, think before you click.
 Milanote on the Rise
Milanote on the Rise
Along the lines of last month’s warning about Google docs, Milanote is being used to disguise malicious links.
Milanote, if you are not familiar, is similar to Microsoft’s OneNote. It’s a note-taking collaboration tool used by big name companies like Uber, Google, and Nike, and it is legitimate. Recently, analysts at Avanan, an email security company, noticed a dramatic increase in attacks using files hosted on Milanote.
1,367 out of 1,430 emails to be exact. 95.5%
How it works is as an email with a pdf attachment. The pdf is supposedly an invoice of some sort, and the email is a typically worded business message. Both email and attachment go through email filters without being flagged because there is nothing malicious. The pdf is a brief one-liner with a button or link to the ‘actual’ invoice, and it is an authentic Milanote link.
The scam is if you click the link on the invoice and go to the Milanote page, on the Milanote page is another link. This is the bad one.
What can you do against this?
- Just as you should automatically stop when presented with any kind of login screen or credentials page that you did not navigate to independently, begin to think of click trails like this. It should cause you concern to receive an attached invoice that is not actually an invoice. It should make you outright suspicious if that attachment leads to yet another link. No legitimate business should make you click 3 times to view what they expect you to pay. But this still works sometimes because we get invested. We’re curious enough to click once. That doesn’t show us, so we click again. Now we’re really curious. What’s at the end of this trail? It’s human nature to wonder and to solve mysteries, but there needs to be a stronger imperative to stop now.
- Also remember the basics such as whether or not you should be receiving an email about an invoice in the first place. Double-check the sender and sender’s email address. Is there any reference to a project or order number? If you recognize the sender, give them a call first. And as always, ask your IT team to check it out for you.
Top 3 Scams – July 1, 2021
 Watch Out for WIM Files
Watch Out for WIM Files
Windows Imaging Format (WIM) files are showing up in current attacks according to researchers at Trustwave. This file type was developed by Microsoft to deploy software components and updates. It isn’t commonly thought of as potentially malicious, so it’s more likely to bypass security filters. It’s also a sign of the creativity of these criminals – as we catch on to their tactics, they will change their approach.
The way this recent scam presents is an an invoice or information from a courier service. The attached WIM file has malware hidden inside that will be installed on your computer if you open it.
How can you avoid this scam?
- There are 2 positive aspects about this method of attack. It’s an unfamiliar file type to most people, which should raise a red flag. It’s also more difficult to open a WIM file than just clicking on a typical attachment. Like a zip file, it involves extracting, which means you should be prompted before the real damage is done. This doesn’t make it safe though, so stay alert.
- As with any unsolicited email with an attachment, stop and think before you click. Who is the courier? If you have not shipped something, it wouldn’t make sense to be getting an invoice. Do you normally receive invoices? If not, call your IT partner and have us check it out first.
 Exploiting Google Docs
Exploiting Google Docs
Sharing documents through Google is incredibly common now, even among Microsoft 365 users. Many businesses use Google Workplace, and billions of individuals have personal Gmail and Google Drive accounts. Scammers want to capitalize on this and have figured out how to use this legitimate Google service and the way it renders HTML to send emails that have authentic Google links and hide their true intent.
Two hugely successful methods have been reported by experts. One involves sending a document-sharing link and the other appears to be a notification from DocuSign. These emails look convincingly real and have authentic Google Docs links because of how the criminals have used these public Google services. In both examples, however, the next step holds the danger.
In the document-sharing example, you receive an email with a Google Docs link. The link looks fine because it is actually coming from Google. But when you click through, the page you land on is actually a custom HTML page made to look like the Google Docs sharing page. And the download link there will send you to a fake sign in page where they will steal your credentials. The URL on the fake sign in page will show that you are no longer on Google’s website, but when everything else looks familiar, it’s easy to forget to check.
Similarly, the DocuSign email appears as you would expect it to because of how it was created in Google Docs. It is a spoof, however, and clicking the View Document button takes you to a Google Docs page that is made to look like the DocuSign login, not the actual DocuSign website. The login button on that page has a ‘listener’ embedded that will send your credentials to the criminals when you click it.
So how can you stay safe from this?
- We need to accept that scammers will continue to evolve their tactics to make money. It used to be that all you needed to do to check a link was to hover your mouse over it and see where it was pointing before clicking it. But with email sending services that mask legitimate links for tracking purposes, and this new trend of hiding behind authentic Google Docs links, we need to be more careful. I won’t say don’t ever click another link. That would be ridiculous. But any time you do click a link, if an action is requested after that, such as a login or download, stop. Check the URL. Check with the initial sender. Or ask us to check it out for you first. The threats keep changing, and we don’t expect you to recognize every danger on your own.
- Remember that your natural human curiosity can be used against you. Wondering how much that invoice might be for or what’s in that shared document someone sent to you is designed to make you click. Stay alert even when it’s the 892nd email you’ve received this week.
 Fourth of July Phireworks
Fourth of July Phireworks
Independence Day may not seem as likely a target as Thanksgiving or Christmas, but every holiday brings a surge in scams. Even Amazon Prime Day, more of an event than a holiday, saw verification email scams and more than two thousand new domains registered about Amazon in the last 30 days.
Scammers take advantage of events and holidays for a variety of reasons. For one thing, the time-sensitive nature makes us more likely to click for fear missing out. For another, sending emails at the right time can make them appear more legitimate. Think about receiving a summer barbecue deal in July versus in December; the very same email could be easily dismissed as junk when sent at the wrong time. Events and holidays help camouflage the scammers.
So for the Fourth this year, experts are warning us to look out for fake pandemic information such as updated event listings or health rules, vaccine information or requirements, plus the usual retail sales and deals.
What can you do against this?
- Remember that when a deal seems too good to be true, it usually is. If you click a link for an offer and it then asks you for personal information in order to be ‘eligible,’ find a way to confirm it is legitimate before entering. Navigate to the company’s website independently or look them up and call first. And whenever possible, pay with your credit card online. Reporting fraud and getting your money back is often easier with credit cards, and your bank account information can remain separate and secure.
- Pandemic and vaccine information can be tricky. Scammers typically spoof larger entities at the state and federal level, so look out for new or lifting restrictions notices or government regulations about vaccines. Travel requirements and warnings could also appear. At the local level, rules for attending the town fireworks may really be different this year. To be safe and get the right information, go to your town or county website independently.
Top 3 Scams – June 1, 2021
 Evolving Business Email Compromise (BEC) Attacks
Evolving Business Email Compromise (BEC) Attacks
BEC attacks, also know as CEO fraud, have been around for quite some time now. They have been proven to be successful, which of course means scammers are going to continue to use and develop them. and we recently featured a blog with video about how to combat them. What’s important to look out for now are the different angles these attacks have begun to take.
Recent BEC attacks rely more on social engineering. The messages are more indirect than simply asking for a wire transfer, which can make anyone suspicious. The 3 latest to look out for are ‘the handoff,’ payroll diversions, and aging report scams.
- The handoff can be an email to someone in Finance seeming to be from the CEO. It will ask you to reach out to an attorney about an acquisition or project. The ‘CEO’ and ‘attorney’ both work for the cybercriminal gang, so they can play off each other with questions and ‘information.’ At some point a sum of money will be required, which the ‘CEO’ will approve you to send.
- Payroll diversions typically go to HR and appear to be from an employee. This ’employee’ will ask to update their bank info used for direct deposit. Even if you don’t reveal existing information and send a blank form, the form they send back to you will have their criminal bank account information so the real employee will no longer be paid. It’s a perfectly normal request, so if your process does not have any other checks or verification built in, this can easily slip by.
- The aging report scam could be directed to a variety of departments. In this, an email appears to be from a vendor, requesting an aging report, which is non-threatening. Once the criminal has it, however, he or she can reach out to others, using the invoice and payment details in the report to seem convincing enough to change the banking information to their illicit account.
As KnowBe4 puts it, “modern BEC attacks leverage some really good social engineering that security defenses aren’t able to detect or prevent because there is nothing technical about it.” Criminals are willing to take a little longer to let their targets put their guard down before going after the wire transfer.
How can you avoid this scam?
- Train your people. Make sure everyone knows how much more sophisticated these scams have become. Then build verification steps into your process that require methods other than email. It may be as simple as a text to a personal cell phone, a work chat, or a call to your vendor, but it can prevent a lot of trouble.
- Ask your IT partner to check any emails you aren’t sure of. A message can come to you looking perfectly normal, but sender names and addresses can be spoofed. And with no attached files or malicious links to trigger a scan or filter alarm, the typical email protections can miss these messages. But your IT partner can look more closely.
 Fake Quickbooks Invoices
Fake Quickbooks Invoices
Quickbooks, known as the #1 accounting software for small businesses, is being used in a new global scam.
Bitdefender reports that the campaign began in April. Scams using Quickbooks angles often increase around tax time in the US anyway, but this one isn’t about taxes. This campaign targets the 3 million businesses worldwide that use the software, sending fake invoices and payment notifications.
The messages are simple, claiming to have your invoice attached for review or your order sent once payment is remitted, and they are not only sent to people in Finance or Accounting. They come from a spoofed address that looks legitimate (‘quickbooks@xxxx.intuit.com’) and contain convincing Quickbooks graphics. There is also an Excel attachment that supposedly shows the invoice details.
The real threat is in the attachment. A hidden macro will install credential-stealing malware in most cases. In some cases, the malware has been updated to deliver ransomware as well.
So how can you stay safe from this?
- Always be suspicious of attachments. Curiosity is so hard to control, and when we see an invoice amount, even if we’re not expecting one, we want to know what it’s about. Stop immediately anytime you see a popup asking you to enable macros. As I’ve mentioned before, macros can be useful, but never enable them unless you are 100% certain they are safe.
- Make sure everyone in the company knows about something as widespread as this. You may have employees who don’t know whether or not you use Quickbooks or who don’t understand the risks of opening that attachment. You may have employees outside the Finance Department who order promotional items or office supplies; they need to be warned as well.
- Once again, ask your IT partner to check anything you are unsure of. Emails with attachments that you weren’t expecting seem suspicious when we talk about them like this, but can easily slip into the normal workday without raising any red flags.
 Search Ad Scams
Search Ad Scams
This last scam is not an attack on your business or an email to look out for. But it is serious enough for the FBI to issue a private industry notification about it to financial institutions.
The scam uses ads in search engine results, such as Google or Bing. Cybercrime gangs create fake banking website links that appear as ads or sometimes in organic search results to try to harvest your credentials.
If you run a search, often the first result is an ad pointing to exactly what you want. If you were looking for your bank and it is one of these scam links, once you click on it you are taken to what looks like that bank’s login portal. You enter your login, password, phone number, and security question answers, but you don’t get access to your account as you should. This is because it’s a spoofed site. Instead, the criminals call you, posing as the institution. They involve you in a lengthy conversation supposedly aimed at restoring your access, all while they use your credentials to log into the legitimate site and start making transfers.
What can you do against this?
- Be careful where you click, especially if you are trying to log into your bank account. You may find using an app to be less risky, and you should almost never use an advertising link. This is not because ads are less secure by nature, but they are being paid to show up there. And as Google explains in its Ads & Commerce Blog, they removed 5,000 bad ads per minute in 2019. That’s just how vast the Internet is. Their tools may detect the reported malicious links and known violators easily, but the more sophisticated ones often have to have resources prioritized to find them based on trends and other available data. It’s a game of catch-up trying to prevent anything malicious from being shown to people.
- Always double- and triple-check the domain of any site you are going to log into. Spoofing banks and major brand websites like Microsoft and Amazon, for example, is what these criminals get paid to do. So it takes careful attention to detail to be able to spot the fakes.
Top 3 Scams – May 1, 2021
 Ransomware on the Rise
Ransomware on the Rise
A recent report from Coveware talks about ransomware trends from Q1 of 2021. For one thing, the ransom amounts are higher, on average increasing more than 40%. For another, the attacks are automated and tactical, with law firms and professional services companies being targeted most often. And on top of all that, the average downtime following a ransomware attack grew 10% in the last quarter to 23 days.
The latest information also points to a shift in method – from targeting specific individuals through email to exploiting network vulnerabilities. And disturbing analysis from a threat intelligence group tells us these scammers are creating ransomware cartels, which means gangs or groups of cybercriminals joining together to share resources, tactics, and profits.
As KnowBe4 sums up, “Cartels are also…reinvesting profits made from successful attacks to enhance their tactics. Unfortunately, it is only getting more and more easier [sic] for these ransomware gangs to infiltrate your organization.”
How can you avoid this scam?
- Shore up your network: Run an assessment, do penetration testing. Make sure you have all the latest updates. Go through your user list and current employees and make sure the only people who have access should have it. And don’t forget all the remote access points you may have enabled this past year. It is much harder to protect personal computers and home wifi networks, but you can put policies in place for best practices and educate your team about the real risk this poses to your business.
- Check on your backups. Test them. Make sure their frequency is what you need to recover properly (once a day, once an hour, every five minutes). Many scammers like to infiltrate and sit quietly for a while. They will turn off automatic backups and wait until the last one is irrelevant. Then they block you out of your own system and hit you with the ransom demand. If you’re not regularly testing that your backups truly work and aren’t just a fake log, for example, you will be blindsided.
- Continue to be vigilant about email attacks as well. Just because experts are reporting a trend toward network breaches doesn’t mean scammers will stop sending malicious emails. So if you or a coworker gets a message threatening extortion, or any other panic-inducing topic, remember to stop first. Remind yourself that any message trying to elicit a strong emotion (such as fear), does so with the goal that you will react without thinking.
 Smishing – The Next Frontier
Smishing – The Next Frontier
SMS texting scams are increasing at alarming rates. Proofpoint reported a 328% increase from Q2 of 2020 to Q3. And while it may seem like a personal problem on the surface, it can easily turn into a real business problem. Consider the company cell phones you issue. Or the business tools employees use on their personal cell phones for email or field work. We may like to think of our phones and apps as separate from work, but how true is that when they’re connected to the office wifi?
If you follow our Facebook page, you may have seen some sample texts posted recently. They are actual screenshots of scam texts received by our team. A few texts even addressed the person by name. They come from a variety of area codes and claim to be from companies such as UPS and Amazon. And while they may seem obviously suspicious sometimes, they work.
Take this example: Two Indonesian men were arrested 2 weeks ago for a malicious texting scam that impacted over 30,000 US citizens. The men sent 200 million text messages with links to fake government websites. They got personal information from the 30,000 who clicked and used it to steal 60 million from a legitimate relief program.
The message targeted people who have been out of work due to the pandemic. And although the money stolen didn’t come out of those individuals’ pockets, the personal information of those 30,000 people is now completely at risk. Where and how was it stored? Was it sold on the dark web?
So how can you stay safe from this?
- There are ways to prevent some of these messages from reaching you in the first place. Certain apps are available to do this, and both iOS and Android offer message blocking options. On an iPhone, you can also set messages from unknown senders to be automatically filtered to a separate list. Making sure you’re on the National Do Not Call Registry may help as well.
- Start thinking of texts the same way you do unsolicited emails. If you weren’t expecting it, and if you can’t confirm the sender, be suspicious.
- Be aware of the things legitimate businesses will and will not ask for via text. For example, Amazon states in their Help information, “We never ask for your password or personal information by text.” If you’re not sure about a business’s policies, check their website or call them first.
 Poison PDFs
Poison PDFs
Almost anyone can open a PDF. Even if you don’t have Adobe Reader or some other program, you can often view the file in a web browser. This cross-platform ability makes PDFs the attachment tool of choice in massively increasing numbers. Researchers at Palo Alto Networks “noticed a dramatic 1,160% increase in malicious PDF files – from 411,800 malicious files to 5,224,056” from 2019-2020.
There are various methods most commonly used to get you to click on a link or linked image in a PDF. Look out for coupons, e-commerce account messages such as needing to update your payment information, and images made to look like they link to videos, particularly on financial topics such as stock charts and digital currency.
Also popular are fake captchas that pop up when you open a PDF and ask you to prove you’re human and fake file sharing through Dropbox or OneDrive, for example, to view a document supposedly being sent to you.
All 5 of these examples can be especially effective by embedding links that point to something called a ‘gating website.’ Gating websites can either redirect to one malicious website or to several of them in a sequential manner, rather than embedding the malicious link itself into the PDF. It makes these scams harder to trace and take down. It also gives the scammers the flexibility to change their objective from a credential stealing site to a credit card fraud site without having to rebuild their whole scam.
Efficient, right? As I’ve mentioned before, this is business to them.
What can you do against this?
- Always be suspicious of email attachments. PDFs somehow seem safer to many people, but they can have malicious code or links embedded within them, just like any other file type. Always check the sender and the message for any red flags. Confirm with the sender via phone or chat before opening an attachment, or send any questionable messages to your IT team to check for you.
- Don’t be fooled by captchas. We’ve gotten so used to seeing them on website forms that we associate them with a valid security measure. But when used like this, as a popup from an email attachment, clicking that button is the same as clicking an unknown link.
- File sharing is tricky. We use so many cloud-based programs now that sharing a file via link is often more efficient than sending one as an attachment back and forth. But always stop and think before entering any credentials. And keep in mind that the way you share files internally may be different from how you access them from vendors or partners.
Top 3 Scams – April 1, 2021
 Instagram Scams
Instagram Scams
According to a BBC article from January 31st, “the average number of Instagram frauds reported each month has increased by more than 50%” since the pandemic outbreak last year. This statistic comes from the national reporting center, Action Fraud, which says the amount of money reported lost per month has more than tripled.
There are romance scams similar to the one I sent you in February, and investment schemes without the romance from “influencers” who post photos of their lavish lifestyles that ‘you, too, can enjoy.’ But a simpler scam to look out for involves giveaways.
Contests work on social media to drive up engagement for businesses and to gather new leads. Many are legitimate. But scammers have taken to impersonating the brands and influencers holding the contests. They will reach out to you saying you were chosen and ask for your information or to pay for ‘shipping fees.’ Neither request is legitimate.
How can you avoid falling for this scam?
- We all like to win things. You can still participate, you just need to be especially vigilant about communication surrounding it. Pay attention to the terms such as when and how they will announce the winner. If you are contacted in any manner other than that, be suspicious.
- Carefully check the sender of any message asking you for your information or money. Even if you think it is legitimate. If you weren’t expecting it, find an independent way to confirm, such as by reaching out to the brand through their website or customer service.
 Back to the Office Attacks
Back to the Office Attacks
Now that everyone in Georgia over 16 is eligible to receive the vaccine, the expectation is a quicker ‘back-to-normal.’ And for many businesses, that means a return to the office. Scammers saw this time coming, and reports have already come in of attacks on that topic.
Examples describe surveys appearing to be from HR to gauge employees’ willingness to get the vaccine or interest levels in returning to the office. As a business owner myself, I can tell you we request feedback from our team on a regular basis. Our survey links do not lead to spoofed sites where scammers hope to harvest login credentials, however.
Other reports warn of a fake letter-from-the-CEO link that leads to malware downloads and policy change documents that staff must review before returning to the office.
So how can you stay safe from this?
- First, know your company’s policies on communication. Would this type of information come from a generic HR email address or a particular person? Do they often includes links or attachments, or do you have a centralized system for accessing documents that they would refer to? When in doubt, pick up the phone or send a chat and ask before clicking.
- Always stop before entering credentials on a site you did not independently navigate to or were not expecting to have to log into. That should always be a red flag.
- Any time you have a question or doubt, ask your IT team to check an email for you. You may not be able to point to exactly why you think something is off, but you will more than likely be right. And when it comes to your business’s network, your customers’ security, and your own peace of mind, it is always better to be safe than sorry.
 Targeted Microsoft Spoofing
Targeted Microsoft Spoofing
A sophisticated campaign designed to harvest credentials has recently been stopped by Area 1 Security. As we’ve seen before, however, if it’s effective once, we can expect it to show up again.
This scam targeted C-suite executives, high-level assistants, and financial departments across numerous industries. Part of what made it trickier is that it was sent only to certain individuals in each company. That means you didn’t hear 5 other coworkers asking if everyone else saw that message that didn’t seem quite right.
The scammers also did enough research to go after chiefs during their new-hire transition periods, when they might not know exactly how emails should appear or when a request was coming from an inappropriate sender. Plus, targeting executive level assistants is often overlooked but can be extremely effective as they tend to have access to a wealth of sensitive information.
Research and analysis showed these attacks to be a complicated combination of techniques to try to bypass Microsoft’s native defenses. The emails were well-written, not showing the awkward grammar or typos we use to easily identify spam. They centered on topics such as ‘Important Service Updates’ and Security Policy Updates or Patches that needed to be applied. They used spoofed sites to appear legitimate and sent forged invoices to receive real payments in attacker-owned accounts.
What can you do against this?
- Be suspicious of any links or attachments you were not expecting. Granted, that is harder to do when you’re a new employee without a baseline of normal activity, but being new is also an easy time to ask questions. Ask about everything.
- Stop every time you are sent to a website that requires your login credentials. If you did not navigate to it independently, ask your IT team to see if it’s safe before entering anything.
- Recognize that the old spammy messages so easy to identify with their errors and bad logos have evolved. Scammers build entire kits and programs to bypass our defenses and get into our inboxes. This is business to them, and it needs to be just as critical, if not more so, to us. So look at links carefully before clicking, call and ask about unexpected attachments before opening, and trust your instincts. Ask your IT team to scan anything that seems ‘off’; we are happy to help.
Bonus Scam Alert
This new threat is one to warn your family about. It is typically more effective when received in the home environment rather than at work.
An email comes in claiming that your subscription to some computer protection program has been renewed at an exorbitant price. Examples have referenced Geek Squad, Norton products, MalwareBytes, etc., and can range anywhere from $400-600. The email conveniently includes a phone number for you to call and cancel.
They want you to call.
Getting on the phone with them kicks off an elaborate process that involves well-trained “techs” who understand your confusion and frustration and convince you that the software you know you didn’t download is hidden on your machine and was probably inadvertently installed while browsing the Internet. They promise to locate it, remove it, and then refund your money.
The team at KnowBe4 describes the entire scam process involving two different calls, three different remote control software downloads, and a convincing attempt to log into your online bank account to ‘issue an immediate transfer’ as a refund. Gaining direct access to your bank account is their goal.
What can you do against this?
- Remember not to panic when you see unexpected emails like this. A simple check into your bank account or credit card could have shown that no such charge was made. They try to play on your shock, anger, or fear to get you to act (call them) without thinking.
- Never give out access to your bank account. Any legitimate business should be able to reverse a charge or issue a refund without requiring direct access.
Top 3 Scams – March 1, 2021
 Document and Parcel Delivery Scams
Document and Parcel Delivery Scams
All those package delivery notification scams we’re used to receiving over the holidays are effective enough to have evolved. Researchers report an ongoing campaign based on DHL and FedEx shipping notifications.
The FedEx angle typically comes as an email telling you a document has been sent. The subject line may include a date it was supposedly sent on, and the message contains a few details about the document to seem legitimate. Then, of course, there is a link to view it. If you click on the link, you reach a spoofed landing page for you to enter your M365 credentials.
The DHL scam is slightly different, claiming that a parcel is waiting for you at the post office because of missing or incorrect delivery details. This message has ‘shipping documents’ attached for you to review. If you click to open them, you’ll see a blurred out spreadsheet with an Adobe login box in front. The login box will be pre-populated with your email address, appearing official, and will prompt you to enter your email password.
How can you avoid falling for this scam?
- Remember than any unsolicited message asking you to take an action – to click a link or open an attachment – should be treated with suspicion. Look closely at the details of the sender, hover over the link before clicking, and ask yourself if this is a normal way for someone to send you documents or a package.
- Any time you click an unsolicited link and reach a login page, stop. In this case, ask yourself why FedEx needs you to provide M365 credentials. Or why DHL needs you to log into your Adobe account or your email. Send the message to your IT team and have them (us) check it for you.
- We hate missing out on things – invitations, news, packages, and documents. Social engineering exploits that fact over and over again because it’s human nature. You can read more about it from a former team member here. So if you can learn to recognize the attempt, you’ll be able to stop yourself from clicking into trouble.
 Vaccine Offers
Vaccine Offers
As mentioned in December’s email, the global pandemic is too large a topic to be safe from scammers.
Carl Wearn, head of e-crime at Mimecast explains, “The majority of online scams rely on some form of human error, as it is far easier to compromise a single user than a whole system. Threat actors know this well and are continuing to exploit the human factor by tailoring scams to target current events and the fears of their victims.”
So now that vaccines are available on the national level, the number of targets is the entire population. And experts have recently reported a surge of 350% in vaccine scam emails impersonating the National Health System in the United Kingdom.
The messages typically say you have been selected for a shot based on family and medical history. You simply need to fill out some information to take advantage of the offer. The information you provide, such as your name, date of birth, and credit card details, however, will be sold on the dark web.
So how can you stay safe from this?
- Always carefully check ‘offer’ emails. Is the logo current and correct? Does the sender email match? Is this message from your particular doctor’s office or a statewide or federal agency that would be easier to spoof? Does the offer make sense? For example, if you have already received a shot, wouldn’t they have a record of that? If you call and confirm the message is fake, you may want to report the email as a scam.
- You probably receive legitimate messages from your healthcare or insurance providers. So ask yourself if they ever ask you to fill out information online that they already have. Usually, they just email appointment confirmations, reminders, and notices. Whenever you receive an unexpected message asking you to take an action, call them first.
- Any time your credit card details are requested, be suspicious. Send the message to your IT team and have them scan the email for you.
 Utility Company Threats
Utility Company Threats
Fresh off the headlines, Texas utility companies are warning customers about scams that threaten to turn off their power if they don’t pay overdue bills. This is another example of scammers using major events and trends to target their attacks.
The Federal Trade Commission (FTC) also warns of scammers taking advantage of ongoing extreme weather events to steal utility company customers’ money and personal information.
These scams come in the form of emails and phone calls. They are designed to scare you into complying and giving them money via credit cards, gift cards, or even money transfers. They can spoof phone numbers to appear from legitimate companies, and they can copy real company logos into their emails.
What can you do against this?
- Never give out your banking information over the phone, and be suspicious of any “business” accepting gift cards or money transfers as payment. If you take a call like this, get as many details as you can and then get off the phone. Call your utility provider independently.
- If you get an email like this, recognize that it’s trying to scare you and stop yourself. Don’t click on anything. Navigate independently to your account and see if you have any official messages there.
- Tell your friends and family members about these scams. Victims can lose hundreds and thousands of dollars when they’re not aware of these tactics that begin to seem so obvious to those of us who deal with them all the time. Let your IT team help you, report scams whenever you see them, and consider implementing employee awareness training to give your staff practical experience.
Bonus Scam Alert
With tax time and the added questions surrounding stimulus checks this year, experts are warning about W-2 scams and related threats.
As more and more companies allow employees to opt for digital delivery of their tax documents, rather than waiting for them in the mail, scammers are taking advantage. They send messages claiming to be from HR with malicious attachments or links to download your W-2. They may also try to send ‘Need to Know’ facts about your tax filing this year, or even ‘ways to avoid claiming your stimulus money as income.’
What can you do against this?
- Check your address book right now to see what messages should look like coming from HR. If you do get a message from HR and you’re not sure it’s real, pick up the phone (or chat) and ask.
- Be sure to check all your tax filing questions at irs.gov or with your accountant.
Top 3 Scams – February 1, 2021
 Medical Providers Targeted for Wire Fraud Scheme
Medical Providers Targeted for Wire Fraud Scheme
The FBI has reported a scam targeting medical professionals. Individuals pretending to be members of a medical board, FBI agents, or DEA agents contact medical professionals and claim that their licenses have been compromised and are being used in a scheme to traffic drugs.
The scammers then direct the medical professionals to wire money as non-compliance fees and as refundable bonds to “move the investigation forward.” These funds are sometimes promised to be returned within three days. Some medical professionals are even told to transfer funds to additional foreign bank accounts because of “other entities that are linking fictitious accounts” to the target’s personal, business, and investment accounts.
This scam typically presents through texts and phone calls, often at the target’s workplace, and often using spoofed numbers. In some cases, email is used for contacting. Official-looking faxes containing ‘evidence’ are sometimes sent, often including publicly available information such as the target’s license number, business address, or National Provider Identifier.
How can you avoid falling for this scam:
- With spoofed numbers, this scam be a little trickier to identify. A spoofed number is when the information sent to your caller ID is deliberately false and typically made to appear as an official, recognized number. What you can do, however, is gather all the information you can, such as the ‘agent’s’ name, title, and badge number, and then get off the phone. You can then visit the agency website they claim to represent and call one of the numbers listed there. Do not simply re-dial the call you received. You should be able to confirm that the agent is legitimate, or you can then report the scam.
- Remember not to give away any of your own personal information on unsolicited calls. There is a wealth of data available to the public that can make a person seem legitimate, but if you did not initiate the call, be suspicious. Do not confirm anything. Get whatever information you can and then independently try to verify it.
- Always be suspicious of unsolicited requests to wire money, especially over the phone. Regulated agencies typically send letters in the mail and will have secure portals for legitimate fee payments. And they don’t often sound like something out of The Sopranos (needing money to ‘move an investigation forward’).
 Beware that New Suitor
Beware that New Suitor
With Valentine’s Day just two weeks away, this next scam couldn’t be more timely. Interpol has issued a notice to its 194 member countries of fraud schemes starting on dating apps.
Scammers create accounts on dating sites and build artificial romances. Once the relationship has reached a level of regular communication and trust, the criminals start sharing investment tips with their targets and invite them to join in money-making schemes.
According to Interpol, “Victims download a trading app and open an account, buy various financial products and work their way up a so-called investment chain, all under the watchful eye of their new ‘friend.’ They are made to believe they can reach Gold or VIP status.
“As is often the case with such fraud schemes, everything is made to look legitimate. Screenshots are provided, domain names are eerily similar to real websites, and customer service agents pretend to help victims choose the right products.
“One day, however, all contact stops and victims are locked out of the account. They’re left confused, hurt, and worried that they’ll never see their money again.”
So how can you stay safe from this?
- Always be vigilant with strangers, especially when it leads to a request for money. And yes, someone on a dating app who you have not actually met, no matter how many pictures they have or how much you “click” when you chat/email/talk, is still a stranger. Online anyone can say or be anything.
- Be skeptical and do your research. If an investment deal sounds too good to be true, it probably is. Look up reviews for the app or trading website, and Google it to see if it has been reported by others before you.
- If you’re looking for love in all the wrong places, ask people you know to help set you up or join local groups. Dating apps can be great. But they won’t do the kind of screening your friends and family will. And if you do get scammed, report it so someone else won’t be.
 Not Actually Government Assistance
Not Actually Government Assistance
It’s a new year with new government officials in place, and the scammers are happy to exploit it. Experts are reporting scams that pose as government assistance programs and target individuals.
This scam typically arrives through email and speaks of “emergency financial aid,” in one example. Compensation can be as high as five thousand dollars, and the message typically includes a link for details.
The emails are short and could seem plausible, given the stimulus conversations, small business programs, and other funding packages mentioned in the news. But if you click on the link for details, you’ll go to an official-seeming “government” site that asks for your personal information. If you submit the data, you’ll be told that someone will contact you soon. They won’t.
What can you do against this?
- Look for the basic indicators first: spelling or grammar mistakes, the sender name not matching the sender email, and anything else that seems ‘off.’
- If the message passes the ‘sniff test,’ continue to use caution. Hover over the link before clicking on it. See if you can determine any particular program or government agency the message is supposedly from. If you’re still not sure, send it to your IT team to test it. The link may not be malicious, but your technology partners can find out more in a protected environment so you and your data are not at risk.
Bonus Scam Alert
Experts are warning that fake Parler links and downloads may soon hit the masses.
As you may recall from the headlines, Parler was the new social media platform that quickly attracted a large fanbase and was almost as quickly de-hosted by Amazon Web Services and removed from the Apple and Google app stores.
A couple of weeks ago, 70 TB of Parler data was leaked online. That data dump reportedly includes user profile data, user information, admin rights data, videos, and posts (including deleted posts).
So according to KnowBe4, “This massive haul of leaked data could allow malicious actors to individually target Parler users in campaigns as well as all manner of online scams.”
What can you do against this?
- Former user or not, never click a link to download an app in an unsolicited message. If you were expecting a confirmation, okay (though I still don’t recommend it). But if a message comes to you out of the blue, go to the app store independently to ensure you are downloading the correct app and the most recent version.
- Remember to make yourself pause if any message seems to elicit a strong emotion, whether that’s excitement, fear, anger, etc. For example, if you were a Parler user upset by it going down and thrilled to hear it’s back up, you should still try to verify it some other way before clicking. And if you are disgusted to hear it’s back up, or curious to see what it’s really like, again, try to verify it independently first.
Top 3 Scams – January 1, 2021
 Don’t Fall for the Fax Notification
Don’t Fall for the Fax Notification
A new scam has been reported that targets businesses and seeks to gain Microsoft 365 credentials.
It arrives as an email notifying you of a fax. The notification appears to come from various legitimate electronic fax services, like eFax, for example, and the email can also be sent from a legitimate, though compromised, email account. This is how it gets past most spam filters.
The message typically includes a thumbnail image of the fax and tries to pique your curiosity enough to click a link to view the document. Once you do, however, you will find yourself on a fake Microsoft login site where the scammer hopes you’ll enter your credentials.
How you can avoid this scam:
- First, know what electronic fax service your business uses, if any. That way, you can immediately rule out any notifications from other programs as scams.
- If the message you receive looks authentic enough that you click to view and you arrive at a Microsoft login page, numerous alarms should go off in your mind. Check with someone in your company about the protocol for receiving digital faxes, or, better yet, send the notification email to your IT support team. Let us test it for you.
- Always be suspicious of login pages you did not directly navigate to. Consider the level of access you could be giving away versus the information you may receive. Did anyone tell you to expect a fax? Do you normally receive information via fax? And if so, is this the standard method you use for retrieving them? If anything seems strange, ask first.
 Take a Moment to Zoom Out
Take a Moment to Zoom Out
Scammers like to capitalize on what’s popular. So now that using Zoom and other conferencing tools has become the norm, it is the topic of numerous phishing attempts.
You may receive an email, text, or social media message, complete with Zoom logo, saying your account has been suspended…but can be reactivated by clicking on an enclosed link. Or you may be alerted to a meeting you missed…and you’ll find a convenient link with details and possibly even a way to reschedule. You may even receive what looks like a welcome message, as if someone else invited you…which of course you can accept by clicking on the enclosed link to activate your new account.
However, if you click on any of those links, you will either find yourself on a login page for stealing your credentials, or you will have automatically begun downloading malware.
These messages work because we often need Zoom for our jobs. Or it’s the only lifeline to faraway family and friends. So the messages play on the fear of missing out, and they disguise it with realistically copied branding.
So how can you stay safe from this?
- Always think before you click. If you receive a warning that your account has been suspended, navigate to the website independently and log in. You’ll be able to see and address any issues. If you get notified of a missed meeting, check your calendar first. A quick glance could confirm that you had nothing scheduled in the first place. And if you receive an invitation to activate your account, you can often sign up without clicking any links. Simply go to the program’s website and create any account you want.
- The main reminder here is to stop yourself before clicking. No matter what the message says, ask yourself why you’re getting it. If it seems legitimate, ignore the link and log in independently. And, as above, you can always send such messages to your IT support team to check for you just in case.
 DMV (or DDS) Text Scam
DMV (or DDS) Text Scam
The state of New York’s Department of Motor Vehicles recently reported a smishing scam. A text went out to people claiming to be from the DMV. It said they needed to update their driver’s license information because of a new compliance requirement. The text contained a link to a fake NY DMV website where the scammers tried to collect personal information.
Despite this only being reported in NY so far, it could roll out in other states. And with all the ways we interact with businesses online, a text with a link is not as obvious a ploy as it once was.
What can you do against this?
- Look for any telltale signs first: spelling and grammar mistakes, the sender not matching who the message says it’s from, and a URL that is not the official, secure webpage it should be.
- Beyond the basics, train yourself to stop before clicking on any unsolicited links in texts or emails. In this case, navigate to the DMV website independently where you can safely log in and see any official notices. Most government agencies tell us they will never ask you to transmit personal information through email or over the phone. They send letters in the mail in order to protect your security. So if you get a message like this, take a screenshot and report it, and then delete it.
Top 3 Scams – December 1, 2020
 Unhappy Holidays
Unhappy Holidays
Tis the season…for an increase in shopping scams.
From unbelievable deals to undeliverable packages, and even fake charities, the holiday season scams that proved successful last year have returned.
You may have already seen a Black Friday or Cyber Monday email offering a thousand dollar TV marked down 90%.
You may have been sent a text message that your FedEx parcel couldn’t be delivered and you need to click on the tracking link in order to update or confirm the address.
You may even have been called and asked to support a heart-warming charity trying to help those in need this particularly difficult holiday season.
At first blush, any of these could be legitimate. To protect yourself when they aren’t, please keep in mind the points below.
And if you enjoy video, watch this three minute interview at WTOC where Cyreia Sandlin and Chuck discuss some warning signs of these typical holiday scams.
How to stay safe:
- ‘If it’s too good to be true, it probably is.’ It’s an old saying that’s still true. When you see an incredible offer, ask yourself how the company could stay in business if it were real. In the example above, is the TV not worth the original, thousand dollar price? If it is, how could the company last selling it for one hundred dollars? And if it’s not, then what else about this ‘deal’ isn’t true?
- Before clicking on any link, whether in text or email, train yourself to stop for a second. A tracking link or delivery issue is such a plausible topic that these scams continue to work. But check for signs of a generic message that could be sent to multiple people. For example, does it address you by name? A legitimate company will have your account information. Does it have any identifying details of the order? And is it from the right shipping company? You may not always know when a business uses UPS rather than FedEx, but you should have a confirmation email you can refer back to. Rather than clicking on the unsolicited message link, go back to the original, official one.
- If you are approached by a charity, whether by phone or email, do your homework before giving. There are so many legitimate organizations working tirelessly to improves the lives of others and relying on your help to do so. Unfortunately, there are also others that come up with similar names and missions solely to steal your money. So ask questions. Don’t let them rush you. Look them up independently. And feel free to say, “no.”
 Fake Teams Update Ad
Fake Teams Update Ad
This scam has been used to target numerous industries, most recently education (K-12). It appears as an ad, trying to lure you into updating your Microsoft Teams software.
What’s particularly dangerous about it is that simply clicking on the ad starts downloading the malicious payload. You won’t be sent to a landing page first where they can try to steal your credentials and where you may see signs of a scam. Instead, your click starts a script that will typically steal your sensitive information and open a backdoor into your computer (and network). You’ll also get an authentic copy of Teams installed to help hide what’s really happening.
So how do you avoid a trap like this?
- Always be careful of ads. If you see one that sounds appealing, navigate to the website independently and see if the offer is real. You can also open a new tab and search using the terms in the ad to see if it has been reported as a scam.
- If you’re not already, consider using a web browser that can filter and block malicious websites. A tool like that should keep such an ad from even appearing to you. You can also have settings to block executable files from downloading unless they come from trusted sources.
- With regard to software you need or want, always ask your IT partner first. We’re constantly testing out something new, and we’ve worked with so many programs already, that we can usually give some well-rounded recommendations. And we typically roll out updates to programs automatically during off-hours so they don’t impact your day.
 Vaccine Scams
Vaccine Scams
A global pandemic is the gift that keeps on giving to criminals. Bad actors have already issued scams about current statistics and infection maps, government funding. tracking apps, and employment rights and layoffs. And now, experts expect them to shift to the vaccine.
The logical concerns and questions people have will become the focus of these scams. Issues such as whether the vaccine may be safe, when and where it can be taken, and how much it will cost will be used as bait in emails and online surveys.
Messages seeming to come from HR could have links to insurance coverage information. Emails appearing to be from government agencies or local pharmacies may link to ‘your nearest vaccine location.’ Some may even claim to let you register or reserve your dose in advance.
They will all try to play off your natural curiosity, fear, or concern. They will all cause you nothing but trouble.
What can you do against this?
- Awareness training is critical. Scams used to be easier to spot. They typically had bad or no graphics, and the grammar was atrocious. Now, they can copy company logos perfectly and use tricks to hide their malicious domains. So it’s up to us to be vigilant. We need to know the warning signs and look out for them. We need to stop and think before every click. And we need to tell those around us to as well. Because a network is only as strong as what its weakest link lets in.
- If my team or I can help in any way more than sending this monthly information, please let me know. It’s been a long, strange year, and I am honored to say we’re still here for you.
Top 3 Scams – November 1, 2020
 Don’t Fall for Fake Windows Defender
Don’t Fall for Fake Windows Defender
As anticipated, phishing attacks and hackers continue to become more sophisticated. A new effort to make authentic-looking Windows Defender graphics, combined with some security-related logos such as McAfee, is convincing users to enable malicious macros.
This phishing attack typically arrives as an email with an invoice or other financial files attached. Once you open the attachment in Excel, you’ll see a yellow bar warning you that “Macros have been disabled” next to a button to “Enable Content.” Then on the screen below, where you would typically see the spreadsheet, you see the Windows Defender and other logos with official-sounding steps to view the enclosed information.
At a glance, it can appear authentic. But if you enable the content, you’ll download the Qbot malware built into the document that can steal everything on your computer and leave the door open for attackers to get back in whenever they want.
How you can avoid falling for this:
- It starts with the phishing email, so look for all the usual signs. Check the sender’s name and email address, look for any strange text in the message, and make sure the attachments are appropriate before opening them.
- If you open an attachment that ever requires you to enable macros, stop. In rare cases, when you are one hundred percent certain of the sender and you were expecting such a file, they can be fine. But if you have any doubt at all, ask your IT professionals to check the file for you first. We have scanning tools and other advanced options to investigate securely without putting you or your network at risk.
 Social Media Scams Increase Exponentially
Social Media Scams Increase Exponentially
If you don’t have a single account on Facebook, LinkedIn, Twitter, YouTube, Instagram, Pinterest, TikTok, or any other social media platform, kudos to you. According to Omnicore’s Social Media Benchmark Report 2020, eight out of ten Americans have at least one account, and the average Internet user has eight accounts.
So for eighty percent of us, extra care is required for our social media interactions.
A recent report from the Federal Trade Commission (FTC) found scams on social media to have skyrocketed this year since the beginning of the pandemic. And ZeroFOX researchers, who say their data aligns with the the FTC report, say scamming incidents have increased by more than five hundred percent compared to last year.
The biggest increases in scams focus on money-flipping, money mules, and HR-related gambits.
These angles target people who have lost jobs and income, and their effectiveness means researchers expect them to continue.
Stay safe with these tips:
- Remind yourself that if a deal sounds too good to be true, it probably is. And if it’s coming to you in the form of a social media post or message about a low-investment dollar amount that will come back to you in double, triple, or even more, then it’s most likely not a legitimate investment in the first place. That’s not to say all low-cost investments are scams. For example, you can purchase stock slices from Charles Schwab for as little as five dollars according to their website. Charles Schwab is a reputable business. However, sending fifteen dollars to an individual through PayPal with the expectation that you will receive sixty back in a week is much less likely to pay off.
- When it comes to HR scams, yes, there are real jobs out there. But you have to do your homework. When a ‘recruiter’ you’ve never met sends you a message on LinkedIn and wants you to fill out paperwork with your personal information, be skeptical. Protect yourself by looking into the company they say they’re with. Try to find a relevant job posting. If it’s not listed, ask questions until you are satisfied. Most legitimate recruiters will direct you to a secure website where they track their candidates. If someone sends you a Word document that needs macros enabled, delete it.
 Election Threats
Election Threats
As predicted last month, scams focusing on the election have recently been reported in Florida and Alaska. Despite all the early voting, these last few days will almost certainly reveal more.
This particular scam comes in the form of an email threatening to ‘come after you’ if you do not vote for President Trump. The message sender appears to be the Proud Boys, a group founded in 2016 that currently supports Trump, but the chairman of the group says it is definitely not from them and that they do not send emails.
The scam typically claims to have your information and sometimes includes your street address. It also claims to have access to the voting infrastructure and demands you set your political party to Republican and vote for Trump. Or else.
What can you do against this?
- While it may be startling to receive a threatening email that also includes your street address, try to remain calm. Remember that there are many public records that can include your address. Report any kind of message like this to your election officials, and rest assured that the FBI as well as the CISA are investigating.
- Scams like this may seem laughable to many, but they work by planting a small seed of doubt that it could be true. If your address and email address are correct, look closely at the name that most of these messages begin with. Instances have been reported of a different first name than the recipient, which is an indicator of mismatched data in lists or an error in the scammer’s script. In any event, report any message like this and delete it. Then vote for whoever you want.
Top 3 Scams – October 1, 2020
 Fake Forward Phishing
Fake Forward Phishing
Just in time for Halloween, we have a ‘zombie’ type of phishing attack to avoid. It appears as part of old email conversation, revived and brought back to life.
The message shows up with the genuine subject line and content you previously emailed with someone. The email thread may be full or partial and can date back months or even years. It will now include a link or attachment that the phisher is hoping you’ll click on since the original conversation was real.
Sound scary? You can outsmart it.
How you can avoid falling for this:
- Always look at the sender’s email address. Not just the name that appears, but the actual email address. In this scam, the sender will not be the real person you previously emailed, and you will see a different email address. It works through third-party programs that almost all businesses use, like Mailchimp and ConstantContact. Remember hearing about SendGrid’s spam problem a month ago? This isn’t their fault, but it is an example of how hackers can gain access indirectly. Once in an emailing system, they can harvest what they want and repurpose it into a scam like this.
- Always stop and think before you click or open an attachment. This scam hopes you will see the familiar message and not pay attention to details. Reports have said the link or attachment doesn’t really make sense with the genuine message, so if you slow down and read, you should be able to avoid falling into this trap.
 Scamming Customer Support
Scamming Customer Support
Bad actors are using the contact forms on websites to try to deliver malware.
A typical example would be a message claiming to be from an illustrator whose work is being used without permission on that website. The message would be submitted through a business website form and might include a threat to sue. “Proof” is offered through a link to Google Drive where, supposedly, you could see the original, copyrighted artwork.
It all seems pretty reasonable. But anything downloaded will require that macros be enabled, which then allows the malware payload to be installed.
Stay safe with these tips:
- Repeat to yourself, your staff, and everyone you know to not click on unsolicited links. The fear of being sued is intended to make you less cautious, and it’s natural to be curious about the artwork. But you or your customer service specialist can investigate this in other ways. You may have a webmaster or an internal person who works on the website. You can also do a reverse image search on Google to find more information.
- Never enable macros. Especially in files from strangers. If a message seems legitimate, ask your IT team to find out if it’s safe.
- This particular scam can be so dangerous because the typical filters and flags aren’t being set off. You expect strangers and unknowns to submit through your website forms, and a simple link to Google Drive can be legitimate. So it is critical that they way such messages are handled–the human behavior part–is with education and awareness.
 Special Disinformation Delivery
Special Disinformation Delivery
You’ve probably received at least one phishing email from a delivery service, such as UPS or FedEx, with a fake link to tracking or other package information. It’s an especially popular scam around the holidays. Now, you need to look out for them via text–vishing rather than phishing.
Recently, a vishing scheme like this went viral for two reasons. It went out to a massive number of victims, and then it was inaccurately reported to be tied to human sex trafficking.
The text appeared to be from the US Postal Service containing a link to information about a package. Clicking on the link would bring you to a customer satisfaction survey that required your credit card number. Then, someone shared a screenshot of the text and claimed that clicking on the link would allow the sender to track your location, which would be used by sex traffickers.
What can you do against this?
- First things first, do not click on a link about a package you are not expecting. If you’re ordering more lately, as many people are, check your package status in the app or when logged into the website where you purchased it. Secondly, no legitimate customer satisfaction survey would ask for your credit card number. It’s an attempt to steal your credentials.
- With regard to the conspiracy theory aspect, there is a positive and a negative side. The positive is that the viral sharing of it may have kept some victims from falling for the scam. The negative, however, is that it leads to so many false reports of sex trafficking that the national agency handling the hotline is diverted from real cases.
- Disinformation also leads to mental fatigue that can lead to lower cognitive functioning. You get tired of hearing stories that turn out to be untrue, so you start tuning everything out. You pay less attention, and that’s when a scam will trip you up. And things will only get worse as we near the November election. The election may not be a global event like the pandemic, but it is expected by experts to bring a flood of phishing and social engineering scams. So stay alert, and stay safe.
Top 3 Scams – September 1, 2020
 Spearphishing through LinkedIn Jobs
Spearphishing through LinkedIn Jobs
This scam is currently being reported in regard to a System Administrator job posting on LinkedIn. It’s worth sharing and being aware of, however, because the approach could be broadened and used for any type of job posting on LinkedIn.
This is how it works: a job is posted on LinkedIn. People who engage with the listing are responded to and sent a Word document as part of the application process. The sender claims the Word file is protected under GDPR and that macros need to be enabled to open and use it.
If those macros are enabled, a series of malicious actions occurs including downloading system-specific malware payloads. Credential harvesting, deletion of security log entries, and lateral movement (how cyber criminals try to move deeper within your network) are all part of the attack.
So how can you avoid falling for this?
- Always be suspicious of someone requesting or demanding that macros be enabled. Macros are a series of operations, like a program, that can run on your computer from within a file like Word or Excel. They can be useful and harmless, but they can also hide malicious activities. If you did not build them yourself, or you do not know and trust the person sending you a file with macros in it, do not enable them.
- Go ahead and be skeptical. If you are applying for a job that was posted on LinkedIn, why would you also have to fill out and return a Word document? Does the company not have a website form or other means of accepting applications? You can provide a lot of personal information when applying for a job, so if the process seems strange, call and ask first.
 Job Dismissal Scam
Job Dismissal Scam
In another employment-related scam, Kaspersky, a global cybersecurity company, reports this Q2 trend.
Stay safe with these tips:
- Double- and triple-check any emails claiming to be from Human Resources. Make sure the email address is perfectly correct. Consider whether the message is something that would be coming through email.
- Even when an email appears to be internal, stop yourself before opening attachments. Pick up the phone and check with your HR Department before clicking any links or opening any files.
- It’s easy to get swept up in the emotions of finding out you’ve been fired. That’s what cyber criminals bank on: emotions clouding your ability to think. So train yourself to pause before taking any action on any email. That simple habit could save you a lot of grief.
 Vaccine Phishing
Vaccine Phishing
As we’ve seen time and time again, global issues attract cyber criminal scams. This pandemic alone has seen phishing emails about maps, statistics, tracking reports, funding resources, and employment angles. Now, the messages are shifting to vaccines.
Checkpoint, a leading provider of cyber security solutions to governments and corporate enterprises globally, reports “a doubling in the number of vaccine-related new coronavirus domains between June and July. In fact, 1 out of every 25 malicious coronavirus-related websites’ landing pages is vaccine related.”
The emails being reported can come through with a malicious attachment, prompting you to download the latest list of approved vaccines, or with a link that redirects you to a spoofed medical site where you would enter your personal details in order to get the promised information.
So what can you do?
- Remain suspicious of unsolicited messages related to global events like the pandemic. If you receive ‘groundbreaking’ or ‘unreleased’ information about a vaccine, look carefully at the sender. If it is someone you know, is it normal that they would send you a message like this? If it is someone you don’t know, treat it with skepticism. If you get it at work, report it to your IT team.
- Curiosity, like fear, is a tool scammers use to get you to take action. If you train yourself to always stop for a moment before doing anything with an email, you will be far less likely to fall prey to it.
Top 3 Scams – August 1, 2020
 Voicemail Notification Scam
Voicemail Notification Scam
Many phone systems, like ours, for example, provide the convenience of sending voicemails as attachments to emails. There are phishing scams taking advantage of that, and researchers tell us those scams are increasing. The increase means the scams are effective, so be on guard.
So how can you avoid falling for this?
- Find out what a legitimate voicemail message looks like in your company. Is it a link or an attachment? Who does it come from? If your company doesn’t send messages like this, then report any you receive.
- Stop any time you are asked for credentials. If it is something being requested, rather than a login you are initiating yourself, are you sure it is a legitimate request? Check the URL very carefully, and when in doubt, ask your IT team.
- If you happen to be near your office phone, an easy way to check is to see if you have any missed calls. If you get an email about a voicemail, but you don’t have any missed calls, it is most likely a scam.
 Quarantined Emails Scam
Quarantined Emails Scam
Stay safe with these tips:
- Double- and triple-check any emails claiming to bey kind of Service Desk or IT support team. If it’s from us, for example, the sender email will be support[at]infinityinc.us. It will not say “Service Desk” or come from any .com address.
- If you see an email like this for the first time and you’re not sure if it’s legitimate, ask. There is no harm in checking. And there could be a lot of harm done without checking.
- Always stop before entering your on a site you did not independently navigate to. Did you hover over and carefully check the link before clicking? Does the landing page URL, text, and images pass detailed inspection?.
 Pandemic-related Workplace Lawsuit Scams
Pandemic-related Workplace Lawsuit Scams
You can view the law firm’s litigation tracker information here.
What does this mean for you?
- Remain suspicious of unsolicited messages related to global events like the pandemic. If the message appears to be from your HR department, carefully check that it is the right sender and not a close spoof. You can also pick up the phone and ask HR if they sent such information before opening it.
- It’s natural to be curious if you see a professional-looking email from a law firm about a class action lawsuit. Remember to hover over any links before clicking to see where they point. You can also Google the firm and see if a) it really exists, b) it handles that kind of case, and c) if the information in the email matches what’s online. Then you can pick up the phone and call. If the email is a scam, you may be helping to make them aware of it.
Top 3 Scams – July 1, 2020
 Survey Says…You just got scammed
Survey Says…You just got scammed
Many businesses, including ours from time to time, will send out surveys to learn more about customers, feature requests, how attractive certain offers might be, etc.
In order to encourage participation, it is common to offer some kind of incentive. This can range anywhere from a coupon code or small gift card to entries in a drawing for a larger, more expensive prize.
But Naked Security by Sophos has reported a wave of surveys appearing to be from brand name businesses that are actually scams trying to steal your email login and/or credit card information.
The survey usually comes from a real company the scammers have spoofed. Often, it includes basic business questions you would expect about shopping preferences and store hours. Your suspicion should be raised, however, when they not only ask for your email address, but the password you use to log into it. No one sending you email needs your password to do so.
Aside from that red flag, how can you avoid falling for this?
- Pay attention to the details. In one example they reported, the brand name appeared to be an existing, legitimate hardware store, but the first few questions were about shopping habits at a grocery store.
- Look for indications of urgency. If there is a limited number of ‘prizes’ and they are showing how many (or few) are left as you go through the survey, they are most likely trying to get you to answer quickly and without thinking.
- Trust your gut. If the reward for answering a few survey questions seems too good to be true, it probably is. For example, getting a $1,000 iPhone in return for answering ten questions seems a bit over the top.
- Run if you see any requests for payment information. Well, report the website and then run. Many survey scams ask for a ‘nominal delivery fee’ or shipping cost to make that thousand dollar smartphone prize seem legit. But the form where you enter your credit card information feeds directly to the scammers. Which they will turn around immediately and use. If that happens to you, call the number on the back of your card immediately.
 VPN Impersonation Scam
VPN Impersonation Scam
As so many companies switched to remote work setups, VPNs quickly became a lot more common. That makes them ripe for scams.
A virtual private network (VPN) is a secure type of connection that lets you use a laptop or home computer as if you were on your company’s network. This is a lot safer than most people’s home connections or free wi-fi used when traveling.
The recently reported phishing scam takes advantage of more (and new) VPN users, claiming there is a configuration update. The message often appears to be from your IT support team, but the link for updating it attempts to steal your O365 credentials.
Stay safe with these tips:
- Double- and triple-check any emails claiming to be from IT support. If it’s from us, the sender email will not have your company’s domain. And if it shows up as a contact in your domain, make sure it’s someone you would expect to send that kind of message.
- Ask first. There is no harm in checking. And there could be a lot of harm done without checking. Did your supervisor or IT team warn you this was coming? Did everyone get the email, even staff who never had VPNs set up for them?
- Always stop before entering your credentials on a site you did not independently navigate to. Did you hover over and carefully check the link before clicking? Does the landing page URL, text, and images pass detailed inspection? Does it make sense to give your O365 email and password for a VPN update? If you have doubts about anything, call or email your IT team.
 BLM Phishing Forecast
BLM Phishing Forecast
Current events, especially global ones like the ongoing pandemic, attract any number of scams. Phishing emails can be quickly crafted and sent out en masse to prey on people’s fears, charitable natures, and other emotions.
One of the indicators that cybersecurity experts use to try to predict what attacks we’ll see next is to monitor domain registrations. The increase in registrations of a similar theme or topic shows what society is currently interested in, which is often quickly followed by more registrations with malicious intent.
“For example, over 20,000 domains related to COVID-19 were registered in just three weeks and 17% of them were related to maliciousness,” reports KnowBe4.
It may not sound like much, but that is more than 3,000 domains intended to steal your data.
KnowBe4 goes on to say that “the current blacklivesmatter movement is another moment in history that spammers and phishers are sure to take advantage of. Once you start seeing the domain registrations come, the scammers are not far behind.”
You can see a sampling of the domain names here.
What does this mean for you?
- Stay aware. Not every message about a current event is malicious. But scammers will always try to take advantage of situations when strong emotions are in play. Stay clear-headed, and do not click on links in an unsolicited message.
- Spread the word. Your awareness helps protect you and your network, but what about all the other people who have you in theirs? When we all know the warning signs and best practices, phishing won’t have any hooks left in it.
Top 3 Scams – June 1, 2020
 Covid Data Spreadsheet Scam
Covid Data Spreadsheet Scam
How can you avoid falling for this?
- Remember to always be suspicious of unsolicited attachments. If the content is of interest to you, then go to the source. Johns Hopkins shares a wealth of information on their website that you can access and has publicly stated that they do not send attachments in their daily reports.
- Ask your IT team to scan suspicious emails and/or attachments. You don’t have to figure it all out on your own. If you can’t tell whether something might be dangerous, have your professionals test it just to be safe.
 Scams Targeting the Unemployed
Scams Targeting the Unemployed
Stay safe with these tips:
- While remote work has been steadily increasing in popularity, you should still be suspicious of unsolicited emails or texts advertising such positions. Unless they come from a headhunter you know, they are typically a widespread scam to either steal your personal information or make you an unknowing accomplice.
- Keep in mind that urgency is a tactic used by scammers to get you to click without thinking or doing research. And if an offer seems too good to be true, it usually is.
- Take the time to check a company’s website and call or email their HR department before filling out information for a job. It’s true that not all positions are posted publicly, but if there is a real opportunity, you should be able to speak to a real person about it.
 Contact-Tracing Scam
Contact-Tracing Scam
So how can you protect yourself?
- Stay vigilant. Scammers will always try to take advantage of emergencies when people are worried and fearful and not always thinking clearly. Do not click on a link in an unsolicited message.
- If the message includes information about the app, try to confirm independently that it is legitimate. If you worry it might be true, contact your local health center without interacting with the message link. They can discuss symptoms and risk with you, and you can arrange a test if necessary.
Top 3 Scams – May 1, 2020
 Caller ID Spoofing Scams
Caller ID Spoofing Scams
Well, here’s the happy ending/silver lining:
- You can easily avoid falling for this scam by not engaging in calls “your bank or credit card.
- You don’t have to be rude or tip them off, but you can get off the phone and contact the company using the number on the back of your card or contact information on their secure website. Then when the bank tells you they didn’t call, you can report the scam and let them look into it.
- To further protect yourself, since obviously the scammer has your phone number and the name of your bank or credit card, you can make sure there is no strange activity on any other accounts you may have. You can also change passwords, especially if any accounts share the same passwords (which they should not – get good password hygiene here). And you can consider a Dark Web monitoring service that will alert you if your credentials show up for sale.
 Impersonating the SBA
Impersonating the SBA
Stay safe with these tips:
- Always use caution with attachments. In this case, as well as typically any other government agency, you can find the exact steps that will be used for an application process. Most likely they will spell out the ways they will contact you and what they will and will not ask for.
- Especially when you receive emails with attachments and action requests, check the sender carefully. Does the sender’s email match the sender’s name? Is it spelled exactly right? In this case, is it what the SBA told you to expect?
- Before opening an attachment you weren’t expecting, try to confirm its validity another way. Call if you can, but don’t use a phone number in that message. Perhaps ask someone else who has gone through the process. And if you can’t find a way to check on your own (or you don’t want to), then just ask your IT team. We can help with things like this.
 Notflix
Notflix
So how can you protect yourself?
- Always check and double check the URL of websites you visit. Look for the padlock that indicates they are secure, and check the spelling carefully. Look for double letters or numbers that appear to be letters.
- Whenever you see a free offer, ask yourself why it’s free. There’s a popular saying that ‘if you aren’t paying for the product, you are not the customer; you are the product being sold.’ Now that’s not to say that something like free shipping offers are evil. They are usually just a way of motivating customers to spend more. But an offer to receive Netflix for free, when other people have to pay for it every month, should throw a warning flag.
Top 3 Scams – April 1, 2020
 Stimulus Scams
Stimulus Scams
Now that a stimulus bill has been passed, keep an extra vigilant eye out for scams about that money.
As I sent last month, something as global as the current virus brings a surge of phishing and social engineering scams. Once you add money into the mix, the scams simply shift from sharing information with malicious links and attachments to requests for ‘verifying’ your information before you can receive your money.
Experts from KnowB4 put it this way,sense of urgencyneed
So what should you look out for?
- Be especially careful of any messages claiming to be from your (or a) bank, the IRS, or any other government agency. Whether it’s an urgent need to ‘verify’ your data or a request for your bank account information, hold off. The IRS has previously reported that it communicates primarily through the mail, and as of March 30th announced that distribution of checks will be automatic in approximately three weeks, with no action required for most people.
- If you receive any messages that pass the sniff test, navigate to the sender’s website independently and look for the supposed information there. If it turns out that you did get something legitimate from your bank or the IRS, then you’ll be able to log in safely and find the details in your account.
 Weaponizing the Fear of Infection
Weaponizing the Fear of Infection
Stay safe with these tips:
- Always try to stop yourself when an email makes you feel a strong emotion. Whether it’s fear, anger, or an adorable desire for puppies and kittens, the sender could be trying to push you towards taking an action–opening an attachment, clicking a link to donate, etc. Many times you’ll be fine (that’s what a lot of successful marketing has been built on), but pausing before you do so can save you a lot of trouble in the long run.
- Check the sender carefully. Does the sender’s email match the sender’s name? If it’s a hospital, is it your local hospital or one you’ve never heard of? Is it spelled exactly right? If you look the hospital up online, does it have the same address, phone number, logo, and style?
- Try to find another way to confirm before acting on a message like this. If it’s really from the hospital, then you might be able to find a phone number–not one included in the message–to call and get more information. And if you do decide to act on it and simply go to the hospital, then skip opening the attachment. You know there’s going to be plenty of forms and paperwork when you get there, so why risk it. With the overload our healthcare system is currently dealing with, does it even make sense for them to send customized attachments? You don’t have to be paranoid, but you can certainly question things.
 A New Twist on Sextortion Campaigns
A New Twist on Sextortion Campaigns
So how can you protect yourself?
- Try not to let your curiosity get the best of you when it comes to unsolicited emails and attachments. We’re human, so we’re naturally curious. But before clicking on something like that, wondering if it could be real, ask yourself what could be the worst-case result from it. The answer is most likely a far higher price than you want to pay just to satisfy your curiosity.
- Similarly, try not to let fear get the best of you. Getting a message like this and being afraid it’s true, and wanting to confirm before letting your friend know they’ve been hacked, is both noble and dangerous for your own network. Let them know without confirming the evidence, and you’ll both be safer.
Top 3 Scams – March 1, 2020
 The Health Information that Gives Viruses
The Health Information that Gives Viruses
When something makes global headlines, like the Coronavirus has, the scams are quick to follow. The World Health Organization (WHO) has put out an alert about ongoing phishing attacks that impersonate the WHO and try to steal confidential information and deliver malware.
These attacks come in various forms. One may include a link to an “updated map of confirmed cases” or a map claiming to predict where the virus will spread to next. Others may attach a document of “safety measures” to review and share with your family and business. And others try to get your personal information as a request from the WHO.
There is obviously a lot of information being shared about this virus and ways to try to prevent getting sick as it impacts people worldwide.
So what can you do?
- Be suspicious of any unsolicited messages. Especially when it appears that you have been contacted by an agency such as the WHO, find another way to verify its legitimacy before engaging with anything in the message.
- Independently navigate to the website and find any pertinent maps or information there. If it’s really from the WHO, then it won’t be private and emailed solely to you. There are also other agencies to contact for information, such as the CDC or NIH.
 Beware the Browser Extension
Beware the Browser Extension
We do so much online that adding browser extensions to type less, shop more frugally, and save passwords, for example, can seem like a godsend. But beware: not all browser extensions are created equally.
Google recently removed more than 500 extensions that were found to be stealing private browsing data and perpetrating ad fraud, among other unsavory activities.
They were discovered through an advertising-as-a-service Chrome extension designed for businesses. Rather than help advertise their businesses, however, the users of the extension fell under server commands to visit a round robin of sites to accumulate fraudulent ad revenue. Some sites were benign and others malvertising, or phishing sites. The extension also had code giving itself extensive permissions for accessing data and was able to steal private browsing data from the infected browsers.
Stay safe with these tips:
- Always vet the software you plan to install. Whether it is on a desktop computer, a laptop, or a phone, just because something is available through the Google App Store (or Apple’s or any other), does not mean it is secure. This applies to extensions, plug-ins, apps, etc.
- Remember the saying that, “if you’re not paying for the product (or not sure exactly what it is), then YOU are the product.” If a deal seems too good to be true, it probably is. As one of my employees likes to say, “trust…but verify.”
 Seasonal Scams: Valentine’s Day Edition
Seasonal Scams: Valentine’s Day Edition
According to the FBI’s Internet Crime Complaint Center latest figures, confidence/romance scams cost victims an astounding $475,014,032 in 2019.
As if dating and relationships don’t already cost too much and often end in heartbreak…
That’s just a joke. All these scams can paint a pretty depressing picture, so I like to lighten things up every once in a while. They’re a serious problem, but my team and I don’t want you to feel overwhelmed. You’re already taking an important first step by embracing awareness. And when you’re ready to talk next steps, we’re here.
In any event, holidays will continue to attract scammers. They’re an easy opportunity to send appropriately themed messages that can play on your emotions or seem like a realistic offer to download that dating app full of malware or con artists for an extremely low entry price.
“For cybercriminals, Valentine’s Day is just another holiday and the opportunity for just another scam,” explains Terence Jackson, chief information security officer at Thycotic. “If you don’t know who the mark is, it’s most likely you. Phishing is still the attacker’s weapon of choice, and there will be no shortage of well-crafted emails and messages designed to emotionally engage you and prevent you from making rational decisions.”
Next up will be St. Patrick’s Day. Then Easter, Tax Day, etc. So keep an extra eye out for those ‘lucky’ deals and offers that will send you ‘over the rainbow.’ Many will be legitimate sales, but others will be designed to steal your passwords, your money, and your faith in humanity.
So how can you protect yourself?
- Try to be more aware around all the holidays. There’s usually a lot going on, so scammers think they can slide in unnoticed and catch you clicking on a malicious link while you’re distracted.
- Pay attention to your emotions. When you’re reading or watching something online, and it tugs on your heartstrings, try to pause before opening your purse strings. Generosity should be admired rather than punished, but there will always be bad actors trying to take advantage or others’ good intentions.
Top 3 Scams – February 1, 2020
 Capitalizing on Celebrities
Capitalizing on Celebrities
The news of Kobe Bryant’s death shocked everyone at the beginning of this week. As a beloved athlete and respected entrepreneur and investor, his death made headlines and continues to receive attention and emotional responses.
Bad actors love to exploit this kind of situation in a variety of ways. They’ll use the Bryant helicopter crash as bait with links to ‘special news coverage,’ secret footage, places to post your sympathetic messages, and even as funding grabs for the other victims of the accident.
Whatever tactic is used, you will wind up with either infected workstations at the house or in the office, giving out personal information, or unleashing ransomware on your network.
What can you do?
- Always remember to be wary when someone is tugging at your emotions or offering special access, e.g., never before seen footage. If you receive an email with anything like this, force yourself to stop and look before clicking on anything. Check the sender, and hover over the links.
- Browse to websites independently of email. For example, if a message claims to show an NBC behind-the-scenes special on Bryant or interview outtakes, try Googling it first. If it really exists from NBC, you should be able to find it. They want the website traffic, and they’ll want you to share and post about their content.
 No Such Thing as a Temporary Social Security Number
No Such Thing as a Temporary Social Security Number
Researchers at Kaspersky have come across a phishing site that’s posing as a data leak protection service set up by the US government.
The site claims to be compensating victims of data breaches, offering cash “to residents of all countries around the world.” The website is well-designed and looks like an official government site, despite some grammatical irregularities and the mention of a non-existent “US Trading Commission.”
Users are invited to enter their names and phone numbers to see if they’re entitled to receive compensation. The site warns that entering false information is illegal, but the researchers found that the output will be the same regardless of what is entered.
“For example, we [researchers] inquired about the personal data of a citizen named fghfgh fghfgh. The site pondered for a while, seemingly connecting to a database of information about leaks…and lo and behold, found that our fictional character with an unpronounceable name had indeed had their data leaked. Moreover, it turned out that someone had already used their photos, videos, and contact information, and so fghfgh was entitled to compensation in excess of $2,500!”
After entering your info and seeing how much money you could be owed, you are asked to provide your payment card information and Social Security number (SSN) in order to receive your money.
There is also an option for non-US citizens who don’t have a SSN. They’ll be taken to a page where they can purchase a temporary SSN for just nine dollars. The scam ends after the victim has either provided their SSN and payment information, or after they’ve forked over the nine dollars.
Stay safe with these tips:
- Being the victim of a breach is scary and all too possible nowadays. But you should be immediately suspicious of anyone asking for your social security number over the phone or through a website.
- There are some legitimate services that can see if your information has been compromised. We can perform Dark Web searches for you and your business, and haveibeenpwned.com is a website search tool that you can put your email into and see if it has been involved in known breaches. You can then use that information to change your password and possibly close old online accounts.
 Windows 7 Support Scams
Windows 7 Support Scams
As you know, Microsoft ended support for the Windows 7 operating system on January 14th. Scammers are taking advantage of the long-anticipated news to launch tech support scams, according to the Better Business Bureau (BBB).
These scams are typically conducted over the phone, with the scammer posing as a Microsoft employee. The scammer will use social engineering to either call you out of the blue, or they’ll use computer pop-ups or emails to convince you to call them.
“The caller may seem friendly and helpful, but they are far from it,” the BBB explains. “They may convince you to pay yearly fees (that don’t exist) or request remote access to your computer under the guise of installing software. If you pay the fees, you could lose hundreds of dollars. But if you allow the scammer access to your computer, your secure personal information, such as banking details and login credentials, can be compromised. This puts you at risk for identity theft.”
So how can you protect yourself?
- First, know that Microsoft will never call you unsolicited. They do not offer support by calling or pushing popups on your computer.
- In fact, you should always be suspicious when someone calls out of the blue offering to remote into your computer. Our advice is to tell them you can’t talk at the moment and then call us or report it directly to Microsoft.
- You should also make an immediate plan to upgrade or replace that Windows 7 operating system. Even without scammers calling you, vulnerabilities will continue to be discovered that Microsoft is no longer offering security patches for.
Top 3 Scams – January 1, 2020
 Netflix and Steal
Netflix and Steal
A Netflix phishing scam is going after users’ payment information and Netflix credentials, according to Naked Security. The phishing emails inform recipients that they’ve missed a payment and they’ll need to login and fix their billing information to resolve the issue.
The emails themselves contain some glaring typos and grammatical issues, including repeated misspellings of “invoice” and the phrase “you local bank being held a transaction.” The phishing site itself is more convincing, however.
The scammers took the time to obtain a valid HTTPS certificate, and they’ve hosted the site on a subdomain with a very long URL consisting of random characters. As a result, the primary domain is pushed out of sight in the browser bar, so the user doesn’t realize they are not on netflix.com. The login page looks perfectly legitimate, as does the page to enter payment card details.
The scammers made another mistake, however, by including an intermediate page that asks users how they want to pay their bill in order to “resrtart” their membership. This page offers a number of options, including one to purchase gift cards. The option to buy gift cards is inexplicably written in French, unlike the rest of the page.
While these warning signs seem easy to spot when you know it’s a scam, they might not be so apparent if you aren’t looking for them or if you are in a hurry.
A similar scam is circulating about PayPal, with the message that an unknown device has accessed your account. This one also has one or two grammatical red flags, but overall looks convincing enough to have gained a wealth of personal information from victims.
So what can you do?
- Force yourself to stop and think before clicking on ANY emails warning about account issues or breaches. Our fear of being compromised is what the bad actors count on, but most legitimate businesses will not try to scare you.
- Always confirm issues independently of the links in these types of emails. Open a separate browser window and log into your account; if there is an official problem, you will be able to see and fix it that way.
- Verify account problems by calling. Don’t use any contact numbers included in a message like those above, but reach out and speak with someone if you have questions.
 Selfie Scams
Selfie Scams
Researchers at Kaspersky Lab have observed a spike in fraud surrounding the use of selfies to gain access to sensitive data, Planet Biometrics reports.
Some legitimate online services ask users to upload a photo of themselves holding their ID in order to verify their identity.
If a scammer gets their hands on one of these photos, they can impersonate you online. These photos are valuable on the black market for this reason.
Scammers are collecting these types of selfies via phishing emails that purport to come from payment services and banks. The emails try to convince recipients to go to legitimate-looking phishing sites and upload a selfie with their ID visible.
It’s best to avoid uploading selfies with your ID at all, if possible, because anything you upload to the internet can potentially be stolen at some point. If you do need to do so, make absolutely certain you’re on the correct site and verify that the service is legitimate.
Stay safe with these tips:
- Before confirming your identity in this way, ask the company if there is any other way to verify.
- If you have to do it, look through the site for signs that it is legitimate before uploading. Check that it is secure, showing a locked padlock in the URL. See if there are terms and conditions explaining how they will use your image and how long it will be stored. If you see all this and still have a bad feeling, trust your gut.
 Movie Mania
Movie Mania
TechRepublic reports that Kaspersky researchers have identified sixty-five malicious files masquerading as online copies of Star Wars: The Rise of Skywalker.
The files are spread via phishing sites and social media accounts that pose as official movie pages. In addition to distributing malware, the sites also ask users to enter their credit card data before they can watch the film.
Tatiana Sidorina, a security researcher at Kaspersky, said in a statement that attackers frequently take advantage of popular movies and shows to spread malware.
“It is typical for fraudsters and cybercriminals to try to capitalize on popular topics, and Star Wars is a good example of such a theme this month,” Sidorina said. “As attackers manage to push malicious websites and content up in the search results, fans need to remain cautious at all times. We advise users to not fall for such scams and instead enjoy the end of the saga on the big screen.”
So how can you protect yourself?
- The easiest protection is to avoid pirated material altogether. But the reality is that your network may be shared by others who may not be so careful. So keep in mind (and teach your children) that a company trying to make money from movie ticket sales is highly unlikely to also release a free online version, no matter how authentic their site looks.
- Never enter information, especially payment information, on a site claiming to offer free movies. If it’s free, what could they possibly need payment for?
- Use the Force: that’s your reason, common sense, and your instincts. If something seems ‘off,’ it most likely is.
2019
Top 3 Scams - December 1, 2019
 Top Ten Most Impersonated Brands by Phishers in Q3
Top Ten Most Impersonated Brands by Phishers in Q3
Since this will be the last scams alert of 2019, we thought this blanket warning would be most helpful to start with. There are still two distinct attacks to look out for below. And if you receive our newsletter, you already know about the Disney+ issue (and have hopefully changed your password).
- PayPal
- Microsoft
- Netflix
- Bank of America
- Apple
- Chase
- CIBC (Canadian Imperial Bank of Commerce)
- Amazon
- DHL
Why does this matter to you?
- The old advice of looking for typos and weird grammar isn’t cutting it anymore. Phishing scams today are far more sophisticated. So if you use ANY of the companies listed above—and who doesn’t—be vigilant of messages appearing to be from them.
- If you feel an email from any of these companies is wrong for any reason, trust your gut. Log into your account independently, and if you find out the email was a scam, report it.
- Sometimes your brain can recognize minor variations, such as a different shade of color in a logo or the wrong font, without you consciously realizing it. Maybe the greeting isn’t what you’re used to seeing from that company. Everything else might seem fine: that’s how tricky these criminals are getting.
- Hover over links as always, and recognize fear tactics as a reason to pause. Authentic brands typically don’t want you to panic and lose trust in them.
 Don’t Get Sway-ed
Don’t Get Sway-ed
Malicious actors have apparently decided that the future of phishing lies in exploiting trusted online services. You have undoubtedly seen the upshot of that decision in your inbox: an endless stream of phishing emails pushing links to malicious content hosted on services like Dropbox, Sharepoint/OneDrive, and Evernote, to name a few. Now the bad guys have a new favorite online service to exploit: Microsoft Sway.
If you’re not familiar with it, “Sway is an app that makes it easy to create and share interactive reports, personal stories, presentations, and more,” according to Microsoft. Essentially, you can make mini websites quickly and easily.
So far these criminals have not yet fully exploited Sway’s integration with other online services, such as YouTube and Facebook. (Give them time.) What they are doing, though, is skillfully deploying Sway to leverage the inherent trust that users place in Microsoft in order to trick you into clicking through to slick, convincing web pages that offer an inviting opportunity to cough up your login credentials.
These phishing attempts appear to link to Microsoft Teams, company surveys, file sharing, and voicemail message centers, for example.
Stay safe with these tips:
- Question everything. Is that message really from your coworker? Would HR send a survey link this way? Does that sound like the CEO?
- Pay attention to details, and pick up the phone (or use a separate messaging tool) to confirm with the sender before clicking on any links or files you did not ask for or weren’t expecting.
 Fake Browser Updates
Fake Browser Updates
Malware delivered via fake browser updates is back and more sophisticated than ever.
Leveraging vulnerable website content management platforms–typically older versions of WordPress, Drupal, etc., that can be exploited by non-updated security code or bugs–these attacks seek to trick users into installing malware under the guise that their web browser is out-of-date.
We all know that software, including your web browser, will eventually need to be updated. So, it’s not so out-of-the-ordinary for users to be notified that a newer version of Chrome or Firefox, for example, is available.
Generally, this kind of notification uses the operating system’s normal update mechanisms. But anyone not familiar with how updates usually work, or someone in a hurry, can easily fall for this attack.
The initial malicious webpage performs a ton of browser validation and then transparently navigates the victim’s browser to a malicious page that, in turn, redirects them to a browser update screen that says something like, “You are using an older version of Chrome.” Other details may be included, and then there is typically a big green or red button saying Update Chrome, or the name of your browser.
So how can you protect yourself?
- Be skeptical of updates coming through your web browser as a link to click on. In the case of Chrome, for example, authentic updates will appear as an icon in the upper right corner where you typically see 3 vertical dots and the customizing menu.
- Ask your IT team before clicking. Typically they will handle software updates for you automatically. If you haven’t used a particular browser in a while, manual updates may be necessary and they can make sure it’s done safely.
Top 3 Scams - November 1, 2019
 Performance Appraisal Scam
Performance Appraisal Scam
Recently, experts uncovered a phishing scheme in which cybercriminals try to mimic the performance appraisal process of the target company.
The attack is twofold: Recipients think that the appraisal (a) is mandatory and (b) can lead to a pay raise. It’s worth noting that in some companies such appraisals are a routine part of the salary revision process and that’s why they don’t raise any suspicions.
It all begins, as usual, with an e-mail. The employee receives a message that appears to be from HR, recommending a performance appraisal. The text of the message contains a link to a website with an “appraisal form” to be filled out.
According to the instructions, the user must follow the link, log in, wait for an e-mail with additional details, and select one of three options. For anyone new to the company and its appraisal procedure, the sequence of steps might look convincing. Only the website address (which is unrelated to any corporate resources) could arouse suspicion.
If the employee clicks the link, they will see an “HR portal” login page. Unlike many phishing resources meant to look like login pages for business services, this one looks quite primitive, with a bright monochrome or gradient background and data entry fields covering the page. For the sake of authenticity, the scammers invite the user to accept the privacy policy (without providing a link to any such document).
The victim is asked to enter their username, password, and e-mail address. In some cases, the scammers direct them to enter their work address. By clicking the Sign In or Appraisal button, the employee actually forwards the data to the cybercriminals.
At this point, the “appraisal” is likely to come to an abrupt end. The employee may wait a while — in vain — for the promised e-mail with further details to arrive. In the best-case scenario, they might suspect something is wrong, or send a kindly reminder to the real HR department, which will then notify IT security. Otherwise, the company might not detect the identity theft for months.
How can you avoid this?
- Use up-to-date spam filters to intercept phishing e-mails before they even get close to anyone’s inbox.
- Issue regular reminders that employees should treat any links in emails with caution, opening them only if their authenticity is certain. Simulated phishing tools have proven most effective with this kind of awareness training.
- Remind staff not to enter work account details on any outside websites, and clearly define the types of communication they can and should not expect to come from HR.
- Sign up for Dark Web monitoring. This service searches for any of your business domain credentials listed for sale or otherwise posted on the dark web. It can also be used on an individual basis for identity theft prevention.
 Stripe Credentials
Stripe Credentials
Cofense warns of a phishing campaign going after credentials for the Stripe online payment platform. The attackers are sending emails purporting to be from Stripe Support, telling the recipient that their account details are invalid and their account will be placed on hold unless they fix the issue immediately.
“This is cause for panic among businesses that rely solely on online transactions and payments,” Cofense explains. “Fear and urgency are the most common emotions threat actors play on, spurring otherwise rational people to make irrational decisions.
”A notable aspect of this campaign is the attacker’s use of the HTML tag to hide the destination of the link to the phishing page. The emails contain hyperlinks that say “Review your details.” When the victim hovers over this hyperlink to see what the URL is, they’ll just see “Review your details” where the URL should be.
If they click on the link, the victim will be taken to a spoofed Stripe login page. After entering their credentials, they’ll be asked to enter their bank account number and phone number. Finally, the phishing page will tell them they’ve entered the wrong password and redirect them to the real Stripe login page.
The attackers have taken steps to ensure the victim doesn’t realize they’ve handed over their credentials and bank account details. Many people would simply think they entered the wrong password and then continue to log in to their legitimate Stripe account, where they would see that everything is all right. New-school security awareness training can teach your employees to watch out for these tactics so they can avoid being scammed.
Stay safe with these tips:
- Remain calm in the face of emails about account and password warnings. If you do not use Stripe, then simply delete or report this phishing email as directed.
- Always carefully check links before clicking and web addresses on pages you are directed to. Look for typos, inconsistencies, and anything that raises doubt.
- Navigate to the account in question independently. If there is an actual issue, you will find it on the authentic website.
 Bank Vishing
Bank Vishing
Bank vishing scams – the telephone equivalent of phishing – are growing more convincing and harder to detect, CNN reports.
A San Francisco man describes “the most credible phishing attempt I’ve experienced to date.”
He said he received two phone calls from the same number, and he answered the phone the second time. A woman on the other end told him she worked for his bank and asked if he had just tried to use his card in Miami. He said no, and the woman began to walk him through the process of securing his account.
She asked him for his member number, and he gave it to her. He then received a text message from the bank’s phone number containing a code, which he read out to the woman. This was actually a password reset code, and it granted her access to his bank account.
Next, the woman told him they needed to block his PIN, and asked what his PIN was. At this point he realized it was a scam, since no real bank should ask you for your PIN, and he hung up immediately.
In hindsight, the man believes he should have been more suspicious of the caller from the outset. “When I read that thread now, that’s one red flag after another,” he told CNN. “But it’s hard to express the social engineering component of it. My guard wasn’t up in the way it should’ve been.”
So how can you protect yourself?
- Find out what information your bank will and will not ever ask you for over the phone or via email.
- When you receive calls like this, tell them you can’t talk at that moment. Ask for a way to call them back later. Then hang up and call your bank directly to find out if it’s legitimate. You can also report the scammer’s phone number.
Top 3 Scams - October 1, 2019
 Amazon ‘Update Account’ Scam
Amazon ‘Update Account’ Scam
Bad guys are targeting Amazon customers, urgently claiming you need to update your information or your account will be permanently disabled. They count on you getting worried and acting quickly without thinking it through.
The phishing emails purport to be notifications from Amazon informing you that you need to update your information within twenty-four hours or your account will be permanently disabled.
When you click the “Update Now” button in the email, you’ll be taken to a convincing imitation of an Amazon login page. After entering your credentials, the phishing page will present a form for you to input your name, address, phone number, and date of birth. Next, you’ll be asked to provide your credit card and bank account information–all information you’ve probably given to Amazon before.
Finally, the phishing site informs you that your account has been recovered and says you’ll be automatically logged out. You are then redirected to the real Amazon website.
The email itself has several red flags like typos and bad grammar, but the worry people have about losing their Amazon accounts makes them click anyway.
How can you avoid this?
- Even if an email is perfect (no typos or strange grammar), leave the links alone and navigate to your accounts independently.
- Recognize when emails immediately make you feel fear or dread, and use that as a trigger to stop and think before you click.
 Watch Out for Fake Video Scams
Watch Out for Fake Video Scams
The bad guys are using social media messaging platforms and emails to send dangerous phishing links that are disguised as a link to a video. The scammers provoke you into clicking by asking, “Is this you in the video???”
Don’t fall for this.
They are counting on an impulsive emotional reaction. It’s important to note that these attacks almost never actually involve a video; they’re only creating a reason for you to click the malicious link.
What makes them especially dangerous is when they come through social media platforms, appearing as if from a friend or someone you know.
Stay safe with these tips:
- Be wary of these types of messages and any unexpected links…even when they appear to be from someone you know. Cybercriminals often hack social media accounts so they can send these messages to everyone connected to the stolen account.
- Remember to never click on a link you’re not expecting. Even when it’s from someone you know, call or find some other way to verify first. In the case of social media accounts, look and see if your connection has posted anything about having gotten hacked.
 Yahoo Settlement Scam
Yahoo Settlement Scam
Yahoo is close to reaching a $117.5 million settlement in a class-action lawsuit over a series of data breaches that affected users between 2012 and 2016 — and you could be eligible for a $100 check and/or free credit monitoring if you had an account during that period.
From 2012 through 2016, several hacks penetrated Yahoo systems and stole billions of records. While this settlement is not nearly as big as the $700 million settlement that credit agency Equifax agreed to for its 2017 data breach involving 147 million records, it’s still enough of a phish bait to deceive people into disclosing their personal information.
Yahoo is offering two years of free credit-monitoring services to anyone who had a compromised account, along with various refunds and up to $25,000 in out-of-pocket losses, if applicable. If you can verify that you already have credit-monitoring, then you can ask for a cash payment of $100.
Similar to scams surrounding the Equifax settlement, bad guys are using the “urgency” trick. Yahoo’s settlement is a set amount, meaning there’s only so much cash to go around, so if you’re going to make a claim, you’d better do it fast.
They are sending phishing attacks that look like they come from Yahoo. When you click on the links, you wind up on a fake website that looks like it’s Yahoo, but will try to steal your personal information. Don’t fall for it.
So how can you protect yourself?
- First, don’t be dazzled by the offer of “free money.” If you never had a Yahoo account, then simply delete and move on.
- If you were affected by the breach, find the proper settlement links online, independent of unsolicited emails like this.
- Always think before you click. Especially when receiving unexpected alerts or offers. Cybercriminals play on your emotions of excitement and fear to push you to act without thinking.
Top 3 Scams - September 1, 2019
 Unusual Sign-in Activity Scam
Unusual Sign-in Activity Scam
This one is tricky. It’s a phishing campaign that pretends to be an “Unusual sign-in activity” alert from Microsoft.
With companies such as Google and Microsoft commonly sending users alerts when unusual activity has been discovered on their account, you may feel it’s normal to receive them and click on the enclosed link without thinking about it. Attackers are capitalizing on this by sending emails that pretend to be “Microsoft account unusual sign-in activity” alerts.
When compared to the legitimate email notifications sent by Microsoft, the scam looks almost identical, with the same information fields and even the same sender address of “account-security-noreply@accountprotection.microsoft.com.” What’s different, though, is that when you click on the “Review recent activity” email link, instead of going to Microsoft to review your account’s sign-in activity, you are brought to a fake landing page on a non-Microsoft site that asks you to login.
When a victim enters their credentials, the information will be saved for the phishers to retrieve later so they can access that account whenever they want.
No matter what credentials are entered in the fake login form, the user will always be redirected to an error page on Microsoft’s live.com site. This is to make it look like there is a problem with your account and that nothing strange is going on.
How can you avoid this?
- Always check the From/sender address, but don’t always trust it. Email addresses can be easily spoofed.
- Pay close attention to the link when hovering over it before clicking as well as looking at the URL if you do click. Is it spelled correctly? Is it secure? Microsoft will always be an https: link.
- Try to stop yourself before clicking on the email link automatically. Think back to when and where the “unusual activity” may have been and whether you should have received the warning in the first place.
 Fortnite Hacks…or Hackers?
Fortnite Hacks…or Hackers?
This scam may be more geared toward your children, but with 250+ million Fortnite users worldwide, it’s worth sharing with everyone.
It’s a ransomware scam disguised as a game hack tool. The offer is a ‘cheat’ for better aim or to know the location of other players in the game. It is believed to appear as a link in the forums and that the ransomware gets installed when the tool is downloaded.
Upon activation, a timer appears on the screen, telling the player his or her files will be deleted if the ransom is not paid before time runs out. After the first two hours, everything in the photos folder will go. After another two hours, the desktop folder. After a third timer, the documents folder.
According to Cyren, the ransomware was still active on Fortnite as of August 21st.
Stay safe with these tips:
- Remind your children that cheaters never win. Just kidding. Who didn’t use codes and tricks to beat Atari or Nintendo games?
- Always be suspicious of downloads. Whenever possible, search for info about them online before choosing to install. Scams are often reported quickly to help others avoid falling victim.
 Take it to the Bank
Take it to the Bank
Financial phishing is getting even more popular.
Researchers at NormShield have released their State of Financial Phishing report that shows an increase in website domains that impersonate financial institutions registered so far this year, with thousands more expected.
That’s important because criminals are getting more savvy, setting up these sites and then waiting to use them. Their phishing attacks are more complex and targeted as well. They are copying actual bank promotions that link to their fake sites in order to steal your credentials and other sensitive information.
So how can you protect yourself?
- Always think before you click. Especially when receiving unexpected alerts or offers from what seems to be your financial institution. Cybercriminals play on your emotions of excitement and fear to push you to act without thinking.
- Contact your bank independently of the email. Open your own browser window to log in, or give them a call. Legitimate offers will be confirmed, and phishing attacks can be reported.
Top 3 Scams - August 1, 2019
 OneNote Audio Note Scam
OneNote Audio Note Scam
Phishing scammers are coming up with more innovative methods to convince their targets to provide login credentials. Such is the case with a new OneNote Audio Note phishing campaign that is currently underway.
Bleepingcomputer reports that “this campaign comes in the form of an email with the subject ‘New Audio Note Received’ and claims that you have received a new audio message from a contact in your address book.” In order to listen to the message, of course, you need to click on a link to listen to it.
Of particular interest is that the phishing scammers are now commonly including footer notes stating the email is safe as it was scanned by a security software. Along with the screenshots, it can look convincing. However, when you click on the “Listen to full message here” link, you will be brought to a fake OneNote Online page hosted on Sharepoint.com. This page states that “You have a new audio message” and then prompts you to click on a link to listen to it. And you will have given the scammers your Microsoft login information.
Remember the following to protect yourself from phishing attempts like this:
- Before clicking, hover over links to see where they are pointing. Never click on a link in a message unless you’re certain the sender is legitimate.
- For that matter, consider who is sending you this audio note. Do you use OneNote? Was this expected? If not, reach out to the supposed sender to check before clicking.
- Whenever you get an email from an online service you use, log in to your account through your browser, not through links in the email.
 More Government Impersonators
More Government Impersonators
The Federal Trade Commission has warned that complaints about scammers impersonating government agencies reached a record high this spring, with more than 46,000 complaints registered in May alone. The majority of these scams purported to come from the Social Security Administration (as I shared in May), but other popular choices for impersonation included the Health Department, the IRS, and various law enforcement agencies.
Most of the scams tried to obtain payment via gift cards, which the FTC says “is a dead giveaway that the consumer is dealing with a scammer.” Six percent of the people who reported the scams said they fell victim, with the median amount of money lost being $960.
The FTC states that the fraudsters use social engineering techniques that are very effective, but that can be easily recognized once someone knows what to look for. “The vast majority of people who report this type of scam say it started with a phone call, and these callers have their mind games down pat,” an FTC blog post said.
“Government impersonators can create a sense of urgent fear, telling you to send money right away or provide your social security number to avoid arrest or some other trouble. Or they can play the good guy, promising to help you get some free benefit like a grant or prize, or even a back brace. Scammers like to make the situation so immediate that you can’t stop to check it out.”
It’s worth keeping in mind that these numbers only reflect the scams that were reported, so the actual number of attempted scams is probably much higher. Providing new-school security awareness training is one of the best ways for organizations to ensure that their employees can resist all types of social engineering.
Stay safe with these tips:
- Pay attention when you get a call out of the blue. If it’s a legitimate government agency, you should be able to get a phone number, possibly a case or account ID, and other ways to verify before sharing your information.
- Remember that payment via gift card should always be a red flag.
- Check online or contact the official agency yourself before taking any action from a call like this.
 Don’t Be Fooled by the File Type
Don’t Be Fooled by the File Type
Be on the lookout for a brand new phishing attachment. The bad guys are using a different type of file to trick you, and it could reach your inbox.
They’re sending phishing emails with SHTML file attachments (.shtml extension). These types of files are typically used on web servers and may not always be caught by spam filters.
If you “open” this attachment, you’ll be brought to a dangerous website that requests sensitive information.
So how can you avoid this?
- Always check the details, such as file type, on an attachment you weren’t expecting. If you see .shtml, consider whether that makes sense.
- Never click on an unexpected attachment. Call to confirm with the sender first.
Top 3 Scams - July 1, 2019
 Brand Impersonation Attacks are at an All-time High
Brand Impersonation Attacks are at an All-time High
According to recent reports, phishing attacks that use brand impersonation are at an all-time high. Cyber criminals are posing as familiar companies so they can trick you and get access to your account in order to steal sensitive data or target additional employees.
Here’s how it typically happens:
Attackers send you a standard-looking email appearing to be from a service or company that you use, such as Office 365. In one example, the subject may be a warning about your files getting deleted. Clicking the link in the email will take you to a fake (but very realistic) login page. The most deceiving part of some of these fake pages is that the web address appears to be safe.
The URL may end with a legitimate domain like “windows.net,” because the bad guys are hosting these pages with Microsoft’s Azure cloud services. But if you enter your information here, the bad guys will gain access to one or more of your accounts which they can use to steal data or plan further attacks on your organization.
Remember the following to protect yourself from brand impersonations:
- Look carefully at the domain in sender addresses. Does it say “microsoft.com” or “micronsoft.com”?
- Before clicking, hover over links to see where they are pointing. Never click on a link in a message unless you’re certain the sender is legitimate.
- Whenever you get an email from an online service you use, log in to your account through your browser, not through links in the email.
 Beware of Voicemail Phishing Scams
Beware of Voicemail Phishing Scams
If your organization uses online voicemail services, you’ve probably used links in notification emails to check your new messages. Lately, scammers are creating look-alike notification messages that trick you into giving up your login credentials.
The fake voicemail notification takes you through a series of steps. First it will prompt you to click a link to listen to your “new message.” Then, you’re directed to a web page containing another link to click on so you can finally hear your new message.
If you click these links, you’ll be brought to a realistic-looking Microsoft sign-in page where you’re prompted for your email and password. If you enter your login details here, the bad guys will have full access to your account, where they can steal sensitive data or perform further attacks on your organization.
Stay safe with these tips:
- If you’re already logged into your email account, you shouldn’t be prompted to log in again. So if you see a new login page, question it.
- Before clicking, hover over links to see where they’re taking you. When asked to log in to an online service, type the web address into your browser rather than using links in the unexpected email.
- Get familiar with the format of your voicemail notification emails. If you’re ever in doubt, contact the proper department in your organization before clicking on any links or downloading any attachments.
 Google Calendar Meeting Scams
Google Calendar Meeting Scams
The bad guys are using unsolicited Google Calendar notifications now to trick users into clicking malicious links.
Here’s how it works:
Scammers send a Google user a calendar invite complete with meeting topic and location information. Inside the details of the appointment lies a malicious link that looks like it’s pointing you back to ‘meet.google.com’ for more details. If you click on it, however, typical tactics will be employed to try to infect your machine with malware and so on.
This kind of attack has a massive attack surface, given the number of people utilizing Google’s Calendar service, i.e., millions. It also has contextual appeal by being hidden within a meeting invite and uses a seemingly valid URL for more information.
So how can you avoid this?
- Stop and think before clicking on any unexpected meeting requests. Do you know the sender? Does the subject make sense?
- Hover over the link before clicking. If it looks legitimate but you still have a bad feeling, trust your gut. Reach out to the sender through a separate email or phone call.
Top 3 Scams - June 1, 2019
 Surprise, You’re Getting Sued
Surprise, You’re Getting Sued
A very effective email phishing and malware attack has come out disguised as a nastygram from a law firm. The scam typically notifies you that you’re being sued, and it instructs you to review the attached file and respond within a few days — or else. The kicker? The attached Word documents are booby-trapped with a trojan used to drop malware on your computer.
This scam was discovered as part of a phishing kit. That’s right, there are ready-made kits hackers can purchase, customize, and put in play. It has some spelling mistakes and awkward grammar that might tip off the vigilant reader, but what’s troubling is how the phishing kit included five booby-trapped Microsoft Word docs to choose from, and none of those files were detected as malicious by more than three of the five dozen or so antivirus products that scanned the Word docs on May 22, ten whole days after they were spammed out.
Also of concern? A legitimate law firm was spoofed in this attack. According to reports, someone had recently called them to complain about a phishing scam, but beyond that the firm didn’t have any knowledge of the matter.
So aside from putting your own lawyer on speed dial, what can you do to avoid this scam?
- Anytime an unsolicited email evokes a strong emotion (such as fear), stop and think before you click. Look up the law firm online, and call them. Do not click on any links or use any contact information in the message.
- Try to remember that legal proceedings typically require serving papers in person, through the mail, or even by putting a notice in the newspaper.
- Never open attachments you aren’t expecting, especially from people you don’t know.
 Customer Service, How May I Rob You?
Customer Service, How May I Rob You?
In this new age of social media customer service, scammers are seeing opportunity.
As digital giants like Twitter and Facebook scramble to keep up with fake news and fake accounts, some are bound to slip through. So when you want to make a complaint about goods or services and get some sort of fast and public resolution, use caution.
It works like this: you tweet to the company about being overbilled or missed delivery, etc. A very similarly named account that may include “CS” or some customer service variation responds to you.
They’ll ask for basic information such as name, address, and account number or login. But then there’s ‘trouble locating your account’ so further information is requested. This may be your date of birth and phone number.
Once they have your phone number, they call posing as the company and can request even more personal information in a seemingly reasonable way. This may include the bank account you use to pay that company and possibly some security questions for “verifying.”
You’re happy to do whatever it takes to get resolution to your problem, so you may not realize that you’ve now handed over the keys to your entire bank account and login details that can be sold on the Dark Web.
This very scam was used in England to wipe out a woman’s bank account and take out multiple loans in her name. So what can you do, especially when it seems that a public complaint is the only way to get some attention?
- Check to see if the account is verified on Twitter or Facebook or whatever social platform you’re using. Not all businesses will be verified, but large corporations typically are.
- Visit the company’s website to find out the account(s) they use for customer service. Look at their contact page or hover over their social media icons to see their official handles.
- Limit your exposure by submitting complaints through the company’s chat or email system, and leave social media for more social pursuits.
 Holiday Hacking
Holiday Hacking
The bad guys are known to use holidays such as Memorial Day to try to get you to click on a dangerous link or download a malicious attachment. They can pose as charities asking for donations, especially for veterans on this holiday, and they often mimic sales from major retailers. These scams will probably crop up again for the Fourth of July.
Whether you’re traveling for the holiday weekend or staying home to take advantage of online shopping deals, be cautious when performing any types of online transactions. Be suspicious of any out-of-the-ordinary emails, and be mindful of what information you’re sharing over your phone when you’re on the road.
- If you’re being asked for donations and it’s not a company you have given to before, navigate to the company’s website independently. Do not click on any of the links in the message.
- If you receive an incredible deal or offer in your inbox, visit the website independently. Private offers may not be listed publicly, so if you don’t see the deal, call the company before clicking any links in the email.
- If you’re traveling, remember to turn off your mobile device’s Bluetooth when not in use. Cyber criminals can pair with your phone’s open Bluetooth connection and steal personal information.
Top 3 Scams - May 1, 2019
 SSN Robocall Scams
SSN Robocall Scams
Be on the lookout for a popular robocall scam that is tricking people into believing their Social Security number (SSN) has been suspended.
The robocall tells you to call the number provided to speak with a government agent about the issue. Some of the robocalls even threaten to issue an arrest warrant if the victim doesn’t respond.
When you call the number back, you are actually speaking with a fake government agent. This scammer will try to trick you into giving up sensitive personal information like your SSN, birth date, and bank account number.
Always remember the following to stay safe from tricks like this:
- Your Social Security Number can never be suspended.
- The Social Security Administration will never threaten to arrest anyone.
- You should not share any personal information with someone you don’t know over the phone.
- If you get this type of call, hang up immediately and report the call to the appropriate agency.
 PDFs as Phishbait
PDFs as Phishbait
The use of malware-laden PDF email attachments has spiked in recent months, internet security company SonicWall has found. Over the course of 2018, SonicWall detected 47,000 new attack variants using PDFs, while they observed more than 73,000 of these variants last month alone. 67,000 of these PDFs linked to scammers, while 5,500 contained links to malware downloads.
John Oates at the Register writes, “Other attacks have been known to nick login details by tricking the user into opening malicious PDFs that use remote document loading mechanisms to capture and leak your credentials.”
Most of the attacks observed by SonicWall simply used PDFs to smuggle malicious links through email security filters. Many security filters struggle to analyze content inside PDFs, so an attacker stands a better chance of getting through to their victim if they place the link in one of these files.
SonicWall notes that PDFs are generally thought of as a safe file type, so users often don’t hesitate to open them. Given the pervasiveness of PDFs within corporate and government environments, employees need to know how to avoid these attacks.
How to protect yourself:
- If you receive a message with an attachment from someone you don’t know, do not open the attachment. Even if it’s a pdf.
- Never click on a link in a message or in an attachment unless you know the sender is legitimate.
- If you think the message is okay, always hover over links to see where they are taking you. If you’re unsure, don’t click!
 Fake Emails from HR
Fake Emails from HR
The bad guys know how easy it is to trick you with emails that spoof–or appear to come from–your Human Resources team. These attacks are everywhere right now.
The emails are often centered around topics such as “new” or “updated” policies, employee benefits, employee handbooks, payroll, and W-2 information.
Whenever you receive an email from your HR team, you may feel compelled to open the email and address it right away. The sense of authority that comes with HR emails is how the bad guys trick you. They’re counting on you falling victim to this sense of authority so you end up clicking before you think
If you receive an unexpected email appearing to come from your HR team, or an HR-related service, always remember the following:
- Pick up the phone and speak with someone who can confirm the request is valid BEFORE you click on any links or download any attachments.
- Log in to the HR-related service account through your browser (not through links in the email) to check the validity of the information in the email.
- If it’s a scam, immediately report the message to your IT team and your HR department.
Top 3 Scams - April 1, 2019
 Robocall Scams
Robocall Scams
Bad actors are automating robocall scams worldwide. Recently, there has been a rise in this type of fraud. They have a variety of attacks that you should watch out for.
Here are a few examples:
- Bank account and credit card scams where the bad guy claims to be an official from your bank or credit card company
- Extortion scams where they request payment for a kidnapped friend or family member
- Callback scams where you are tricked into calling back a very expensive international number
Always be suspicious when a company calls you requesting action right then over the phone. Legitimate businesses will typically contact you via email or by letter to notify you of issues with your account and inform you of any corrective steps.
If you receive a call from a company urging you to complete a request, politely get off the phone and then call the company directly to investigate. Scammers can spoof any number they like, so even if it looks legitimate, it can be fake.
Never provide personal information over the phone unless you’re the one who initiated the call.
Consider getting on the national Do Not Call registry. The FTC allows you to report numbers that do not comply after you’ve been on the list for 31 days. You can also report robocalls whether or not you are on the list.
 Malware thru Messaging Apps
Malware thru Messaging Apps
As if email and phone calls aren’t enough, bad actors are using popular messaging apps to trick you into downloading malware. These scammers know you’re used to looking out for suspicious emails, so they’re hoping to catch you off guard in the messaging apps you may use.
The attack is simple: The bad guys send a malicious link in apps such as Skype and Facebook Messenger. If you click on this link, a complex attack begins and you’re left with a ransomware-infected machine.
Don’t fall for this messaging scam!
If you receive a suspicious message from someone you don’t know, don’t even open it.
Never click on a link in a message unless you know the sender is legitimate.
If you think the message is okay, always hover over links to see where they are taking you. If you’re unsure, don’t click!
 Child P0rn Phishing Attack
Child P0rn Phishing Attack
This new blackmail/sextortion scam is pure evil.
You get an email that claims the CIA is about to bust you for child p*rn unless you pay 5,000 dollars to have the sender delete your records. It includes a case number and (fast-approaching) fictional arrest date.
What makes this especially dangerous, even for those who know they have never looked at anything being described, is that there is a link you might be tempted to click for information, whether out of shock, fear, or curiosity.
That link, once clicked, will install the very materials they claim you’re going to get arrested for and will add related searches to your browsing history. Then they notify the authorities about you!
Always resist the urge to click when it is strongest. Any message that scares you that much or makes you so angry is most likely an attempt to override your logic and good sense.
Immediately report such a message to your IT team.
Top 3 Scams - March 1, 2019
 Tech Support Scans
Tech Support Scans
You’re browsing online. The attack usually goes like this: First, you receive a fake Windows Alert pop-up message claiming “Your PC might be infected” and to “click OK to do a quick 10-second scan.”
When you click OK, a very realistic-looking, but very fake, ”system scan” runs within your browser. The scan looks almost identical to your antivirus software’s real system scans.
Once the “scan” ends, you’re told that your PC is indeed infected and that you need to download and install an update to the antivirus software. Don’t do it! This “update” is actually an unwanted application that will install onto your computer.
Never trust internet pop-ups. They often use scare tactics to get you to call a number for tech support or download an application to “fix” the problem.
Go to your IT administrator (if at work) or a reputable computer repair company (if at home) if you think something is wrong with your computer.
 Dangerous Office Attachments Bypassing Email Security
Dangerous Office Attachments Bypassing Email Security
As always, be suspicious of email attachments because attackers are finding new ways to get around email security filters. The latest attack includes Microsoft Office attachments containing hyperlinks to dangerous websites.
If you unknowingly download one of these attachments and click on a link from within the document, you will be brought to a malicious website that steals your sensitive information. This particular attack is usually carried out with Microsoft Word attachments, but dangerous links are certainly not limited to files with .docx file extensions. This attack could occur with almost any file type.
Remember the following to prevent this type of attack from happening to you:
- Never open attachments from people you don’t know.
- Don’t open any attachment unless you have asked for it or have verified with the sender (through a channel other than email) that it is legitimate.
- Before clicking on any link in an email or email attachment, hover over it to see where it will take you.
 Bogus Job Offers
Bogus Job Offers
This one is tricky. A series of phishing campaigns are targeting companies in various industries with phony job offers using direct messages on LinkedIn, according to researchers at Proofpoint.
The attacker initially makes contact by sending an invitation to the target on LinkedIn with a short message regarding a job opportunity.
Within a week after the target accepts the invitation, the attacker will send a follow-up email with either a link or a PDF attachment that contains embedded URLs.
These links take the target to a spoofed version of a real staffing service, which forces the download of either a Word document or a JScript loader. This document or loader will result in the installation of a JScript backdoor known as “More_eggs” which can then install malware or be used to gather information from the machine.
You expect strangers to reach out to you about jobs on LinkedIn, so you’ve got to be incredibly vigilant to avoid this.
- Do some independent research on the supposed offer.
- If you can’t find out about the company or position, Google the person contacting you.
- Look very carefully at the staffing service site you’re directed to. Make sure there are no tricky spellings in the URL or missing or strange information in the rest of the website.
- Remember to always be suspicious of downloads.
Top 3 Scams - February 1, 2019
 CEO Fraud
CEO Fraud
The bad guys are getting creative with CEO Fraud and gift card scams. This particular campaign involves a bad guy impersonating one of your executives, and then asking you to buy gift cards for customers. They even allow the employee to take one for themselves (how generous!). The unknowing employee is instructed to go to the store and physically buy the cards, then email or text the gift card numbers to “the boss.”
Try to think of gift cards like cash, and never blindly comply with a request like this. Call the supposed sender directly to determine whether the request is valid or a scam. Sometimes it’s OK to say “no” to the CEO!
 False File Hosting
False File Hosting
Bad actors have come up with another way to trick you. Now they are using sites like Dropbox, Google Drive, and other file hosting sites for their evil attacks.
They put a malicious file on these sites, and they use that site to send you an invite to log in and open/click on that infected file. The invites look legit because they are. They really came from that site and are identical to the normal invites. So what to look out for?
- Email invites to open a shared file somewhere in the cloud that you did not ask for.
- Emails that require you to log into a site to see something important. Don’t enter anything.
Always be suspicious of links in emails that you did not expect or did not ask for. If you decide to log into a file sharing site like Dropbox, enter the address in your browser or use a bookmark you set yourself earlier.
 Tax Time
Tax Time
The IRS saw nearly double the number of tax-related scam incidents in 2018 compared to 2017. Watch out for scams claiming to be from the IRS or from tax firms. These emails purporting to come from the IRS demand a payment or threaten to seize the recipient’s tax refund. Those involving tax firms seek to solicit personal, tax, or financial information. Similar scams target employers by impersonating employees.
The IRS suggests the following steps to avoid becoming a victim of phishing:
- Be Vigilant – Employers and businesses providing tax services can best protect themselves from phishing attacks by educating employees with Security Awareness Training. Employees are trained on phishing tactics in order to heightened their sense of security, making it easier to spot a malicious email and avoid becoming a victim.
- Use Security Software – The use of email, web, and DNS scanning solutions can reduce the number of potentially malicious messages that reach an Inbox.
- Use Strong Passwords – Make unique, complex passwords for each account used.
- Use Multi-Factor Authentication – When available, use MFA to better secure access to online applications, websites, and data.
Emails impersonating the IRS can be forwarded to phishing@irs.gov.
Protect yourself and your network.
Think Before You Click.